SAA
Overview
-
A: hostname to IPv4
- AAAA: hostname to IPv6
- CNAME: hostname to hostname
- Alias: hostname to AWS resouce

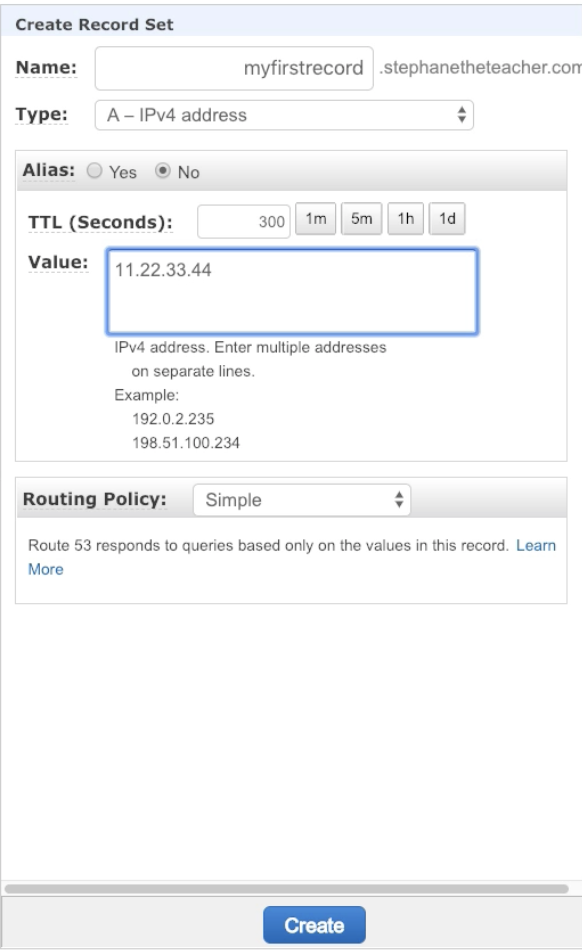
Create a Record point to a IP that you control
Testing against: can use nslookup / dig

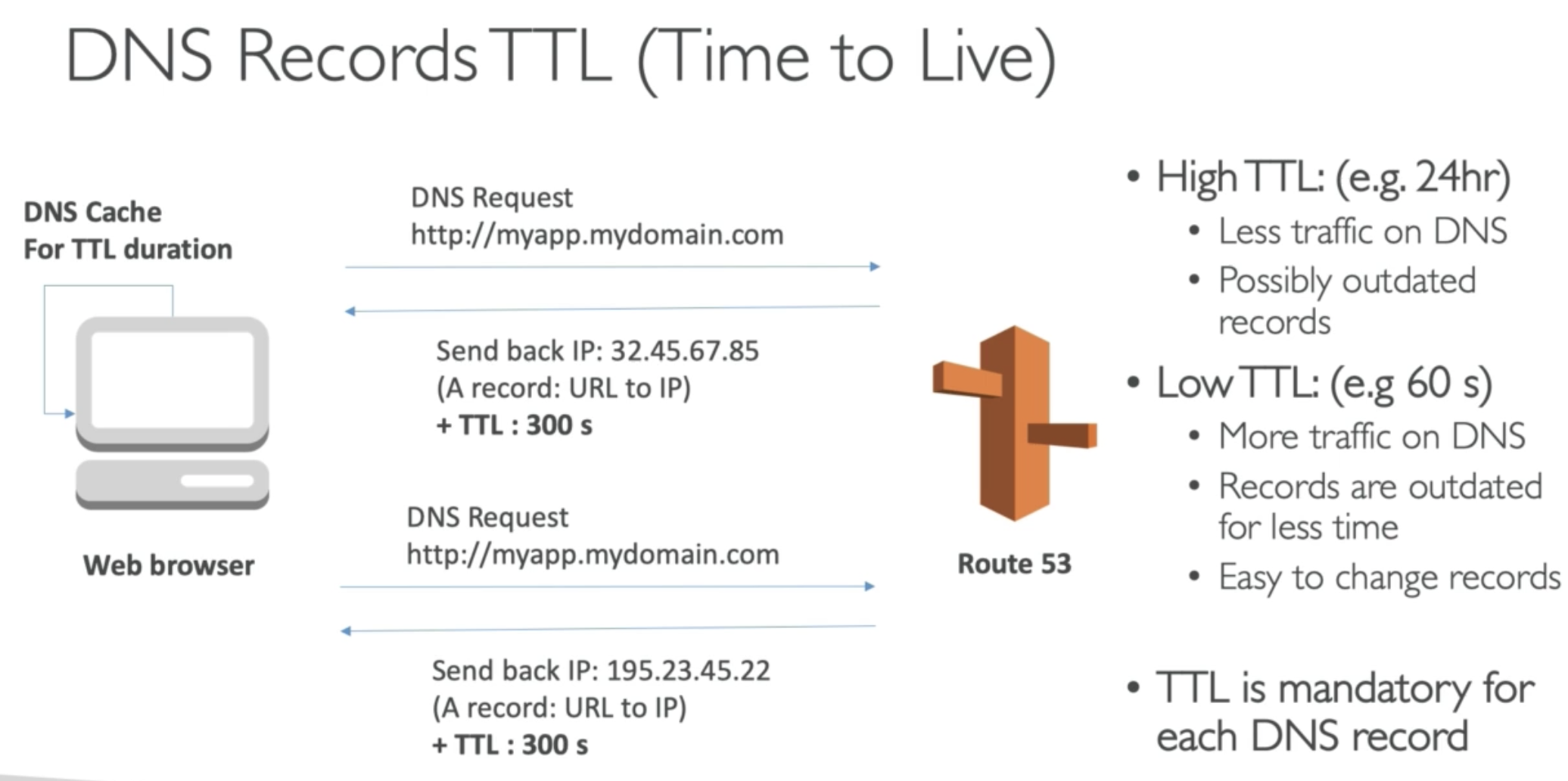
- Web broswer will cache the DNS response so that request will hit less time to DNS
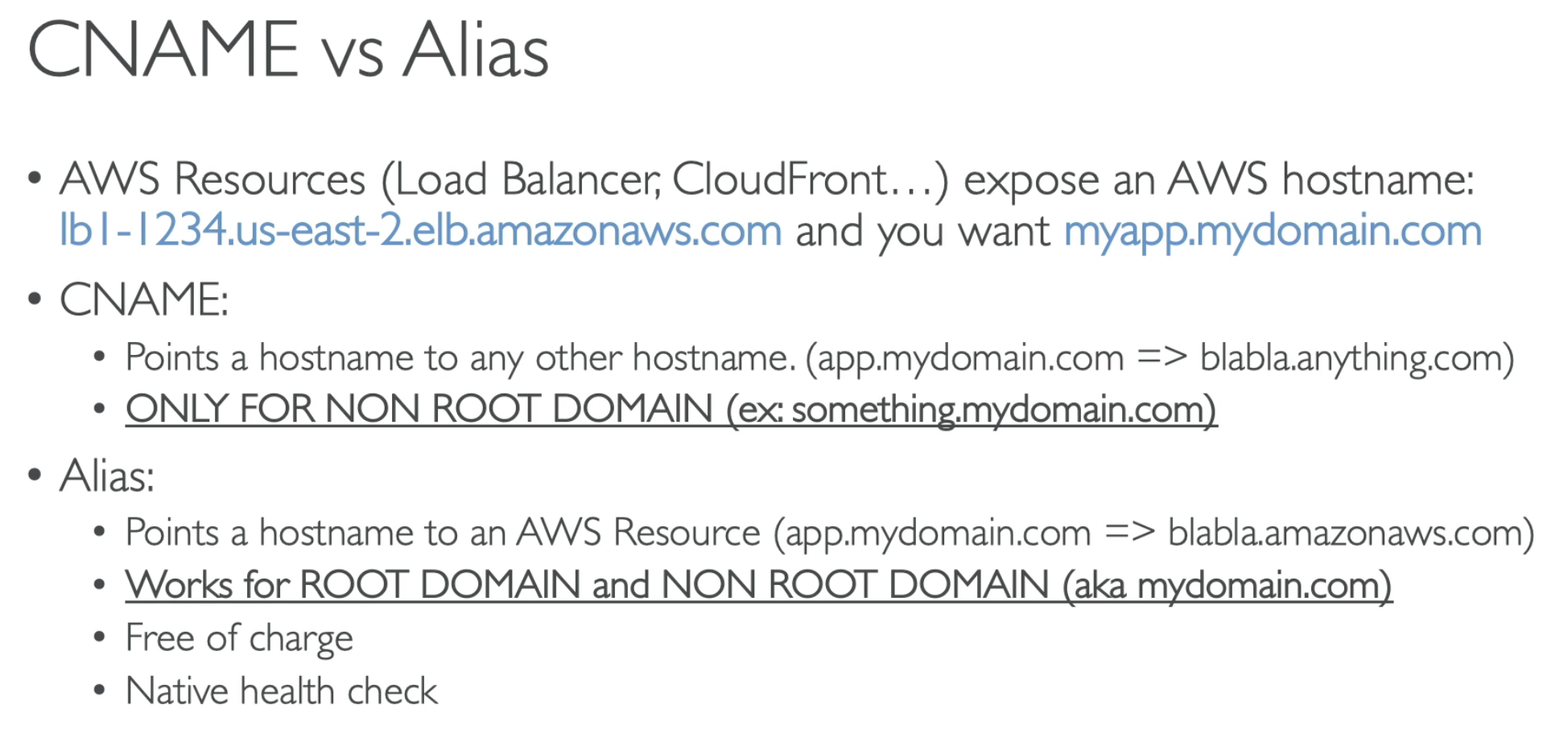
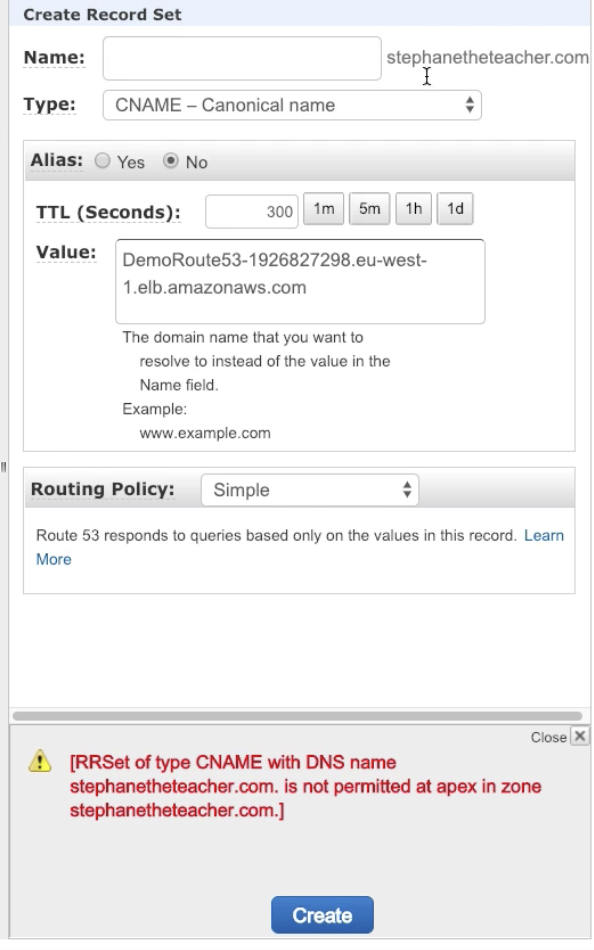
- CNAME has to be something.yourcompany.com, NON Root Domain, in this case, root domain is yourcompany.com
- Alias: has to point to aws resource. Can ref to non or root domain, so work both for yourcompany.cpm and something.yourcompany.com
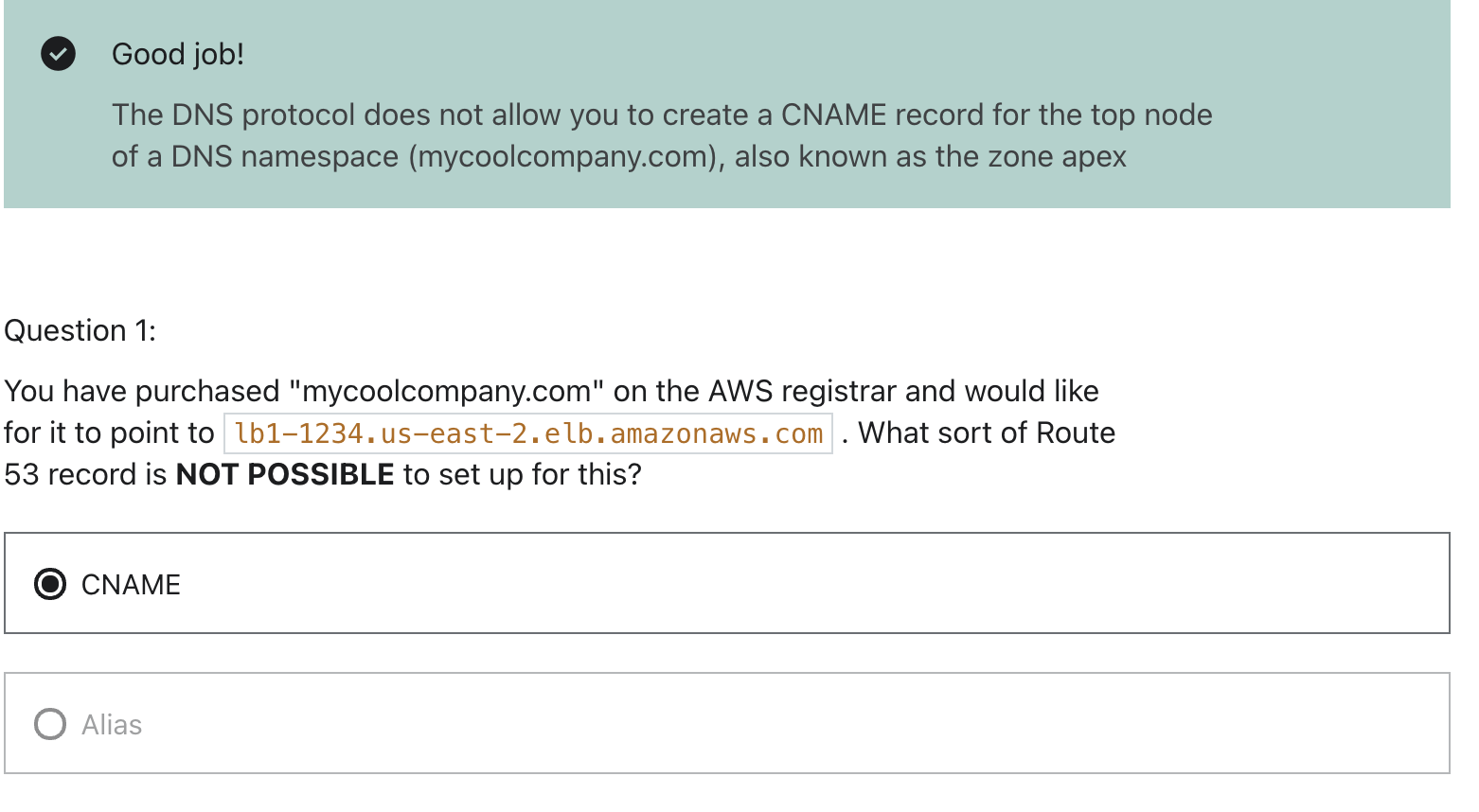
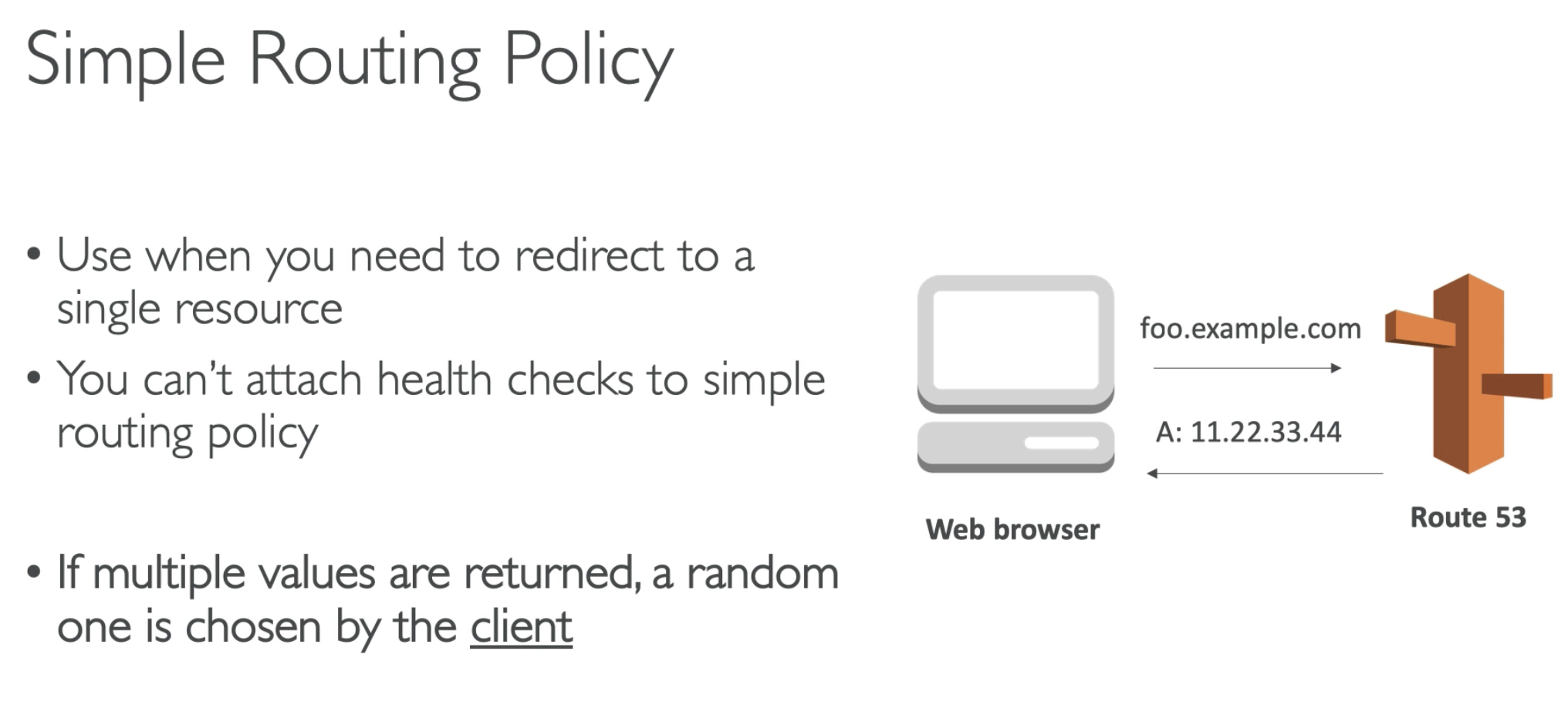

If you give to IP address, browser will choose which one to go. It is called Client side load balancing.
Affected by TTL. For 60second, it always goes to one IP address.
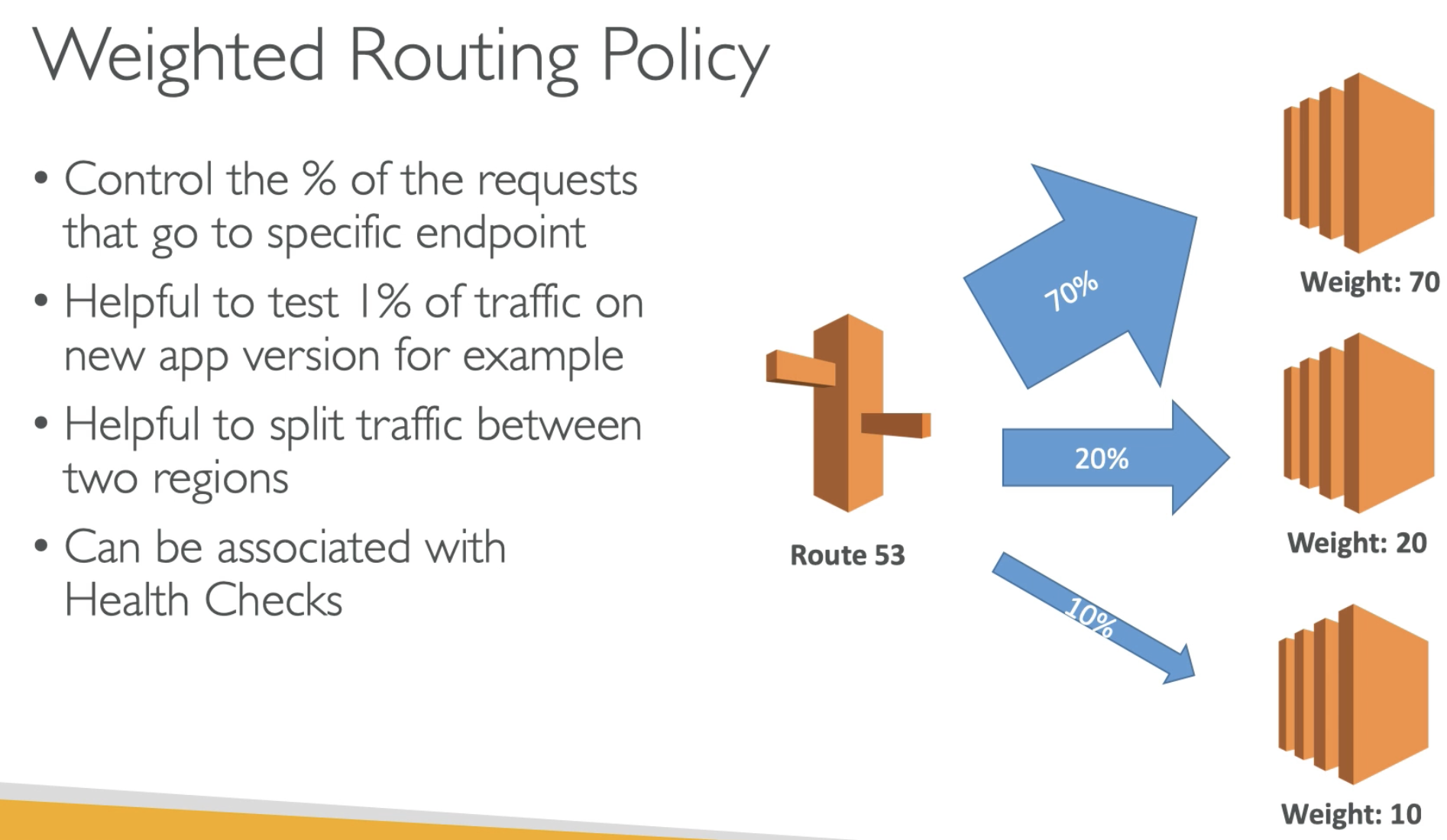
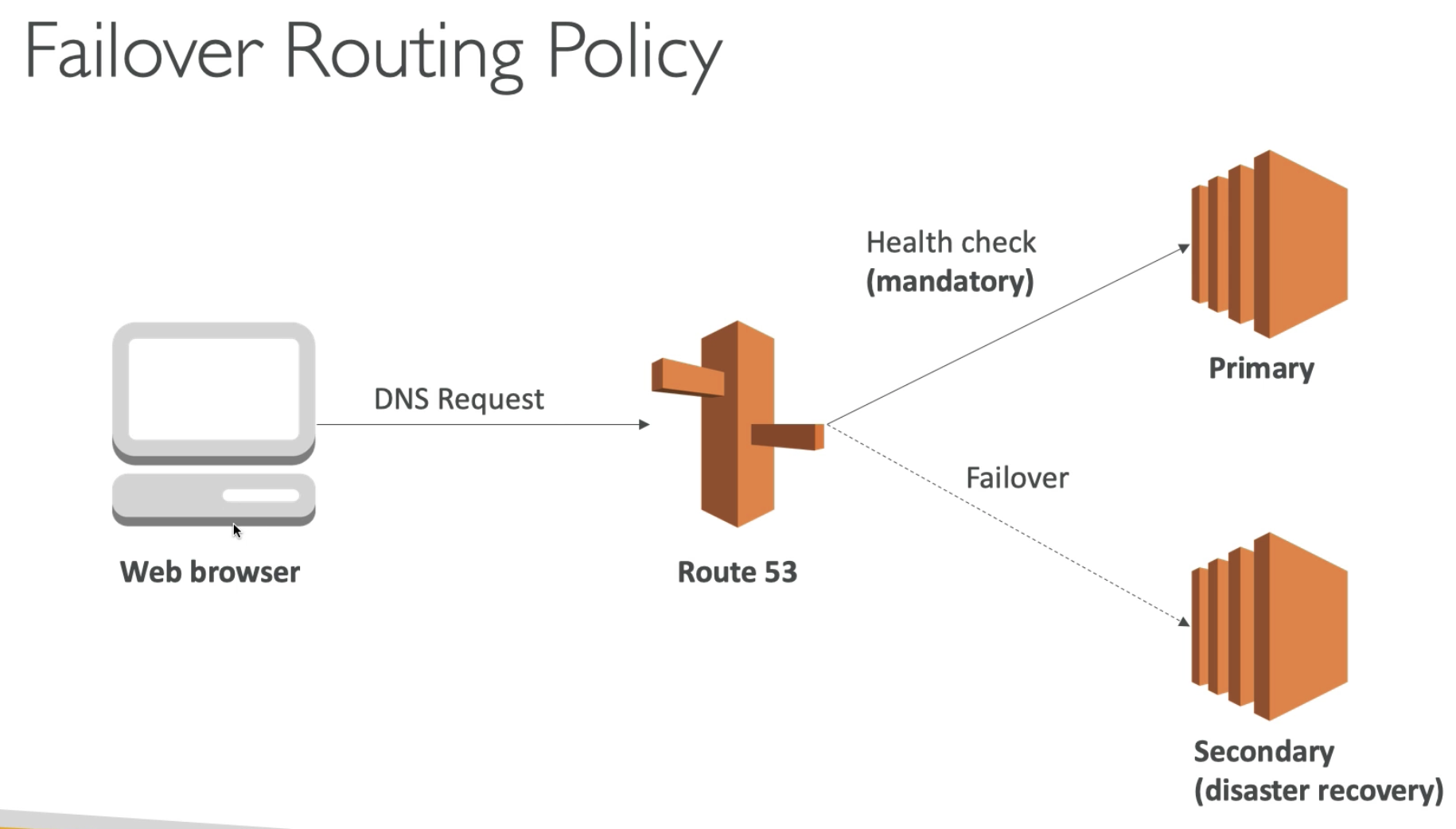
- Has a failover capability if you enable health checks

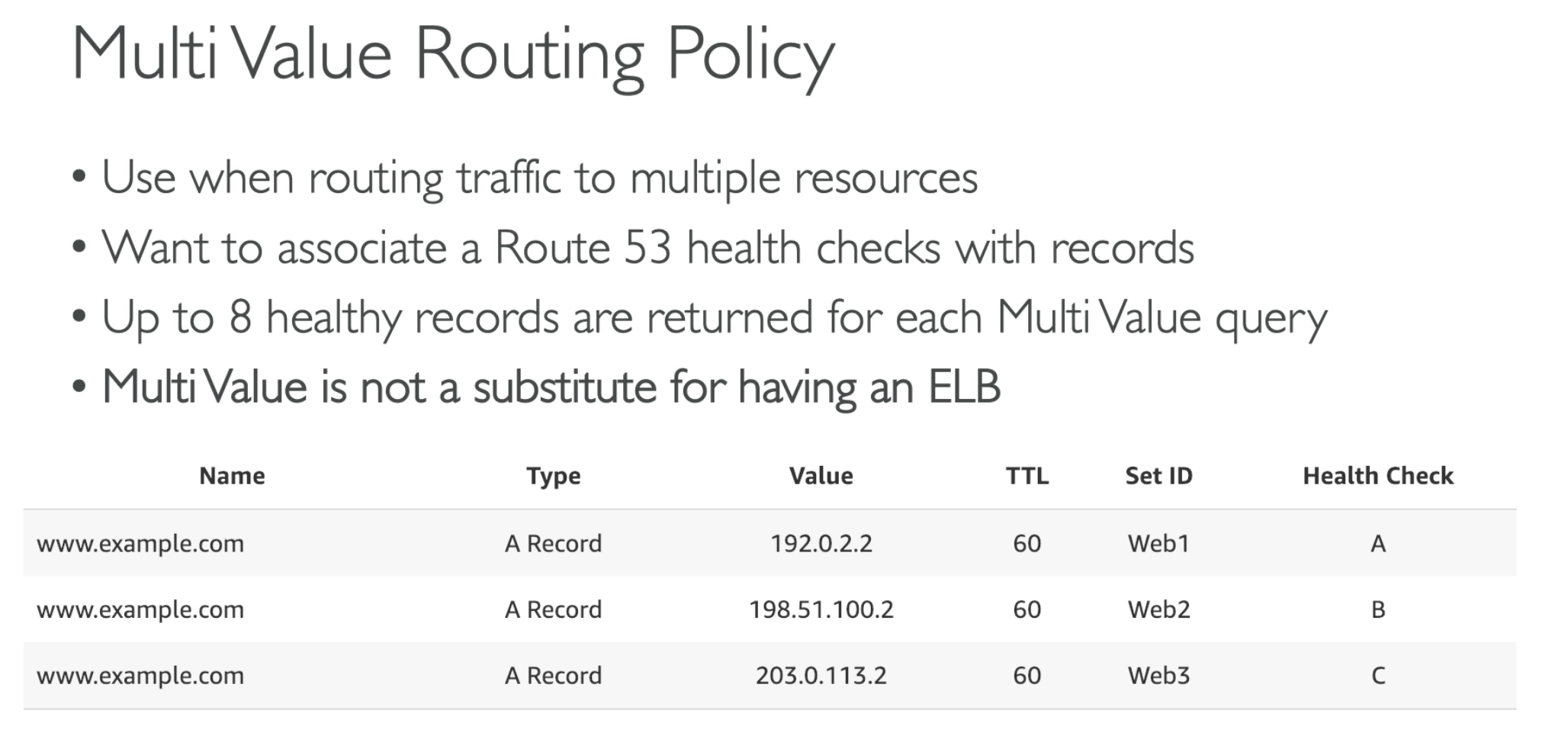
Return multi IP for client side to choose, a full tolerance solution

GoDaddy is a public DNS service, private host zone is only for internal AWS service.
SAP
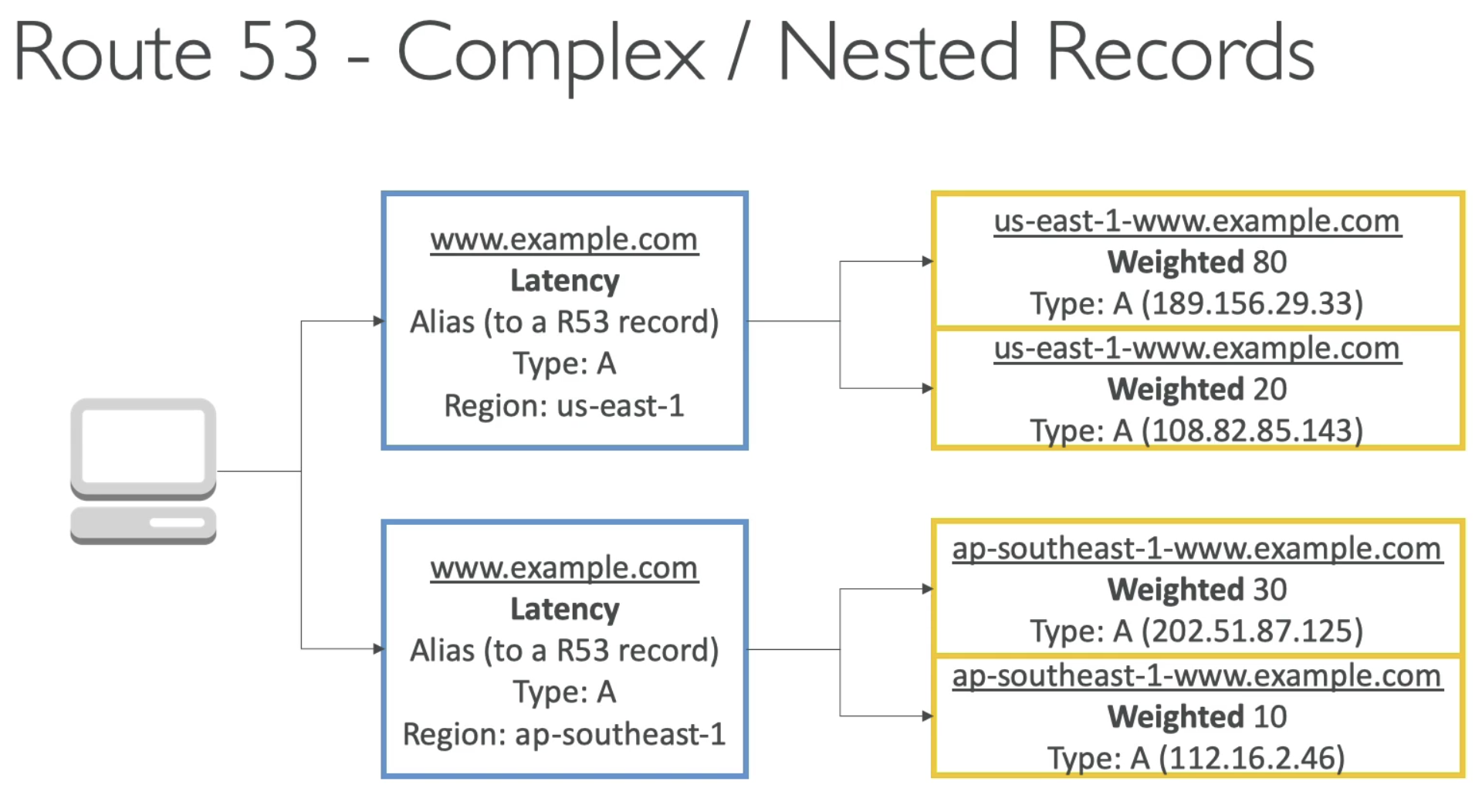
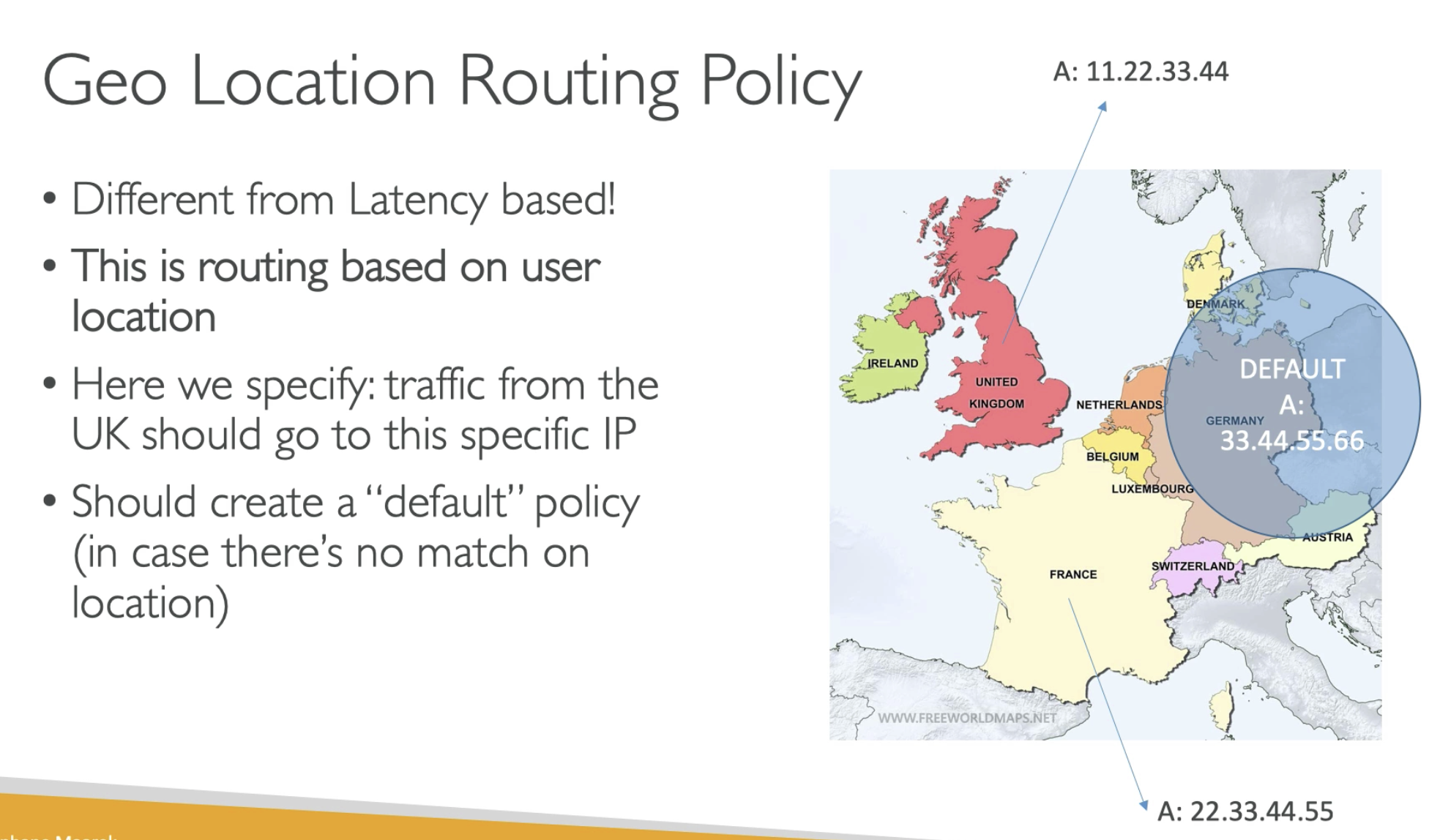
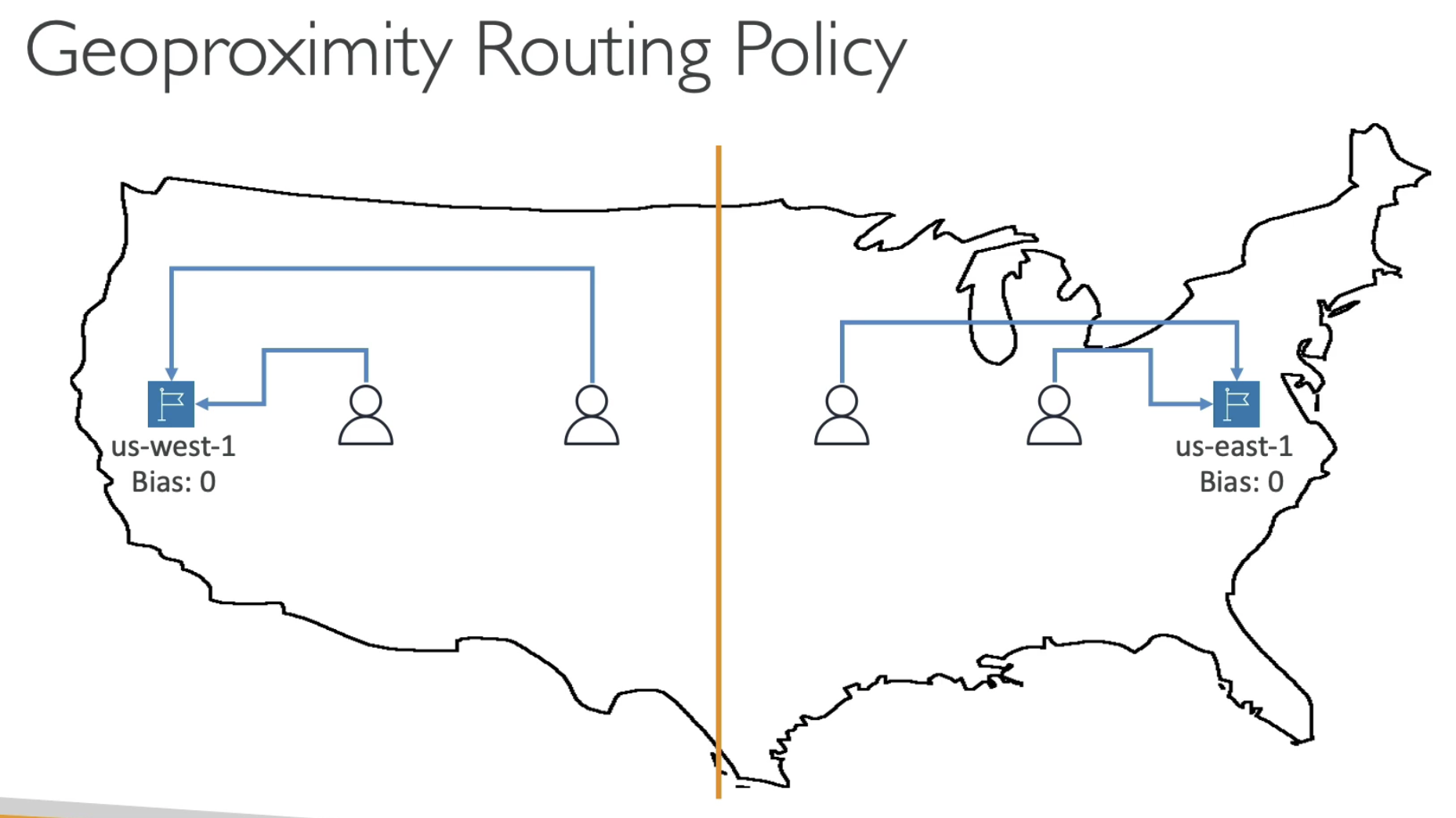
- You can combine route policy
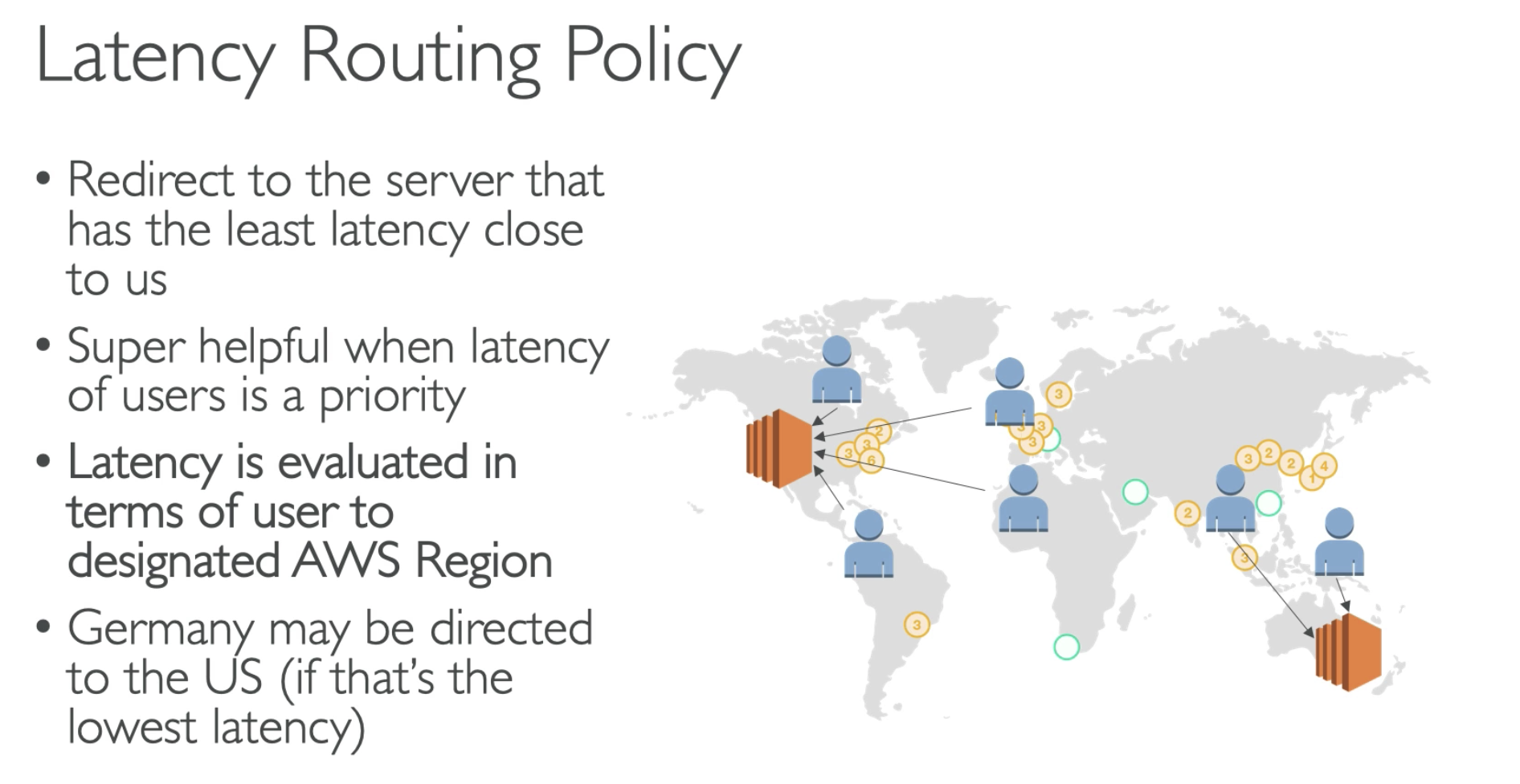
- For example, you ca use Latency as Phrase 1 policy, so the user near US, will be sent to us-east-1 region
- users are close to Asia will be sent to ap-sourth-1 region
- Then in each Latency group, can split traffic by using weighted policy to different IPs.
Good to Know
Private DNS
- Can use Route 53 for internal private DNS
- Must enable the VPC settings enableDnsHostNames and enableDnsSupport
DNSSEC (protect against Man in the Middle attack)
- Amazon Route 53 supports DNSSEC for domain registration
- Route 53 supports DNSSEC for DNS service as of Dec 2020 (using KMS)
- You can also run a custom DNS server on Amazon EC2 for example (Bind is the most popular, dnsmasq, KnotDNS, PowerDNS).
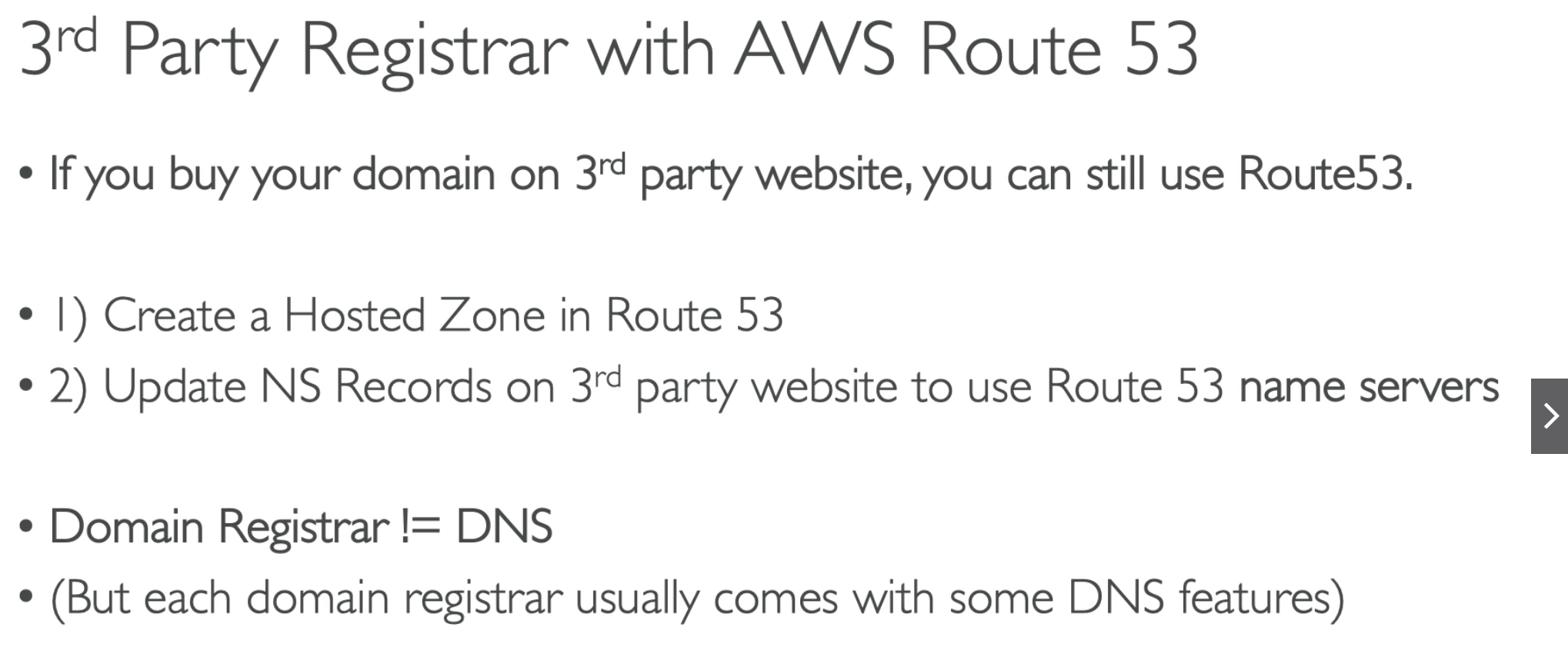
3rd Party registrar
- You can buy the domain out of AWS and use Route 53 as your DNS provider
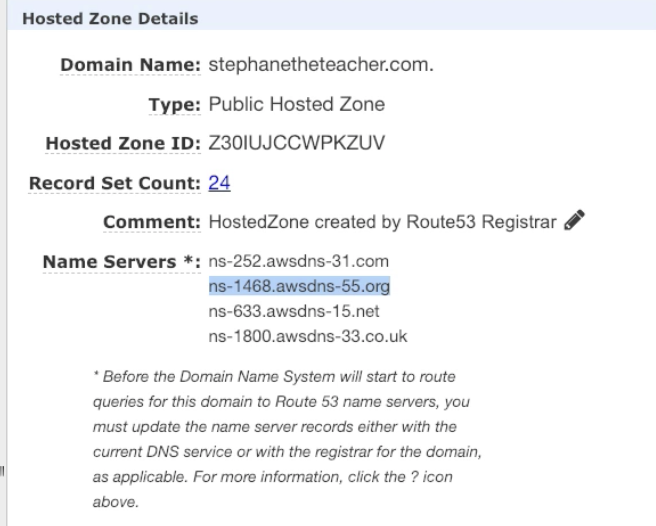
- Update the NS records on the 3rd party register
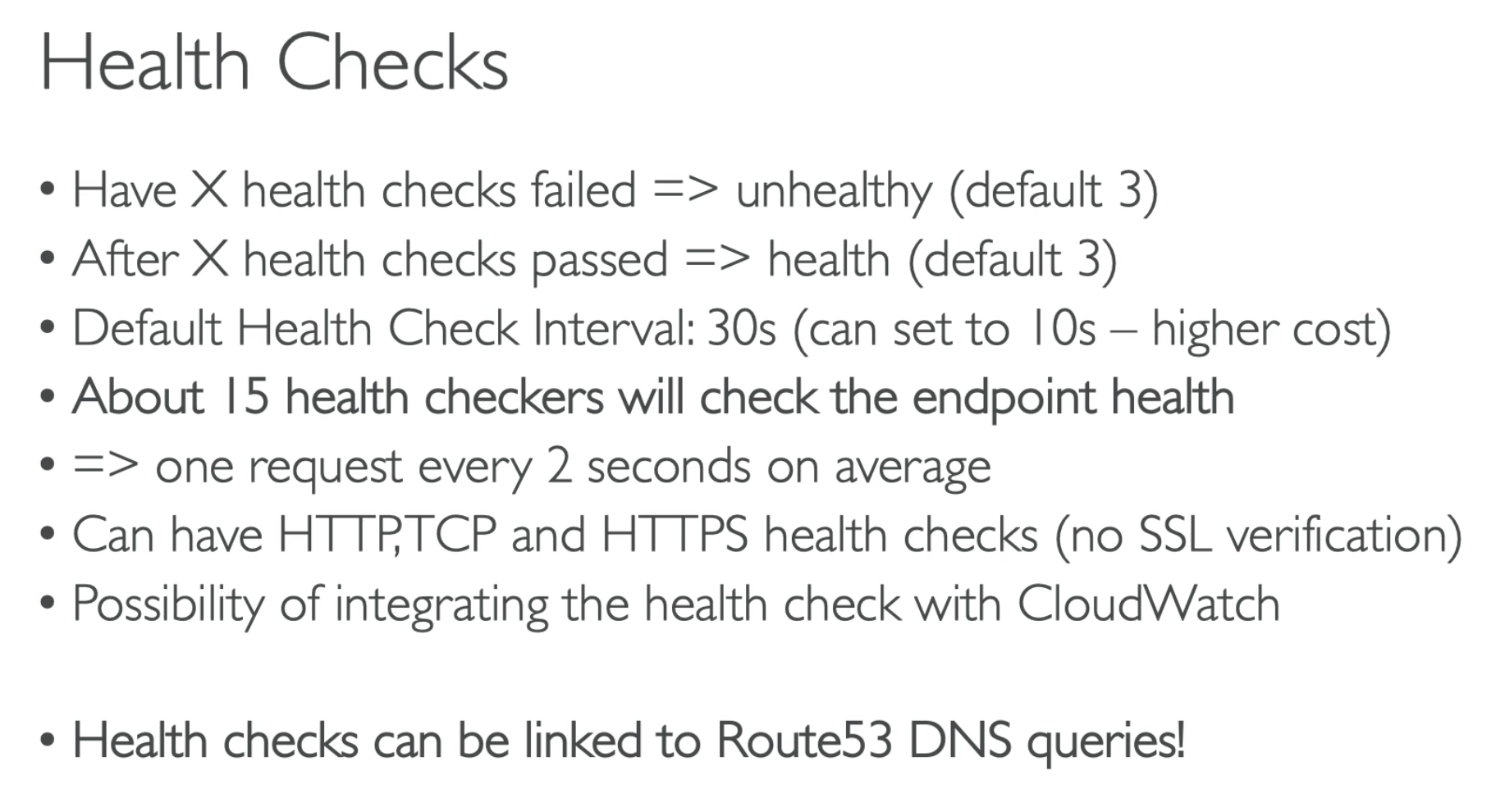
Health Checks
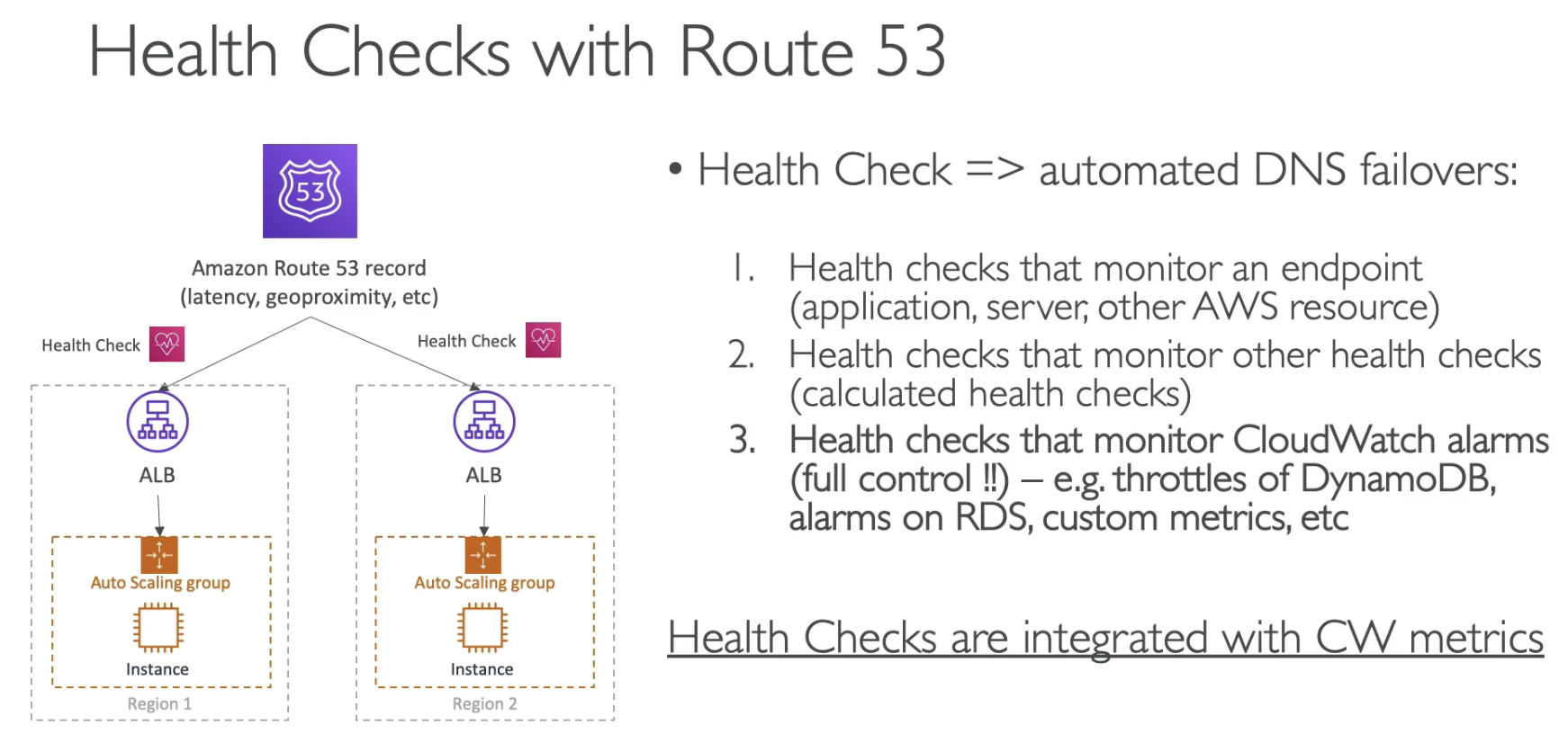
- Health Checks can be setup to pass/fail based on text in the first 5120 bytes of the response
- Health Checks pass only with the 2xx and 3xx status response
- Calculated health checks
- Create separate individual health checks
- Specify how many of the health check need to pass to make the parent pass
- Health Checks can trigger CloudWatch Alarms
Health Checks - Private Hosted Zones
- Route 53 health checkers are outside the VPC
- They CANNOT access private endpoints (private VPC or on-premise resource)
Options:
- To check a resource within a VPC, you must assign a public IP address (But if resouce is in private subnet, then this option is not possible)
- You can configure the health checker to check the health of an external resource the instance relies on, for example a database server.
- You can create a CloudWatch metric and assoicate an alarm. You then create a health check that checks the alarm itself.

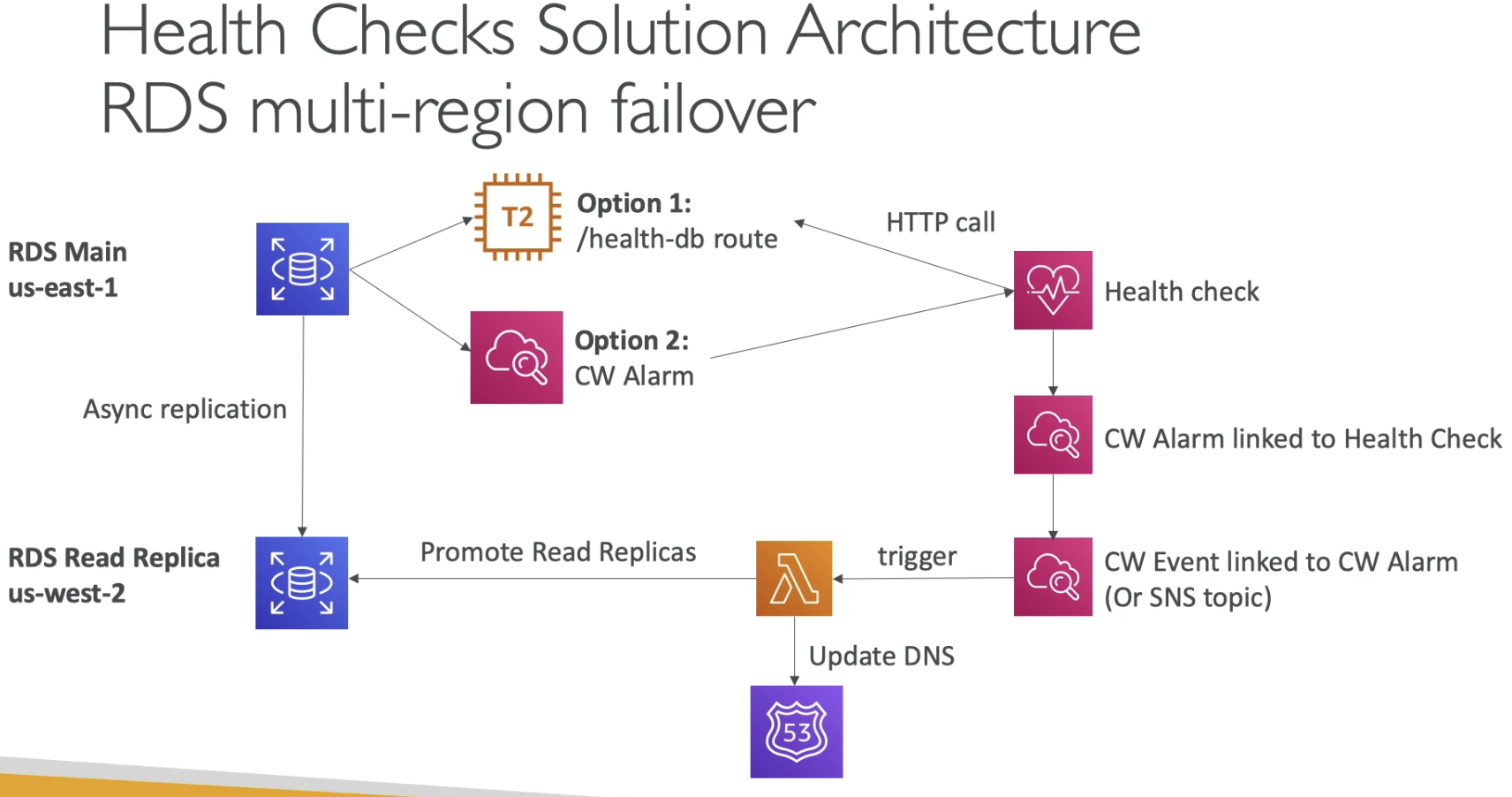
Health check Solution Architecture RDS multi-region failover
- If we have two RDS databases in two different regions
- We use Async replication between two RDS databases
- We want to achieve automatic failover for RDS
For Health Check, we can we two options:
- EC2 instances call /health-db endpoint to do health check
- Use CW Alarm to do health check
Then got unhealth result, what we can do is:
- CW alarm linked to Health check
- CW Event linked to CW Alaram (or SNS topic)
- Then trigger Lambda
- Update DNS record in Route 53 to point to read replica
- Send a request to Promote Read Replicas as Primary database
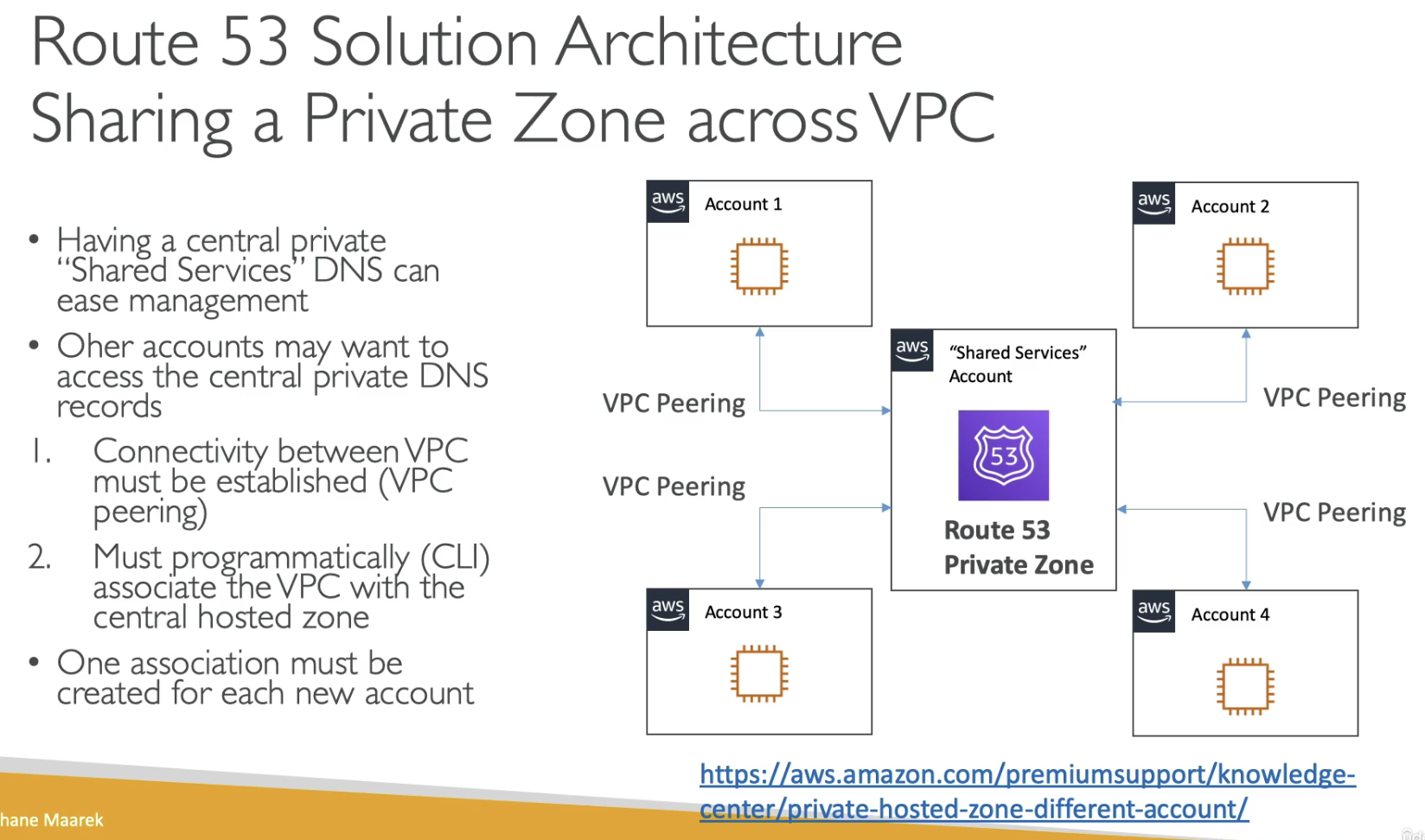
https://aws.amazon.com/premiumsupport/knowledge-center/private-hosted-zone-different-account/
Geoloaction is restrict access by GEO Loaction
Latency is minimize network time which has a failover is enable health check