首先做这道题,需要对vm虚拟机有一定的了解,了解虚拟机文件格式、加密虚拟机、挂起虚拟机。
初步分析:
我们看到有三个文件如下图,有个文件后缀是vmem,因此猜测是vmware的内存文件,用volatility工具分析后无果,看到文件名称中提示加密,联想到vm的加密功能,于是我用一个已经有的虚拟机样本做了加密处理,然后又生成了快照加密文件样本和挂起加密文件样本,对照前两个题目原文件特征与样本文件逐一比对后发现,Encryption.bin02文件是vmx全局配置文件的加密形式,Encryption.bin01是vmss快照配置文件的加密形式,而vmem正是加密内存快照本体!我们还注意到Encryption.bin02文件内容后跟随一段二进制内容,它不应该出现在这里,依据二进制文件特征lsilogic与样本比对后发现是vmdk虚拟机磁盘镜像文件。而且Encryption.bin02是残缺的vmx加密文件,需要修复。

文件修复:
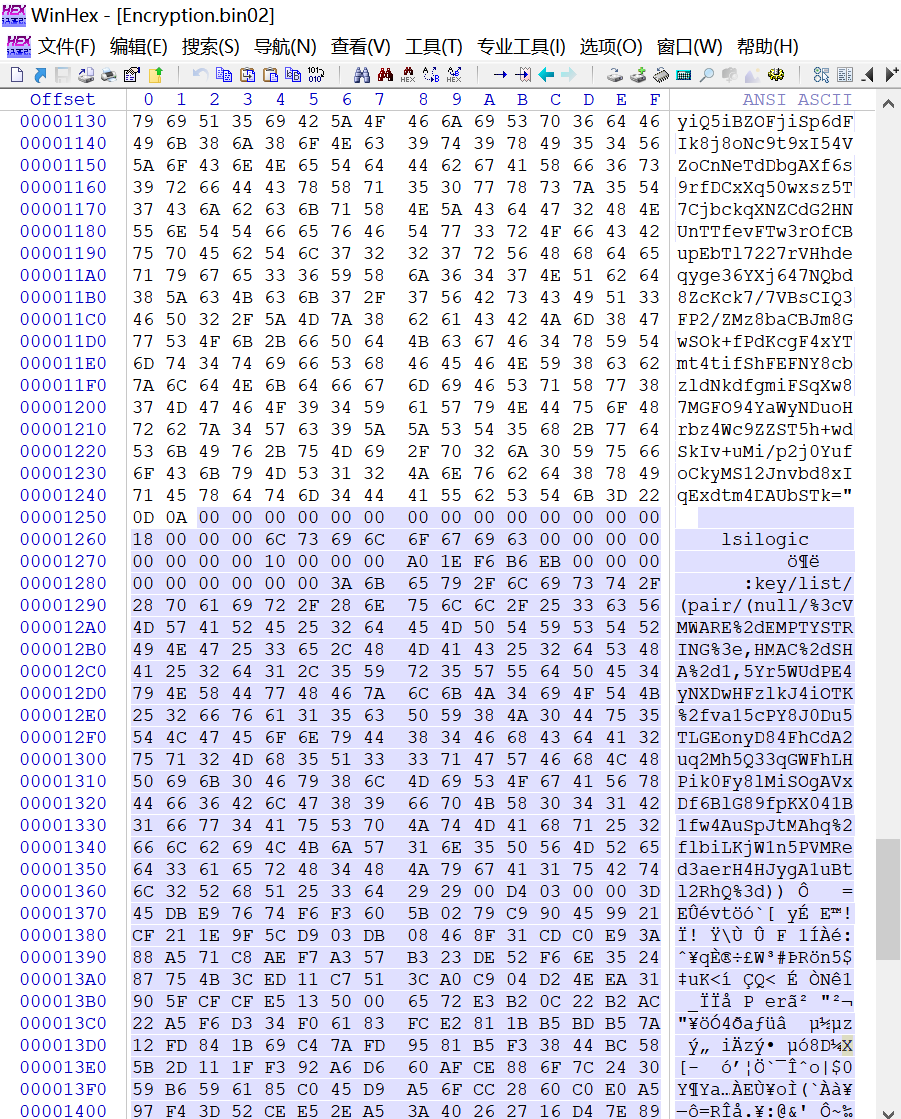
首先使用winhex工具截取文件,将Encryption.bin02文件用winhex打开,在可见字符后的十六进制0D0A处的后面截断,将截断数据保存到新文件中命名为mem_secret.vmdk后面要用到,截断的位置如下图
然后修复缺失的vmx文件
.encoding = "GBK" displayName = "vm" encryption.keySafe = "vmware:key/list/(pair/(phrase/Dg7Se8rqkNI%3d/pass2key%3dPBKDF2%2dHMAC%2dSHA%2d1%3acipher%3dAES%2d256%3arounds%3d10000%3asalt%3d%2b21PdYUqEQd1wdT2AoPEQw%253d%253d,HMAC%2dSHA%2d1,CgKwC5U7lfLjpVohwbpxufC11yU4a0%2byrP08oY0KDDcP1NL%2fRiLojwTz2JnYqm7baAhtgENYUeFUHXwODjSClaJ%2bSRBhKw6UwET6p3AYK8vs4T0cBrvTjYSrs0baLgG7dozcvL5JxA%2fKYJvriz4Mf%2bMmVvE%3d))" encryption.data ="UnIYbS+nasPwdnhtrcPfHLk0VOViI4i1XuasjZgIpp8FsUyeCo6vQ7589Q0ImqTeo8eOV0mJmlrfCKwJeIhE8M4P2vEOmtNvpvCcog+wO7xEg2+YFRdZVz6GDZ7EOl06ZDa1SM+Nt4oKRApQYcOmil0vw9jGJvFT2YYZrInue9luErlFKVCRPSOniNYebiwyEtNOr6Cg2BMYJtxVjJQNoixY8OjEr7Z+Hj/oI7GjYQAuNgh1+FnPf0hxiBT2BVGhyyRzHIl03HXjFQXVHlZE26fsj3Kbjn8m1Eduvw00v1c8Dt1JIp7qFY0lZ9UIMDEdtbVMW/haR84gQ6L9nLdI3JhpCmoF0icdN4pji9XwpmoHqJ5GecpWgdD3mqvuJd9zJSIP8mCCTI9+fpe7pcf8lTpQfppLv1PoLkIZbm91Hkq3sYusrxmuUKX5lIRwHrCpVTquibxDqyoEHjApWg5wvE3y17jOf9xbaMb/5LkYrC9Ql4HwVDzHQ7NyP8xqJXGhcHCRS2PjipxVEJ3fhY2+hxT5cEbvUCp/Yn/YQWXacuwFiMClFY5HN5Yba46lM9/6zWFVDwnHvq2y2URXTCRb/7sd2JhrTe3lvyArErqJZZNw431e7poTBCsGmZipIv6Vbchco/NW2V8JMzFvPfar4YS1oeZsfPrrANBBw3izMPfkwVgOFmk2ZXz8r0YD5Px4a3hxfXzjLD7CJByVxUVfKTPTtiv6es70K5qJ0S8C4aCKQYENR+FL8m4u2w/PC6VjCC3VX2QZzIE5oOgTTA8kCdQ6ONCCyuOJ02Pa8TqrfkGD5gSkdB9t7Xj0IlmBKHLbOYhvimGQrVJuNePzgUH4siz+YfJFRUsFDR6+EWzUCRuJpiMz5VMH3wVWQnWh7OQ4Mvs5UgkLzxaegmOV0HORfJfzsgP2f/IvVKWvInE7VKoRu1JUc20h9Jp8LYVSUTiFKc+guXvia/lqvpgPIxYW9/A3IswiolTWcbfCWEZiMDPCEDLWWFaLfRIuclxeMUDJItK7c/fkud2DpyVOs4APdA2mXiSVmTrY39s48/s/mBT4ytVcyHxD+GD+QLpR4Fqw2Lb/yWhlBCTfjcV80jiOOYR+Wh55raVJ2BN9fAMjK3woTF0L1lPecIjY6xp78eu765vpRoAG/BASFHFf283GrupDL1KAypKcIlRY2+iKRFuX3OvOjgS9aQ/JSP5he2OqnyD3qQsMEjdkMaKEU/oP5x/jNw6JDFbnsxOf4wg7Z+ggozXsWNQmeICe03RFx0CLOuWXxJYQ/hqPCcjMr2uWYJEPZe9TlRgYJYbjRFfG1/owbFO1Kpv81mTpboA3m7qo0/wzs4fUV/ikqU+5DCKXedwMJCXo46/6q2lb6i/V3e9qaIM7AOJ/XSePqb0RMFj6VypBtrnHcIfMuDFMFx+l8zs4tu4jqJyqETLggeglk+DEzoyToLVeQ+YRZu/AGr0Wk0d3+R4zSMR2RAz8mmOJrmw7yJKogHoPzZxaFkx5yRw21d5yPZH4JRabvZu8fQyuNkdk9tiJ5nREHqy8EzuAPP47Gt/NU7MDZh+BEjYs1o7fwjgwD+kpyfLrnktEVhpX3eJXmOiLAuAzRtirqzXzw7HN872iEChnimEnWhOUOwyAYTuSog9BVliezZVvzG2+3EScZ+wlWWICzQSxxURXaMRaQgtNy4dPAHl2gL+ZkQ3bTcrEBZ6PaIj0biq/+LVaYlb82Z1VquKXVtyyF+jiEU3mIpYAIPULWT80f2Sm8RKmnIqmNmJaDqKgQfyBwAUdX6XpzH0yND4SK+7lnwX8nkGy26e7v9mWGDBdY+vOe/AK/jn/gq1HN8EZutt5FpsOtzJT8wnmUTQut3YWNPEdxPNTTzikbaDyJSP4sKcqiEZW/LOLXsf2vEIY+U1OjW6Xo5EKK8BSr7Vj10CugbiBSISLgP4kTQ/KoaJ9RR9raFIH9G0P5nhKsBiQssV5B9bTfBAayzdGHQLMNsEJksr7Nxxsb+2BV+JBoRmkGcIYjaNA+tXRky0PavYf5LcYY88THy045LRJvOX7QJlxAl99pdeZBT+0IOZJpQIeDwSIxuVSw1g7CUuJ/bVdfvTWmtQ2Tvu8cKsdOcNad8zYs92PdnQGS/22CaxLOjkghB8zu8a4KzGrLqkdSabSWedvOUK7bx5cUPJMKpInbBKKsmSCh89JcVJkglKxI9R4nx8p3UW2GRXLb6Ioce7dq3Zh9Cw8g7VyjSzK4MSw7803Pecez8CjXQ0371kmijZnCB942TjSKz3Vg/wwDufrrTDbgQfqruoDFKWR+2H3k9y2dzMHSIOnUZNkgfDXUetEqRfauwXNHANJGBKpfiNeJGhlmb4H7tGUmo6f5uOqiuS1CHZKx3unNngaziwAs8NztDYHISn0h7eP5VGiTOP+RLY002Ob/OMBWKUTDUQy3rcLaMDUQy7ZlEmj6ObcYctQnnTKShfGEfnA0UnzV39v/cTd3KhgOSgvUFfbnbSngTdF0QoX16OnlvVbLgKdZPamI7Lty/6KOLn/U/+Iv3ziZsJo/FTnYYewnBgLZmBnhugbJpVMSUNRumcsesNveM0Zr+XNZ6ceT2DY6F6xWY1/04jYXPc6T0+sDHxQEO2d+1VVyMKP5BRqlbUyVaVj2RAIYmAsTXqGhMvxMJRN8z/z7nhVVmxHvE+/hz8QOnDpNLpkcQRlcR41yc8j3C2loqvITzEqdp9n/c3pr756uaPq6Xfqbf3Ly30Zb9kSoFZfZH+8ZCRpJdzkCt5G3MjTv/L3SkqzDbjOddxmuQLCXyx3bhdvYEfmWXrUMe+bR7qPi48FOhwm40lP6m6/iFAuGxipWtKq10qHvkC8DoPoNZpYPPvNHTINDU+7U2xZ86Qg1nv5addAOaEk40FpMWrpvF10IXl5G7vsMw9NuNE6C6xWeplUUCs6bXxFZM0PSBW0WSKGBE/YUOZQdqVYJq5r9KbiUvtTb7ZyaTy3uM014xTR8DrZDsll6CDaD+fYGj9IH5ViHJ0fqqSPT9GMPV2TnYhpQrysyGMtHDUuAcDkGS9LYk9YGQnRCBTU93sbHoge7yJBVEUzPwc5gPTfZeZUhPEVB6iMPI1I3zbW1Qckvmwbof4D6l0J1YAtUCCSdWqtWjfvIbXGdwJ4NPQpsPbNTeyoSrisWVRMOul+A/pSm8oh1hlWKdHjmaZEYa6o3y04ahSXPfdMvfU5Fon4YKdtrIPCjmRWe0bo5f9gtm8xTUfVV+8MpDfEo6Gyhef0Bywtg6zNBd8F+W8E1NO/5gN+UaJbIxtPRJ5UDwBl2J6d4ET3GU/fbkd+2KLUxkEoZsQOHNnu3R0QHA4ig6ZjYzVzhEkjcMH7Z+N7PP691/Y3BPBd2decJhIeniMyuFd7X8ElPzccpgdwbQXpmB9zxa8TUZSj6v/CNp/HTEjIOu7ibWK43iRZ68RH0OmBGgZ/tdSPCoNj5oySivoohXjXlFM9siBmsqtqTIWIcFDXx9K8OAD8zjfbLtDRQQadO8SKzvmO6d/Fqq4WtrXewkB6T/VZrsS5gudA6G9c45qed/4OXChKtIa6bLmwkmEz0ChsMnHK3xPxAxtBTcNEw/ztDFf2GhI27EN3F7SsfU7EKqCS4DvJGnTbiK8YpxDkcTPlEZ4TC5jeaU1YcM8Jsk7vFvScQkie/dy5wjIBqUEe8V877dek/c2H7aXHrOdfd6VE+5ZQ2ypUnCHX+JTpwkbjMT9xliMnZZ/po5jPZP4NTbJq13EJDzkfSxasmJOMmleDFotme4dux8UC6zm/sL+uc2aAY3xiEF+TJkQHsdx2igiXuXIdbD0WGhlwcrtrodJUjGILeLMHu1U8ZZYWbKsel4PyaBOXiZiLAksYOyXSuryNmCm9lkkfWsXO/bRhqvOp/tPb5nAZpbrm/wPROmQEUajfhXBEvwa8cl4X6wOI783/CxrqleHacyhLJb3lABwcR6XjQlNVuOoOWYVmxyVQWfcQxhh8cg0jdMy6q43N4O2b1dbbDTHpoKMdKCqM1Lefj2me77gdSijuR63y4bH4Zwd6Hqsq8WfDcJFGrBmNnIuwppni2MjB0yiQ5iBZOFjiSp6dFIk8j8oNc9t9xI54VZoCnNeTdDbgAXf6s9rfDCxXq50wxsz5T7CjbckqXNZCdG2HNUnTTfevFTw3rOfCBupEbTl7227rVHhdeqyge36YXj647NQbd8ZcKck7/7VBsCIQ3FP2/ZMz8baCBJm8GwSOk+fPdKcgF4xYTmt4tifShFEFNY8cbzldNkdfgmiFSqXw87MGFO94YaWyNDuoHrbz4Wc9ZZST5h+wdSkIv+uMi/p2j0YufoCkyMS12Jnvbd8xIqExdtm4DAUbSTk="
重命名Encryption.bin02为mem_secret.vmx
重命名Encryption.bin01为mem_secret-963a4663.vmss
爆破密码:
双击vmx打开,此时提示输入密码,我们不知道密码是多少,爆破密码
python3 pyvmx-cracker.py -v mem_secret.vmx -d wordlist. txt
密码 1q2w3e4r
修复vmdk:
再次打开vmx,提示缺少vmdk虚拟磁盘文件,我们新建一个虚拟机,虚拟机配置依照已知的信息配置,未知信息默认即可。配置vmdk为单文件并重命名为mem_secret.vmdk。下面截图是我配置好的截图。注意无需挂载win10系统安装镜像。
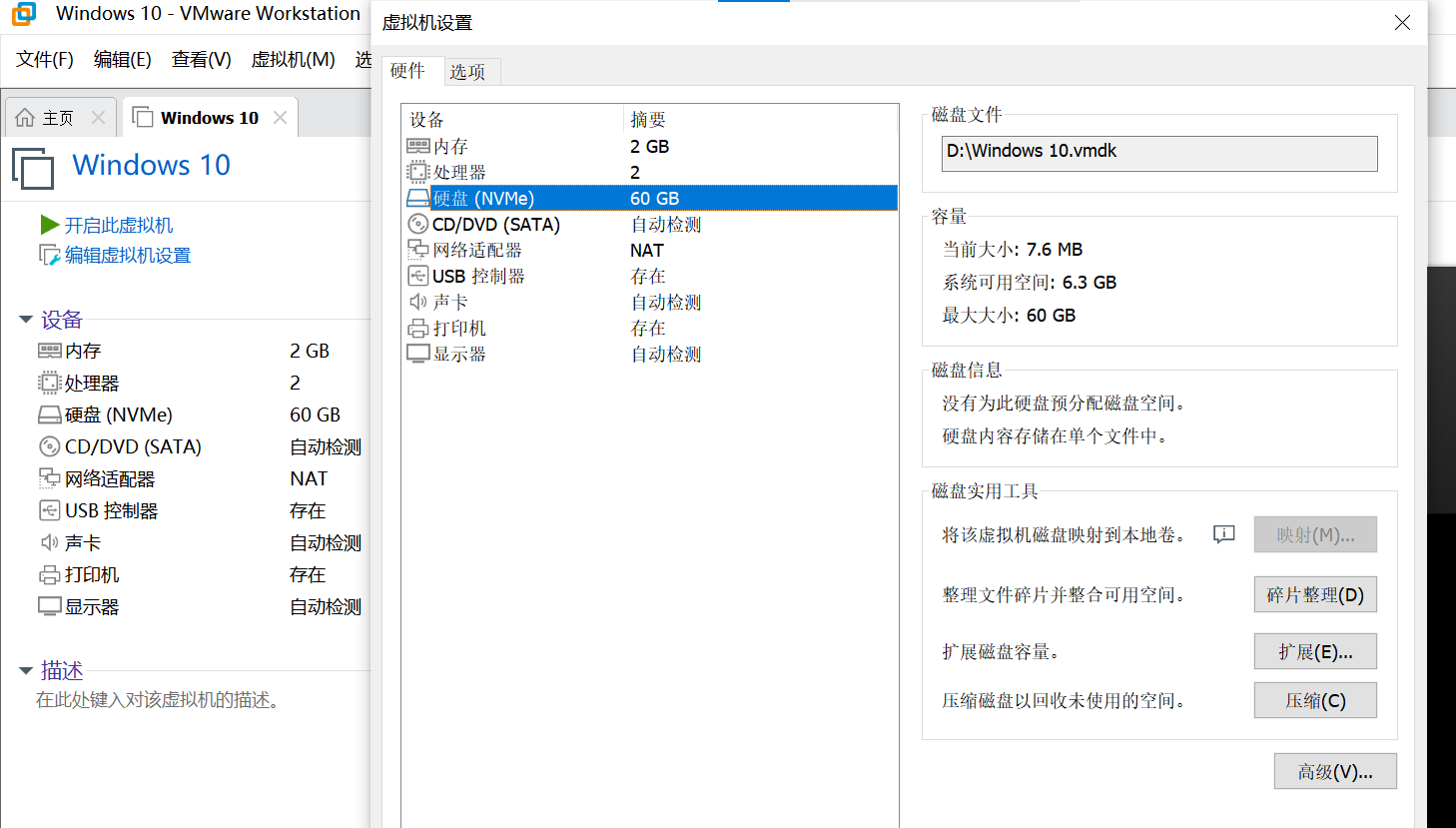
配置好后用相同密码加密虚拟机。将mem_secret.vmdk与上一步文件修复中的mem_secret.vmdk比对发现,上一步中的mem_secret.vmdk只是我们刚刚新建的vmdk的一部分,我们用winhex工具将旧的部分替换新的部分,下图是新建的vmdk,粘贴点在下图选中的位置,在winhex右键编辑--》剪贴板数据--》写入,替换当前位置的数据。
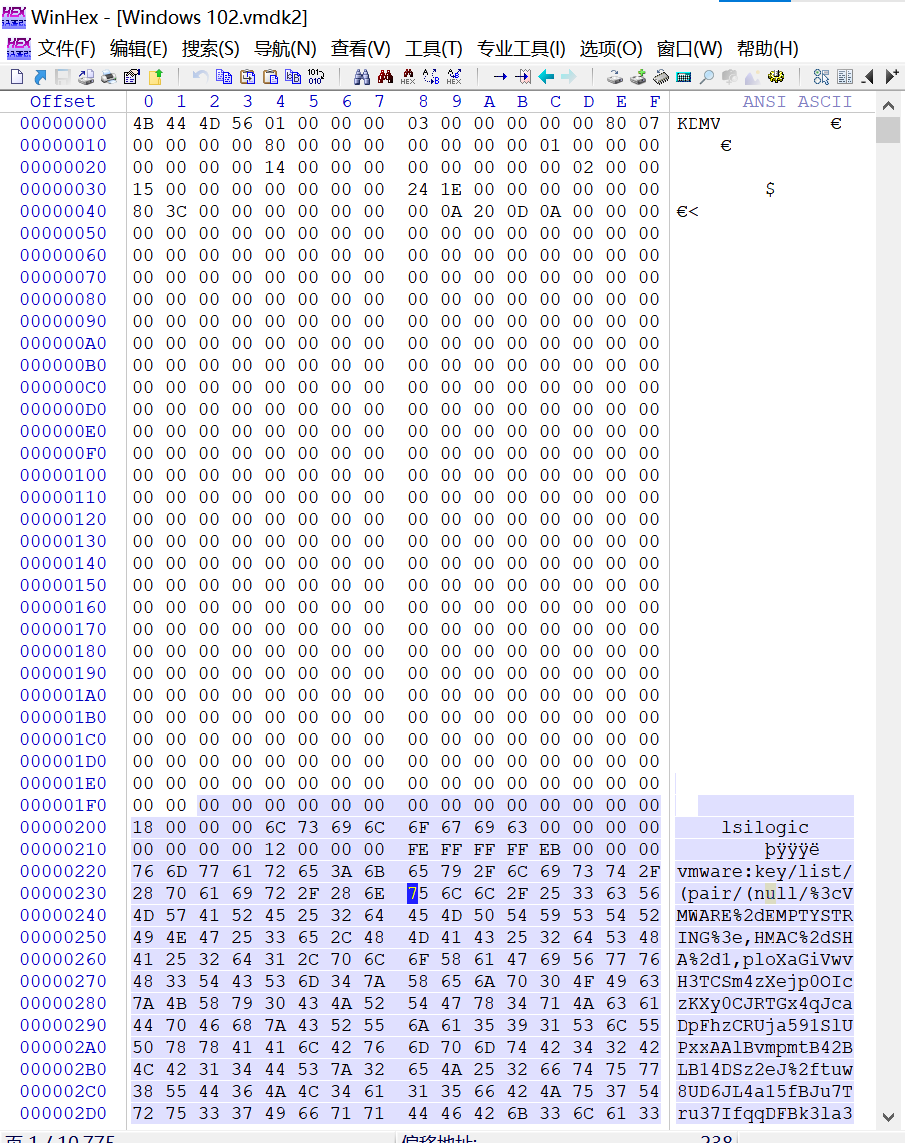
替换后注意还要修改红色部分
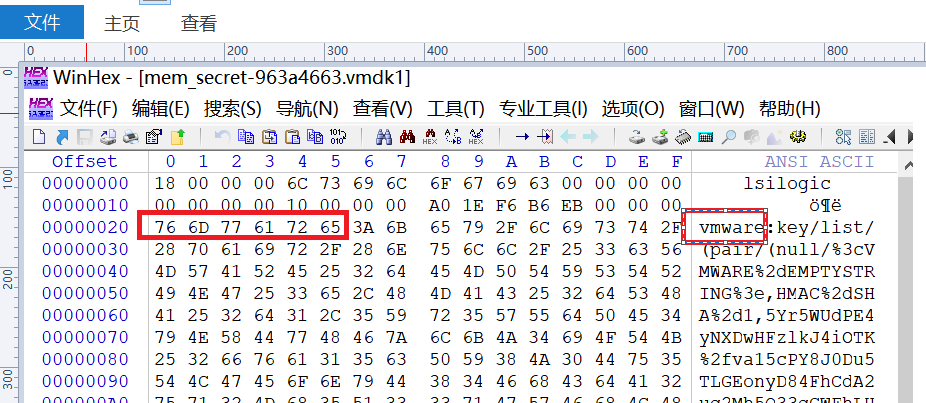
此时设置去除密码
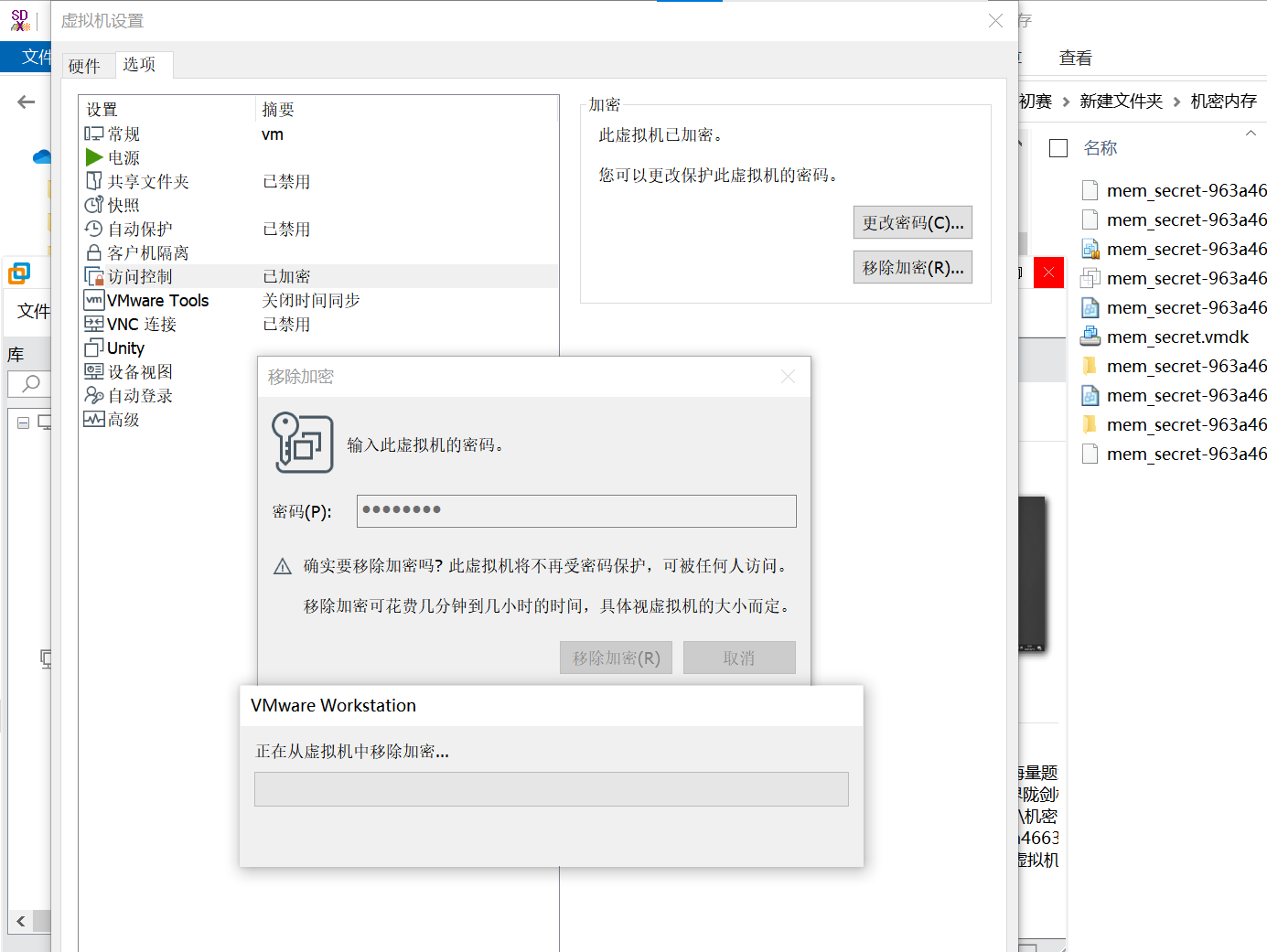
大功告成。
直接分析解密好的vmem文件,
注意注意注意这里有个坑,使用最新主线版本的Volatility,不要使用归档版本的Volatility(例如2.6.1),因为归档版本不支持这个win10
下载链接 https://github.com/volatilityfoundation/volatility
获取系统版本 python2 vol.py -f '/root/Documents/mem_secret-963a4663.vmem' imageinfo ,得知系统是Win10x64_18362
导出注册表 python2 vol.py -f mem_secret-963a4663.vmem --profile=Win10x64_18362 dumpregistry -D ./
使用MiTeC Windows Registry Recovery工具解析注册表,查看主机名为DESKTOP-4N21ET2,版本号为6.3.18363
导出文件 python3 vol.py -f mem_secret-963a4663.vmem windows.filescan -D ./
搜索desktop,分析后得知用户名为Ado
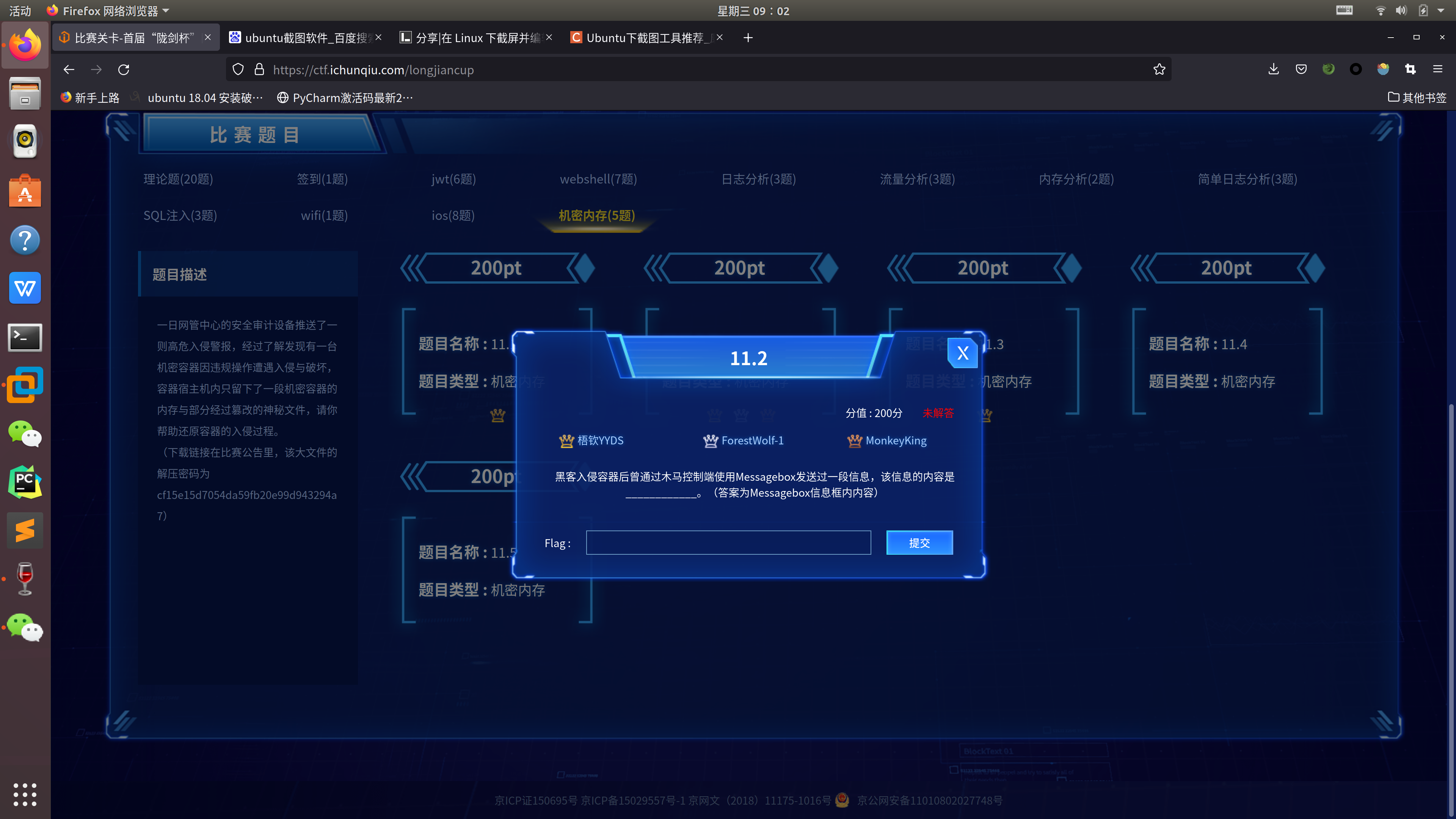
挂起状态虚拟机中显示的内容就是答案:Best_hacker
我们在vmem中直接搜索关键字 @ 、username 、password 就可以找到答案,steam注册邮箱为john@uuf.me ,用户名为jock_you1,密码为,jock.2021
查看进程 python2 vol.py -f mem_secret-963a4663.vmem --profile=Win10x64_18362 pstree
查看网络 python2 vol.py -f mem_secret-963a4663.vmem --profile=Win10x64_18362 netscan
马程序steam.exe,ip为192.168.241.147,端口号为8808

python2 vol.py -f mem_secret-963a4663.vmem --profile=Win10x64_18362 userassist
python2 vol.py -f mem_secret-963a4663.vmem --profile=Win10x64_18362 filescan -D ./
桌面发现可疑文件 Wywz.exe,时间 2021-09-10 21:10:13 UTC+8(注意时区转换)