背景
使用lcx也好,nc也好,总是会被安全防护软件查杀,所以想着自己写一个。顺面学习一下,端口转发的原理。
端口转发的逻辑
端口转发的逻辑很简单开启两个scoket,一个绑定IP端口进行listen,一个连接被转发的内网服务的IP和端口,使用select循环检测,转发信息。
代码
# -*- coding:utf-8 -*-
import os
import select
import socket
from optparse import OptionParser
class PortMap(object):
def __init__(self, laddr, lport, raddr, rport):
self.server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self._server = None
self.laddr = laddr
self.lport = lport
self.raddr = raddr
self.rport = rport
def run(self):
try:
self.server.bind((self.laddr, self.lport))
self.server.listen(1)
except Exception, reason:
print "Create Listen Port Failed!"
exit(0)
self.rlist = [self.server]
self.wlist = []
self.elist = [self.server]
while True:
rs, ws, es = select.select(self.rlist, self.wlist, self.elist)
for sockfd in rs:
if sockfd == self.server:
self._server, addr = sockfd.accept()
self.rlist.append(self._server)
try:
self.client.connect((self.raddr, self.rport))
except Exception, reason:
print "Connect Source Port Failed!"
exit(0)
self.rlist.append(self.client)
self.elist.append(self.client)
continue
elif sockfd == self._server:
data = sockfd.recv(4096)
self.client.send(data)
elif sockfd == self.client:
data = sockfd.recv(4096)
self._server.send(data)
if __name__ == "__main__":
optParser =OptionParser ()
optParser .add_option ('-R','--raddr',dest ='raddr')
optParser .add_option ('-l','--laddr',dest ='laddr')
optParser .add_option ("-P","--rport",dest ="rport")
optParser .add_option ("-p","--lport",dest ="lport")
options ,args =optParser .parse_args ()
maper = PortMap(options.laddr,int(options.lport),options.raddr,int(options.rport))
mapert.run()
使用
python portmap.py -l 127.0.0.1 -p 4444 -R 172.16.204.137 -P 22
或者编译后
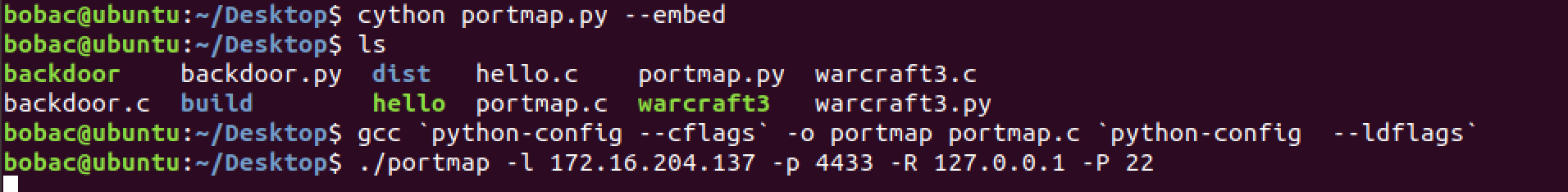
bobac@ubuntu:~/Desktop$ cython portmap.py --embed
bobac@ubuntu:~/Desktop$ ls
backdoor backdoor.py dist hello.c portmap.py warcraft3.c
backdoor.c build hello portmap.c warcraft3 warcraft3.py
bobac@ubuntu:~/Desktop$ gcc `python-config --cflags` -o portmap portmap.c `python-config --ldflags`
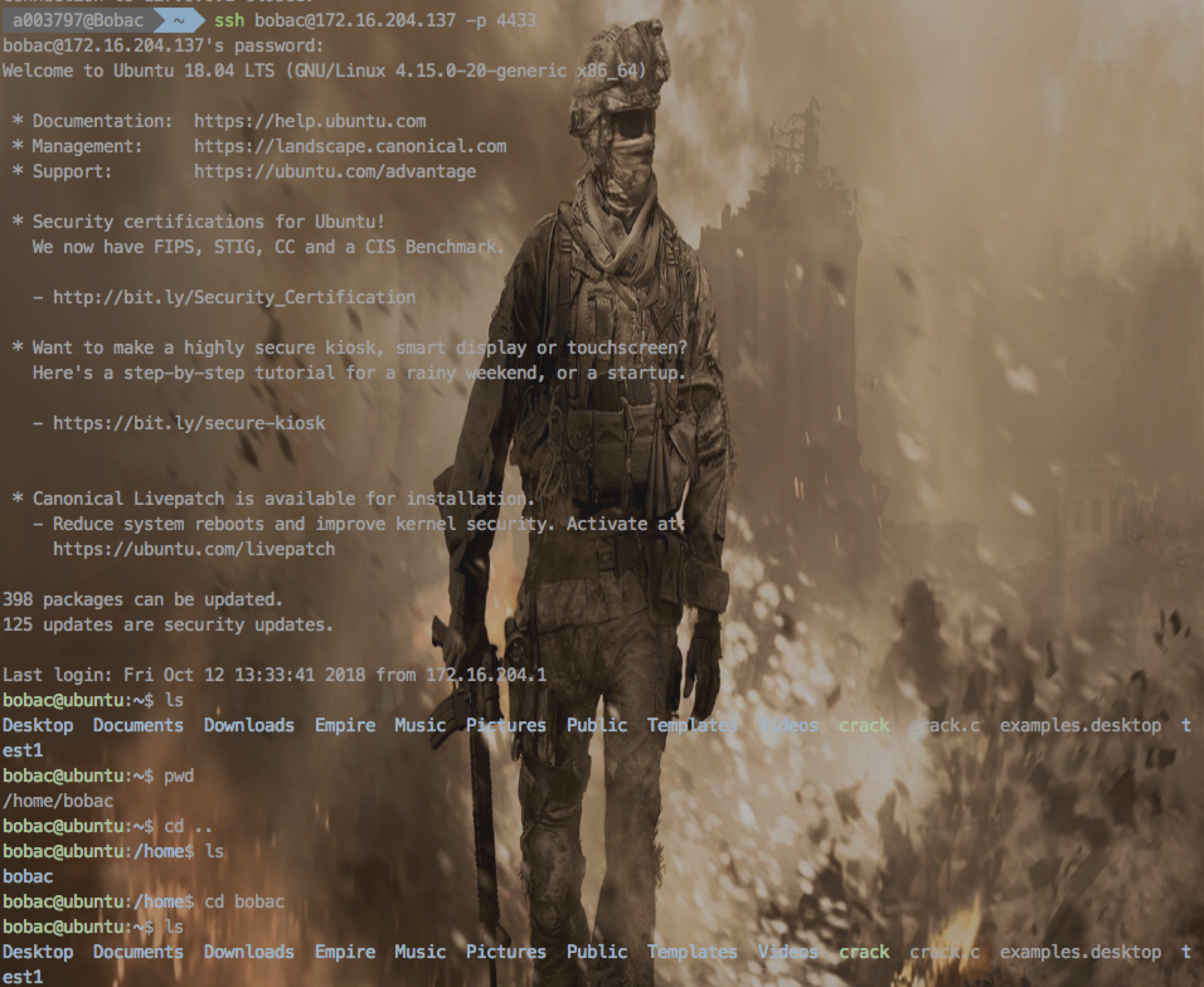
bobac@ubuntu:~/Desktop$ ./portmap -l 172.16.204.137 -p 4433 -R 127.0.0.1 -P 22
效果图
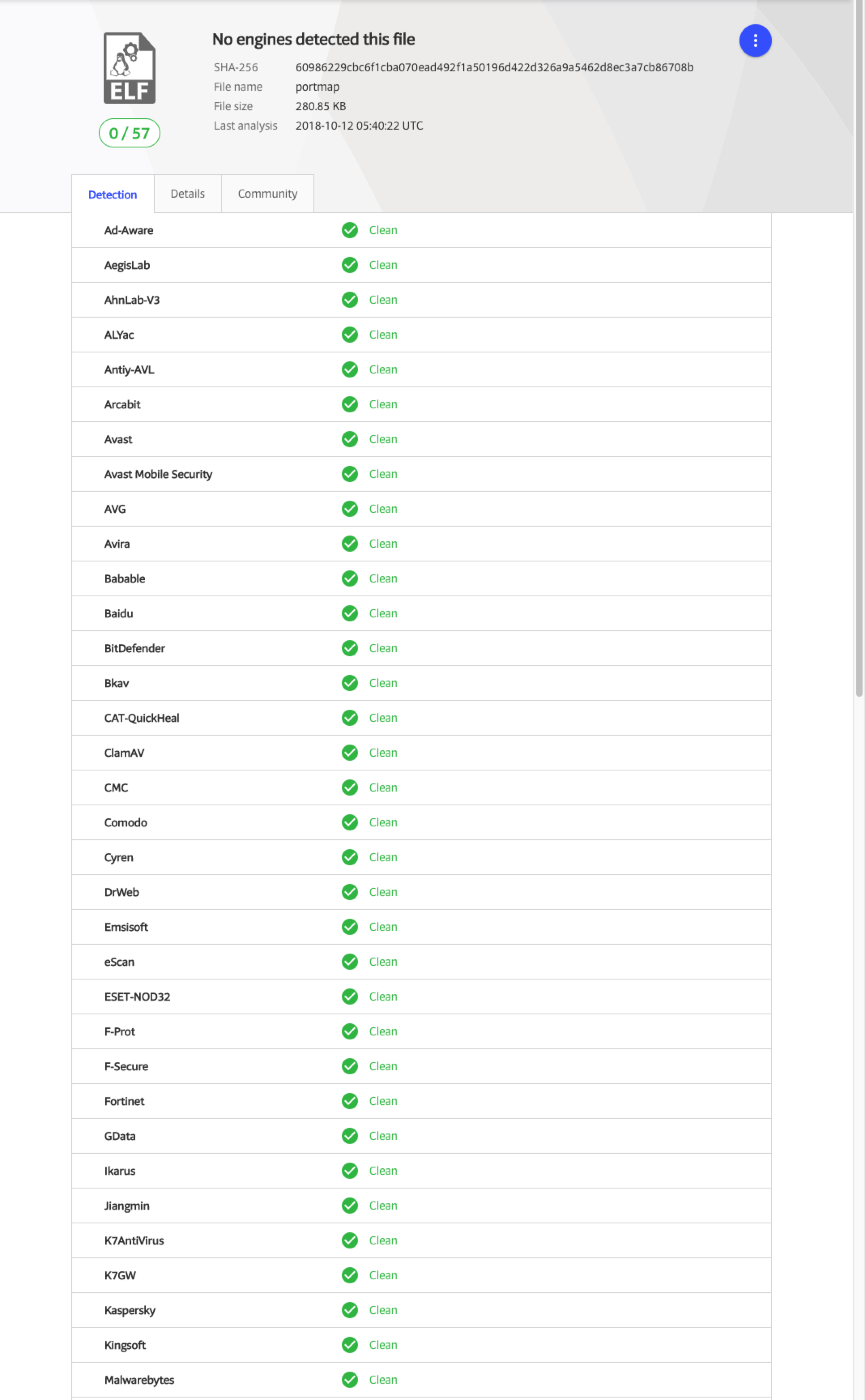
安全软件效果:
包括卡巴斯基、360不会报毒,本来嘛,作为网络工具常用的功能罢了,只不过在渗透中也能成为有用的小工具。