系统 : Windows xp
程序 : vcrkme01
程序下载地址 :http://pan.baidu.com/s/1mh1n33y
要求 : 爆破
使用工具 :OD
可在“PEDIY CrackMe 2007”中查找关于此程序的破文,标题为“标志位法爆破实例”。
OD载入程序根据字串提示找出关键算法:
00401223 . 68 FF000000 push 0FF ; /Count = FF (255.)
00401228 . 68 30694000 push 00406930 ; |Buffer = vcrkme01.00406930
0040122D . 68 E8030000 push 3E8 ; |ControlID = 3E8 (1000.)
00401232 . 50 push eax ; |hWnd => 00490736 ('[v0!d] Crackme - v0.01',class='#32770')
00401233 . FFD6 call esi ; GetDlgItemTextA
00401235 . 8B0D 28694000 mov ecx, dword ptr [406928]
0040123B . 68 FF000000 push 0FF ; /Count = FF (255.)
00401240 . 68 306A4000 push 00406A30 ; |Buffer = vcrkme01.00406A30
00401245 . 68 EA030000 push 3EA ; |ControlID = 3EA (1002.)
0040124A . 51 push ecx ; |hWnd => 00490736 ('[v0!d] Crackme - v0.01',class='#32770')
0040124B . FFD6 call esi ; GetDlgItemTextA
0040124D . 68 306A4000 push 00406A30
00401252 . 68 30694000 push 00406930
00401257 . E8 A4FDFFFF call 00401000
0040125C . 83C4 08 add esp, 8
0040125F . 83F8 01 cmp eax, 1 ; eax 是否为1?
00401262 . A3 646C4000 mov dword ptr [406C64], eax
00401267 75 65 jnz short 004012CE ; 不是则跳转出错
00401269 . 8B15 28694000 mov edx, dword ptr [406928]
0040126F . 6A 40 push 40 ; /Style = MB_OK|MB_ICONASTERISK|MB_APPLMODAL
00401271 . 68 80604000 push 00406080 ; |good job! - cracked!
00401276 . 68 50604000 push 00406050 ; |send your solution to : v0id2k1@hotmail.com
0040127B . 52 push edx ; |hOwner => 00490736 ('[v0!d] Crackme - v0.01',class='#32770')
0040127C . FF15 C4504000 call dword ptr [<&USER32.MessageBoxA>>; MessageBoxA
这里F7进入标志eax的子程序:
00401183 8B5424 14 mov edx, dword ptr [esp+14] ; 对edx的最后一次赋值
00401187 B9 40000000 mov ecx, 40
0040118C |. 33C0 xor eax, eax
0040118E |. BF 446B4000 mov edi, 00406B44
00401193 |. F3:AB rep stos dword ptr es:[edi]
00401195 |. 5F pop edi
00401196 |. 5E pop esi
00401197 |. 5D pop ebp
00401198 8BC2 mov eax, edx ; 最后将edx的值传入标志eax
0040119A 5B pop ebx
0040119B C3 retn
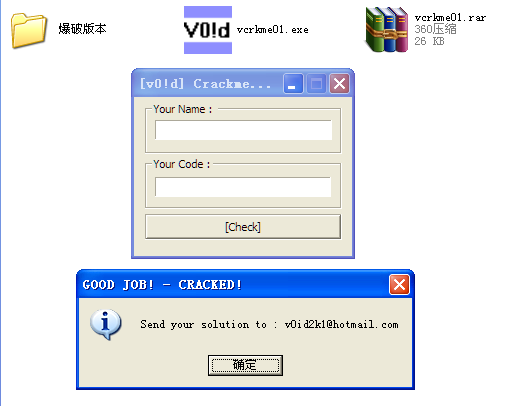
程序最后对eax的值进行了设置,我们也在最后将赋值的指令(地址401198)改成:
inc eax
效果如下:
-------------------------------------------------------------------------------------------------------------------
分析标志eax的子程序:
00401000 /$ 53 push ebx
00401001 |. 8B5C24 0C mov ebx, dword ptr [esp+C]
00401005 |. 55 push ebp
00401006 |. 56 push esi
00401007 |. 8B7424 10 mov esi, dword ptr [esp+10]
0040100B |. 8A0B mov cl, byte ptr [ebx] ; 取出密钥首字符
0040100D |. 33ED xor ebp, ebp
0040100F |. 57 push edi
00401010 |. 8A06 mov al, byte ptr [esi] ; 取出用户名首字符
00401012 |. 3AC1 cmp al, cl ; 首字符是否相同?
00401014 |. 0F85 69010000 jnz 00401183 ; 不同则注册失败
0040101A |. 8BFE mov edi, esi
0040101C |. 83C9 FF or ecx, FFFFFFFF
0040101F |. 33C0 xor eax, eax
00401021 |. F2:AE repne scas byte ptr es:[edi]
00401023 |. F7D1 not ecx
00401025 |. 49 dec ecx ; 求用户名子串长度
00401026 |. 83F9 05 cmp ecx, 5 ; 长度低于5?
00401029 |. 0F82 54010000 jb 00401183 ; 低于则注册失败
0040102F |. 807B 01 2D cmp byte ptr [ebx+1], 2D ; 密钥第二个字符是-吗?
00401033 |. 0F85 4A010000 jnz 00401183 ; 不是则注册失败
00401039 |. 8BFE mov edi, esi
0040103B |. 83C9 FF or ecx, FFFFFFFF
0040103E |. 33C0 xor eax, eax
00401040 |. 33D2 xor edx, edx
00401042 |. F2:AE repne scas byte ptr es:[edi]
00401044 |. F7D1 not ecx
00401046 |. 49 dec ecx ; 求用户名子串长度
00401047 |. 74 17 je short 00401060 ; 并没有什么卵用的jump
00401049 |> 0FBE0C32 /movsx ecx, byte ptr [edx+esi] ; 循环迭代用户名字符串
0040104D |. 03E9 |add ebp, ecx ; 累加
0040104F |. 8BFE |mov edi, esi
00401051 |. 83C9 FF |or ecx, FFFFFFFF
00401054 |. 33C0 |xor eax, eax
00401056 |. 42 |inc edx ; 循环变量自增
00401057 |. F2:AE |repne scas byte ptr es:[edi]
00401059 |. F7D1 |not ecx
0040105B |. 49 |dec ecx ; 求用户名子串长度
0040105C |. 3BD1 |cmp edx, ecx ; 是否迭代完毕?
0040105E |.^ 72 E9 jb short 00401049
00401060 |> 81C5 64600000 add ebp, 6064 ; 累加结果加上0x6064
00401066 |. 55 push ebp
00401067 |. 68 34604000 push 00406034 ; ASCII "%lu"
0040106C |. 68 306B4000 push 00406B30 ; ASCII "25215"
00401071 |. E8 B6030000 call 0040142C ; 将数值转换成 对应的无符号长整形 ”字符串“
00401076 |. 8A16 mov dl, byte ptr [esi] ; 取出用户名首字符
00401078 |. 8BFE mov edi, esi
0040107A |. 83C9 FF or ecx, FFFFFFFF
0040107D |. 33C0 xor eax, eax
0040107F |. 8815 446B4000 mov byte ptr [406B44], dl ; 保存用户名首字符
00401085 |. C605 456B4000>mov byte ptr [406B45], 2D ; 添上-字符
0040108C |. F2:AE repne scas byte ptr es:[edi]
0040108E |. F7D1 not ecx
00401090 |. 49 dec ecx ; 求用户名子串长度
00401091 |. 0FBE4431 FF movsx eax, byte ptr [ecx+esi-1] ; 取用户名子串尾字符
00401096 |. 50 push eax ; 入栈
00401097 |. E8 C4020000 call 00401360 ; 小写转大写
0040109C |. A2 466B4000 mov byte ptr [406B46], al ; 添入大写字符
004010A1 |. BF 306B4000 mov edi, 00406B30 ; ASCII "25215"
004010A6 |. 83C9 FF or ecx, FFFFFFFF
004010A9 |. 33C0 xor eax, eax
004010AB |. F2:AE repne scas byte ptr es:[edi]
004010AD |. F7D1 not ecx
004010AF |. 2BF9 sub edi, ecx
004010B1 |. 81C5 64600000 add ebp, 6064 ; 循环结果再加上0x6064
004010B7 |. 8BF7 mov esi, edi
004010B9 |. 8BD1 mov edx, ecx
004010BB |. BF 446B4000 mov edi, 00406B44 ; ASCII "p-"
004010C0 |. 83C9 FF or ecx, FFFFFFFF
004010C3 |. F2:AE repne scas byte ptr es:[edi]
004010C5 |. 8BCA mov ecx, edx
004010C7 |. 4F dec edi
004010C8 |. C1E9 02 shr ecx, 2 ; 逻辑右边移动两位
004010CB |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi] ; 添上长整形字符串1
004010CD |. 8BCA mov ecx, edx
004010CF |. 55 push ebp
004010D0 |. 83E1 03 and ecx, 3
004010D3 |. 68 34604000 push 00406034 ; ASCII "%lu"
004010D8 |. F3:A4 rep movs byte ptr es:[edi], byte ptr [esi] ; 添上长整形字符串2
004010DA |. BF 30604000 mov edi, 00406030
004010DF |. 83C9 FF or ecx, FFFFFFFF
004010E2 |. F2:AE repne scas byte ptr es:[edi]
004010E4 |. F7D1 not ecx
004010E6 |. 2BF9 sub edi, ecx
004010E8 |. 68 306B4000 push 00406B30 ; ASCII "25215"
004010ED |. 8BF7 mov esi, edi
004010EF |. 8BD1 mov edx, ecx
004010F1 |. BF 446B4000 mov edi, 00406B44 ; ASCII "p-"
004010F6 |. 83C9 FF or ecx, FFFFFFFF
004010F9 |. F2:AE repne scas byte ptr es:[edi] ; 求贴好的序列号子串长度
004010FB |. 8BCA mov ecx, edx
004010FD |. 4F dec edi
004010FE |. C1E9 02 shr ecx, 2
00401101 |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi]
00401103 |. 8BCA mov ecx, edx
00401105 |. 83E1 03 and ecx, 3
00401108 |. F3:A4 rep movs byte ptr es:[edi], byte ptr [esi]
0040110A |. E8 1D030000 call 0040142C ; 将数值转换成 对应的无符号长整形 ”字符串“
0040110F |. BF 306B4000 mov edi, 00406B30 ; ASCII "25215"
00401114 |. 83C9 FF or ecx, FFFFFFFF
00401117 |. 33C0 xor eax, eax
00401119 |. 83C4 1C add esp, 1C
0040111C |. F2:AE repne scas byte ptr es:[edi]
0040111E |. F7D1 not ecx
00401120 |. 2BF9 sub edi, ecx
00401122 |. 8BF7 mov esi, edi
00401124 |. 8BD1 mov edx, ecx
00401126 |. BF 446B4000 mov edi, 00406B44 ; ASCII "p-"
0040112B |. 83C9 FF or ecx, FFFFFFFF
0040112E |. F2:AE repne scas byte ptr es:[edi]
00401130 |. 8BCA mov ecx, edx
00401132 |. 4F dec edi
00401133 |. C1E9 02 shr ecx, 2
00401136 |. F3:A5 rep movs dword ptr es:[edi], dword ptr [esi] ; 添上长整形字符串3
00401138 |. 8BCA mov ecx, edx
0040113A |. 8BC3 mov eax, ebx
0040113C |. 83E1 03 and ecx, 3
0040113F |. F3:A4 rep movs byte ptr es:[edi], byte ptr [esi] ; 添上长整形字符串4
00401141 |. BE 446B4000 mov esi, 00406B44 ; ASCII "p-"
00401146 |> 8A10 /mov dl, byte ptr [eax] ; 循环迭代密钥
00401148 |. 8A1E |mov bl, byte ptr [esi] ; 循环迭代序列号
0040114A |. 8ACA |mov cl, dl
0040114C |. 3AD3 |cmp dl, bl ; 是否相同?
0040114E |. 75 25 |jnz short 00401175
00401150 |. 84C9 |test cl, cl ; 是否为0?
00401152 |. 74 16 |je short 0040116A ; 是则结束循环
00401154 |. 8A50 01 |mov dl, byte ptr [eax+1] ; 循环迭代密钥
00401157 |. 8A5E 01 |mov bl, byte ptr [esi+1] ; 循环迭代序列号
0040115A |. 8ACA |mov cl, dl
0040115C |. 3AD3 |cmp dl, bl ; 是否相同?
0040115E |. 75 15 |jnz short 00401175
00401160 |. 83C0 02 |add eax, 2
00401163 |. 83C6 02 |add esi, 2
00401166 |. 84C9 |test cl, cl
00401168 |.^ 75 DC jnz short 00401146
0040116A |> 33C0 xor eax, eax ; 清空eax
0040116C |. 33D2 xor edx, edx ; 清空edx
0040116E |. 85C0 test eax, eax
00401170 |. 0F94C2 sete dl ; dl为1
00401173 |. EB 12 jmp short 00401187
00401175 |> 1BC0 sbb eax, eax ; eax=ffffffff
00401177 |. 83D8 FF sbb eax, -1
0040117A |. 33D2 xor edx, edx
0040117C |. 85C0 test eax, eax
0040117E |. 0F94C2 sete dl ; dl为0
00401181 |. EB 04 jmp short 00401187
00401183 |> 8B5424 14 mov edx, dword ptr [esp+14]
00401187 |> B9 40000000 mov ecx, 40
0040118C |. 33C0 xor eax, eax
0040118E |. BF 446B4000 mov edi, 00406B44 ; ASCII "p-"
00401193 |. F3:AB rep stos dword ptr es:[edi] ; 清空序列号
00401195 |. 5F pop edi
00401196 |. 5E pop esi
00401197 |. 5D pop ebp
00401198 |. 8BC2 mov eax, edx ; eax取edx的值
0040119A |. 5B pop ebx
0040119B . C3 retn
那么长的代码段实现的功能却是很简单,我们动手实现一下注册机。
我们直接打开之前搭建的框架,并修改OnBtnDecrypt函数如下:
void CKengen_TemplateDlg::OnBtnDecrypt()
{
// TODO: Add your control notification handler code here
CString str;
GetDlgItemText( IDC_EDIT_NAME,str ); //获取用户名字串基本信息。
int len = str.GetLength();
if ( len != 0 ){ //格式控制。
unsigned int sum = 0;
for ( int i = 0 ; i != len ; i++ ) //循环累加
sum += str[i];
sum += 0x6064;
//转化大小写
if ( (str[len-1] >= 0x61) && (str[len-1] <= 0x7A) )
str.SetAt( len-1,str[len-1] - 0x20 );
CString PassWord;
PassWord.Format( "%c-%c%lu-%lu",str[0],str[len-1],sum,sum+0x6064 );
SetDlgItemText( IDC_EDIT_PASSWORD,PassWord );
}
else
MessageBox( "用户名格式错误!" );
}
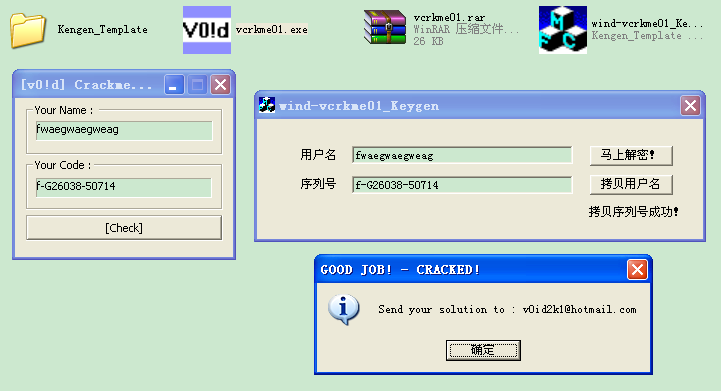
再在OnInitDialog中添加此代码修改标题:SetWindowText(_T("wind-vcrkme01_Keygen"));
运行效果: